Cyber Terrorism Attacks Powerpoint Presentation Slides
Cyber Terrorism is the fusion of cyberspace with terrorism; it refers to illegal assaults and threats of attacks on computer networks. Check out our competently designed Cyber Terrorism Attacks template that is of significant assistance to learning about the problems faced by the company and the current scenario of cyber terrorism around the globe. In this presentation, we have incorporated the elements of cyber terrorism, which include types and forms of cyber terrorism and the tools misused. In addition, PPT shows preventive measures to protect the company from tools of cyber terrorism. Furthermore, it includes strategies to mitigate cyber terrorism. Moreover, this presentation represents an assessment matrix to determine the financial impacts of cyber terrorist attacks on businesses and the companys implementation of cyber security measures. Further, the template caters to a checklist to deal with cyber terrorism in the industry, a timeline, and a roadmap to monitor the implementation process. Lastly, the Delivery Network deck comprises a 30-60-90-day plan to implement cyber security in the business. Customize our 100 percent editable cybersecurity ppt template now.
Cyber Terrorism is the fusion of cyberspace with terrorism; it refers to illegal assaults and threats of attacks on compute..
- Google Slides is a new FREE Presentation software from Google.
- All our content is 100% compatible with Google Slides.
- Just download our designs, and upload them to Google Slides and they will work automatically.
- Amaze your audience with SlideTeam and Google Slides.
-
Want Changes to This PPT Slide? Check out our Presentation Design Services
- WideScreen Aspect ratio is becoming a very popular format. When you download this product, the downloaded ZIP will contain this product in both standard and widescreen format.
-

- Some older products that we have may only be in standard format, but they can easily be converted to widescreen.
- To do this, please open the SlideTeam product in Powerpoint, and go to
- Design ( On the top bar) -> Page Setup -> and select "On-screen Show (16:9)” in the drop down for "Slides Sized for".
- The slide or theme will change to widescreen, and all graphics will adjust automatically. You can similarly convert our content to any other desired screen aspect ratio.
Compatible With Google Slides

Get This In WideScreen
You must be logged in to download this presentation.
PowerPoint presentation slides
Enthrall your audience with this Cyber Terrorism Attacks Powerpoint Presentation Slides. Increase your presentation threshold by deploying this well-crafted template. It acts as a great communication tool due to its well-researched content. It also contains stylized icons, graphics, visuals etc, which make it an immediate attention-grabber. Comprising seventy one slides, this complete deck is all you need to get noticed. All the slides and their content can be altered to suit your unique business setting. Not only that, other components and graphics can also be modified to add personal touches to this prefabricated set.
People who downloaded this PowerPoint presentation also viewed the following :
Content of this Powerpoint Presentation
Slide 1: This slide introduces Cyber Terrorism Attacks. State Your Company Name and begin.
Slide 2: This slide shows Agenda for Cyber Terrorism.
Slide 3: This slide presents Table of Content for the presentation.
Slide 4: This is another slide continuing Table of Content for the presentation.
Slide 5: This slide represents title for topics that are to be covered next in the template.
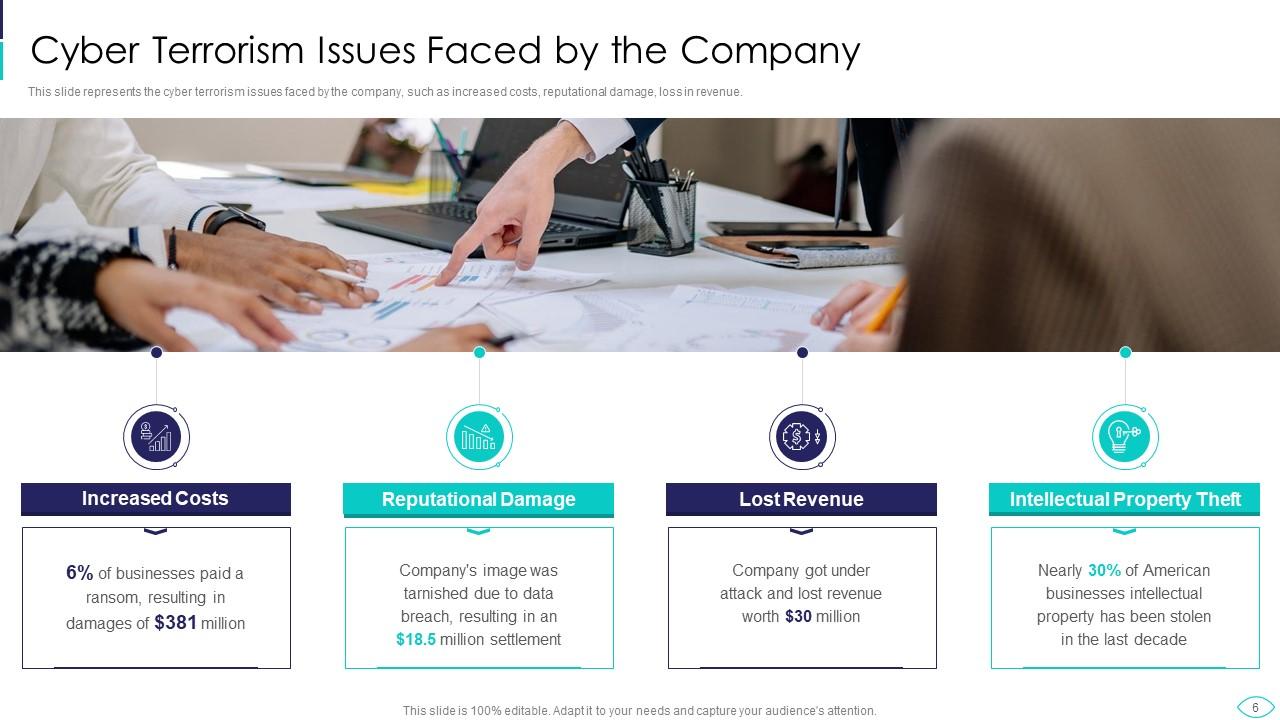
Slide 6: This slide showcases Cyber Terrorism Issues Faced by the Company.
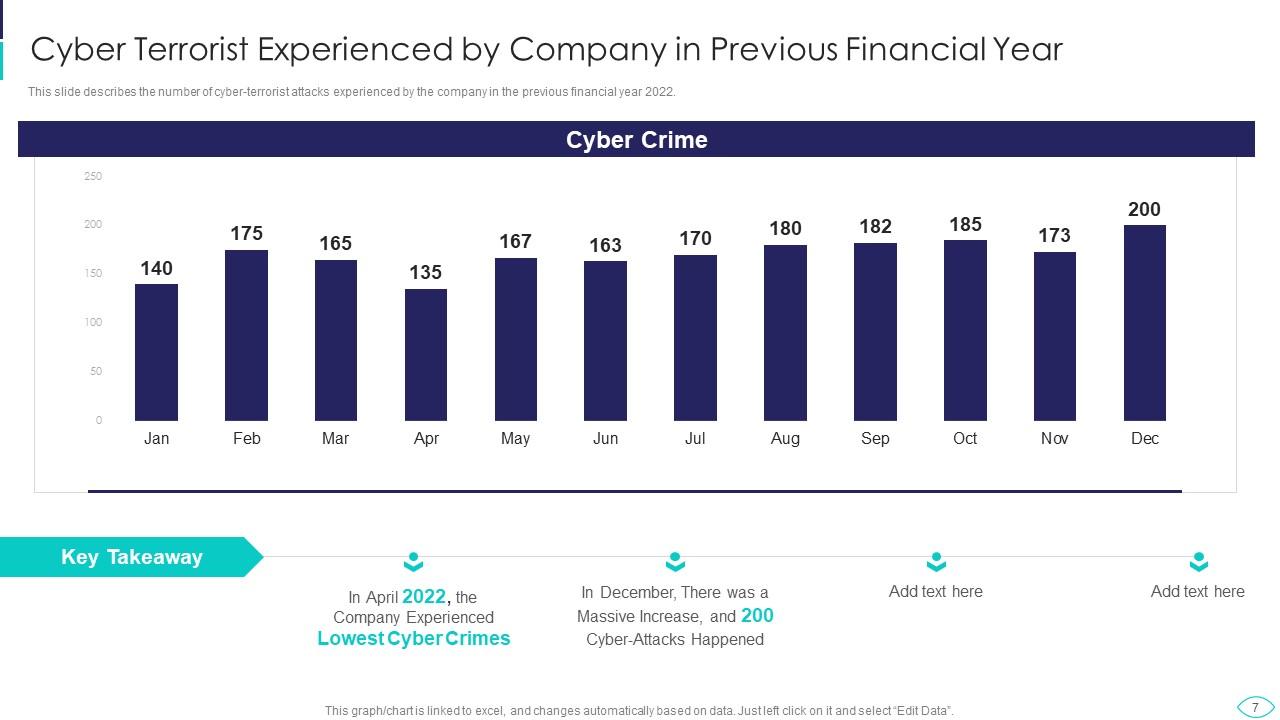
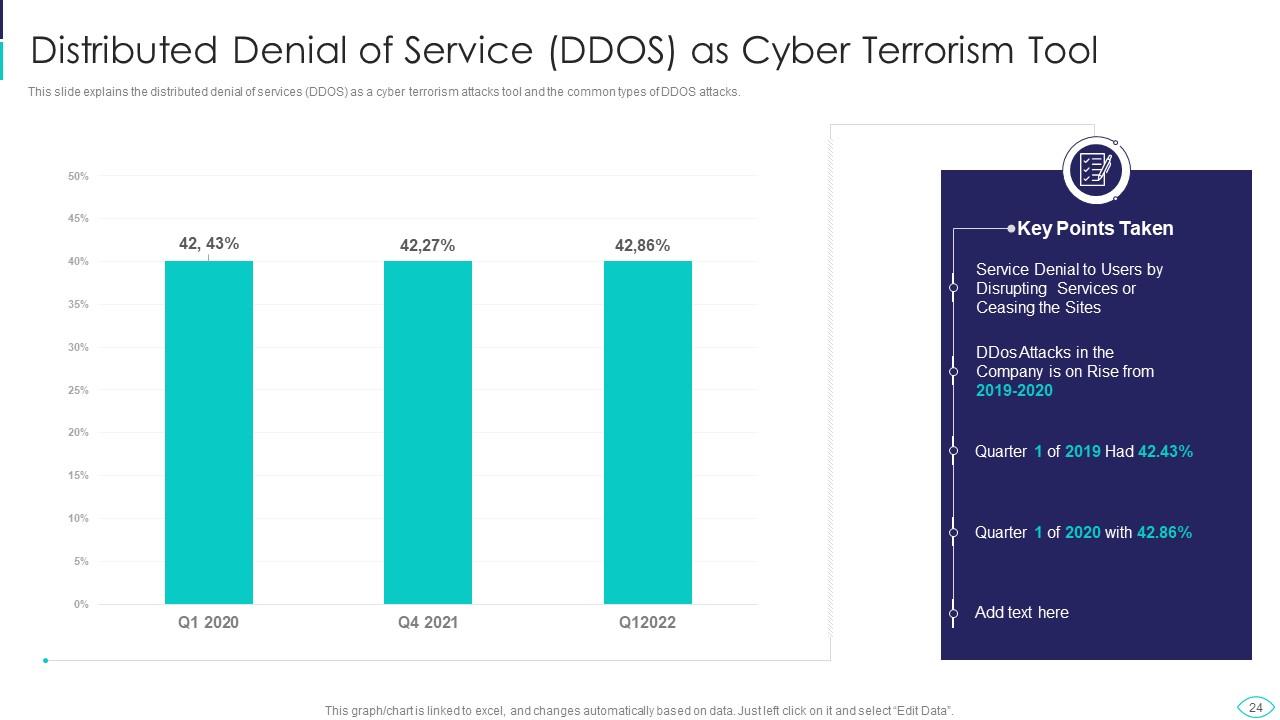
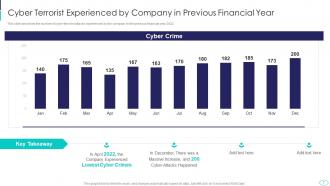
Slide 7: This slide shows Cyber Terrorist Attacks Experienced by Company in Previous Financial Year.
Slide 8: This slide presents average financial loss faced by the business when projects of different scales are attacked.
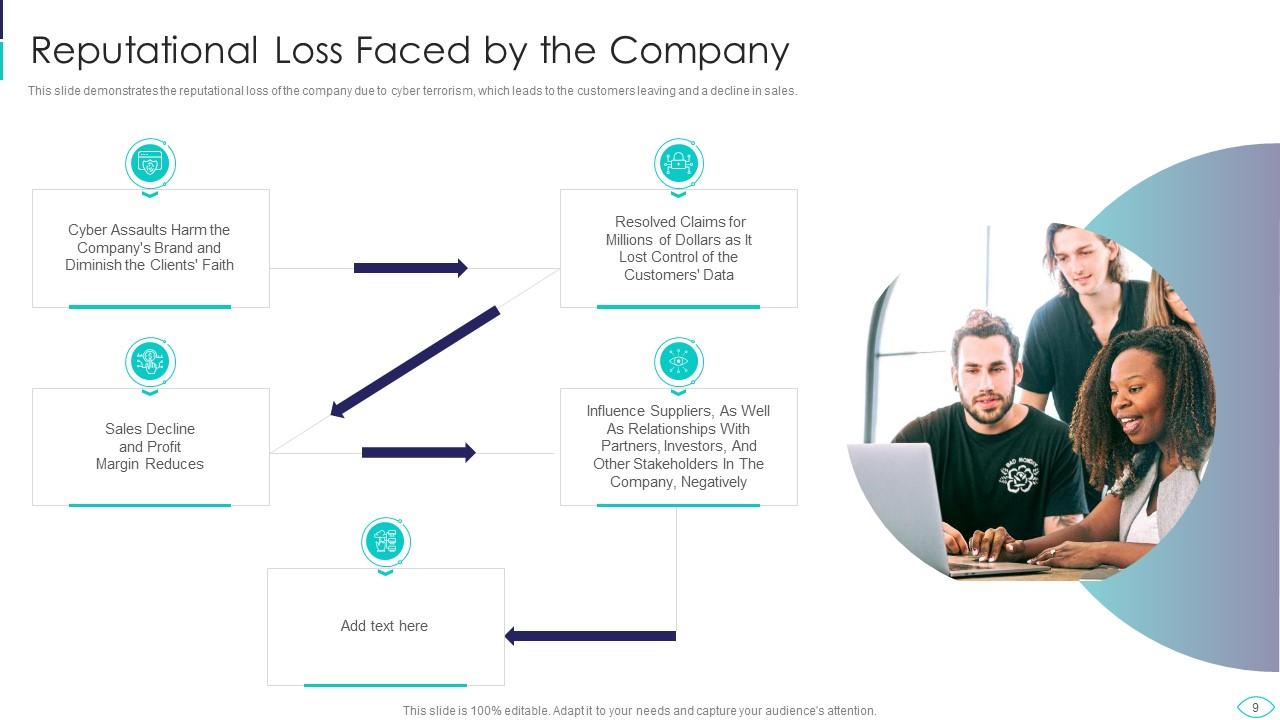
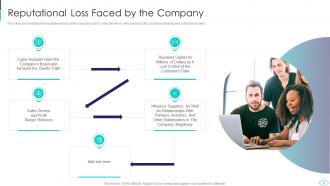
Slide 9: This slide displays reputational loss of the company due to cyber terrorism.
Slide 10: This slide represents title for topics that are to be covered next in the template.
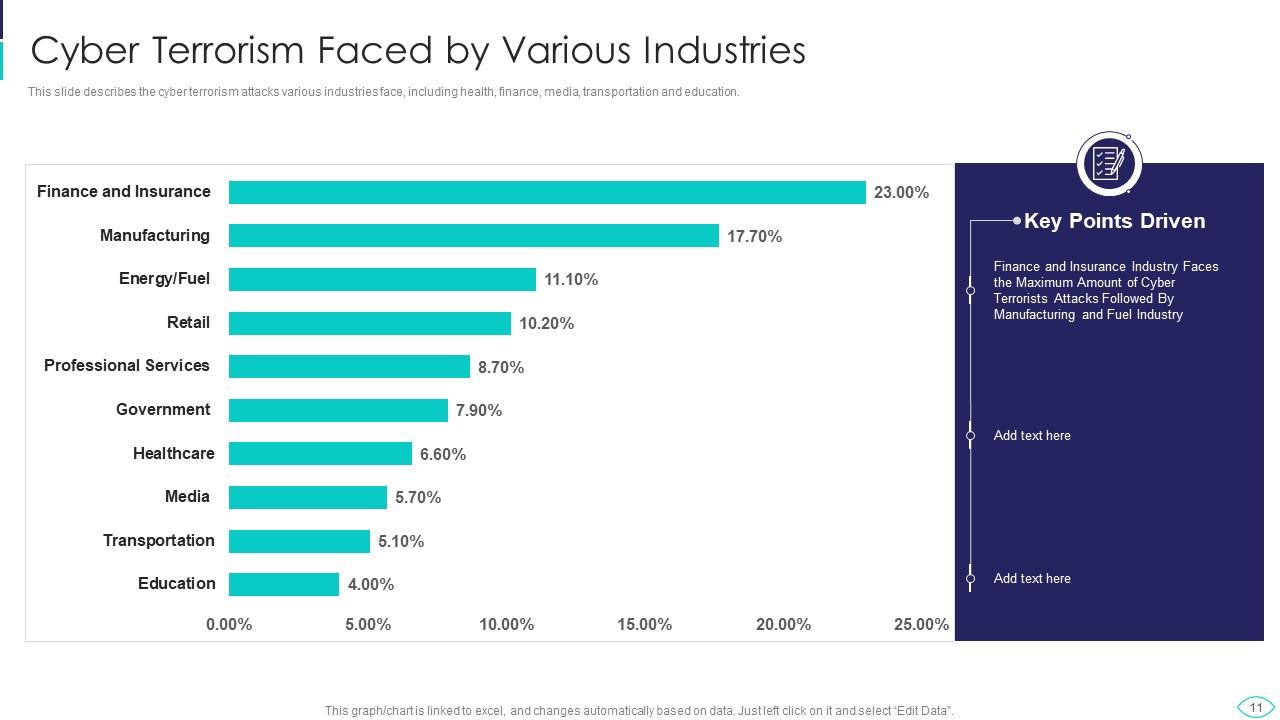
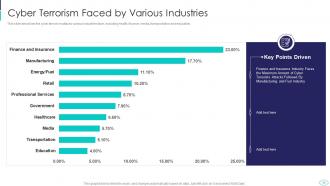
Slide 11: This slide showcases cyber terrorism various industries face, including health, finance, media, etc.
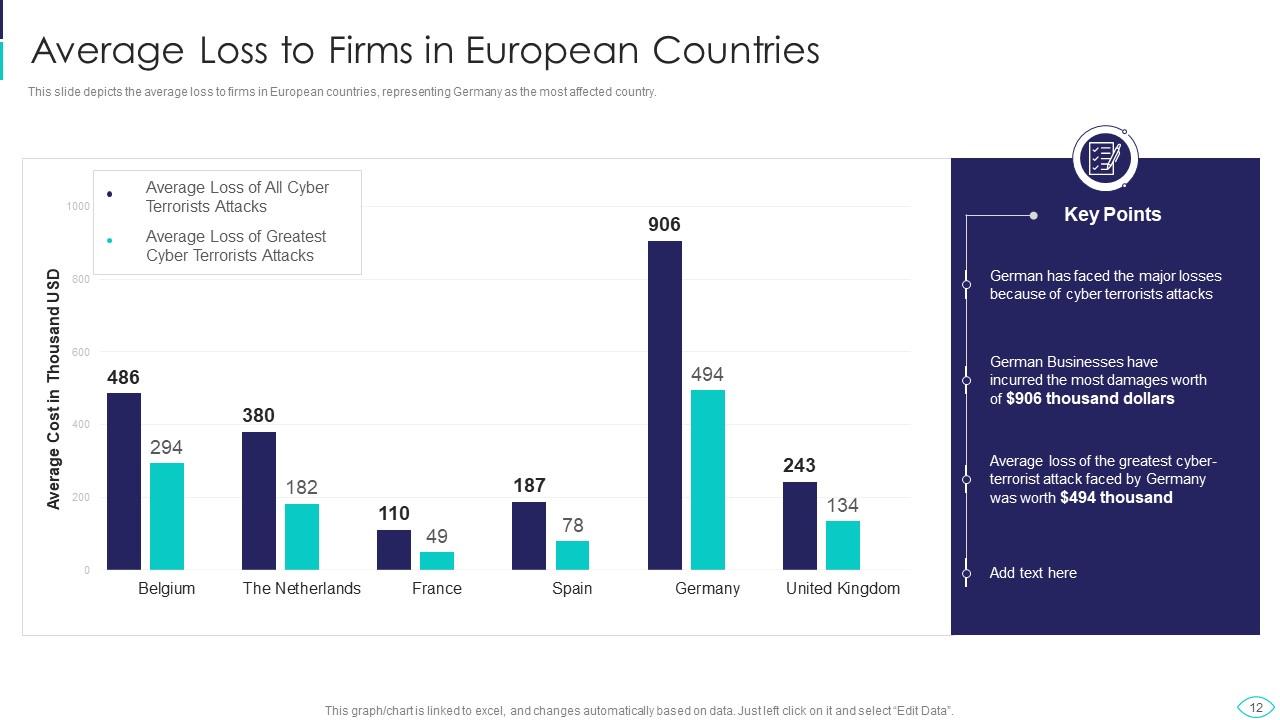
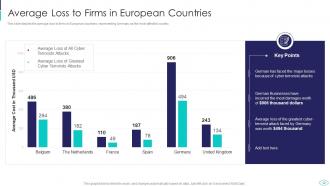
Slide 12: This slide shows average loss to firms in European countries, representing Germany as the most affected.
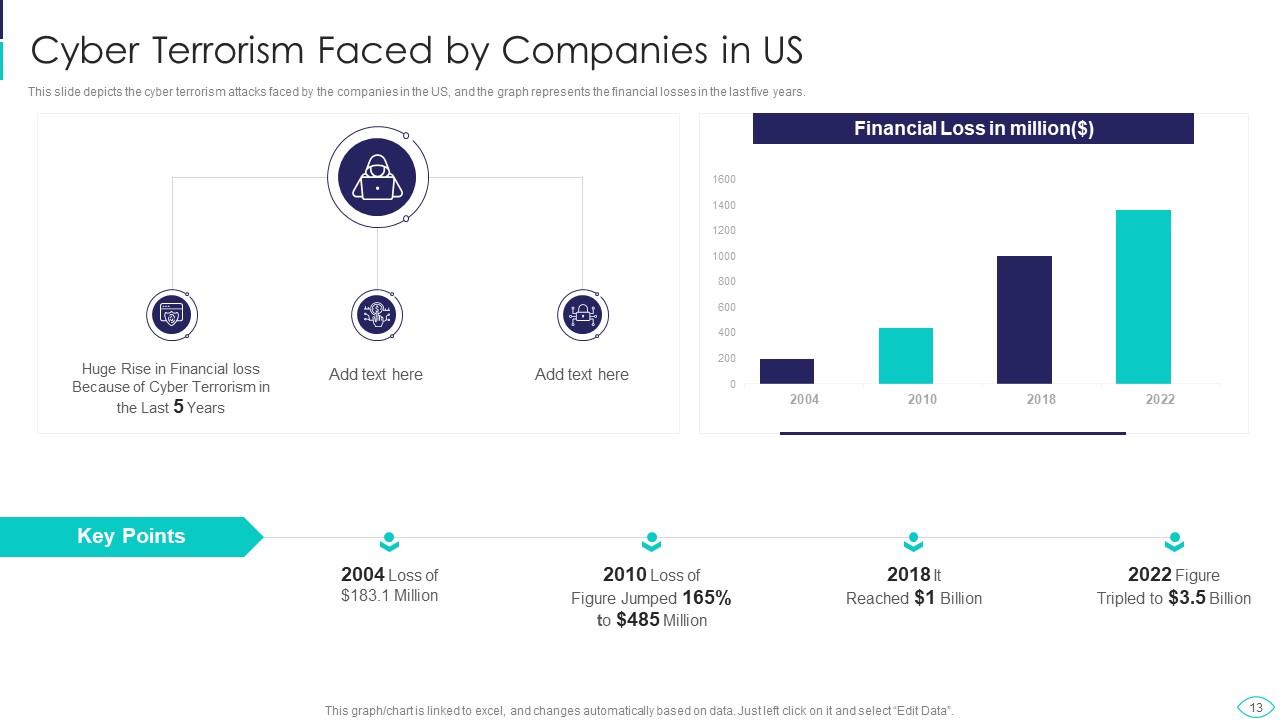
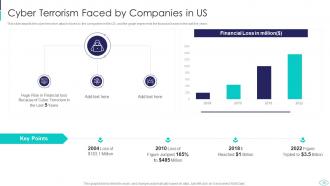
Slide 13: This slide presents cyber terrorism faced by the companies in the US.
Slide 14: This slide displays title for topics that are to be covered next in the template.
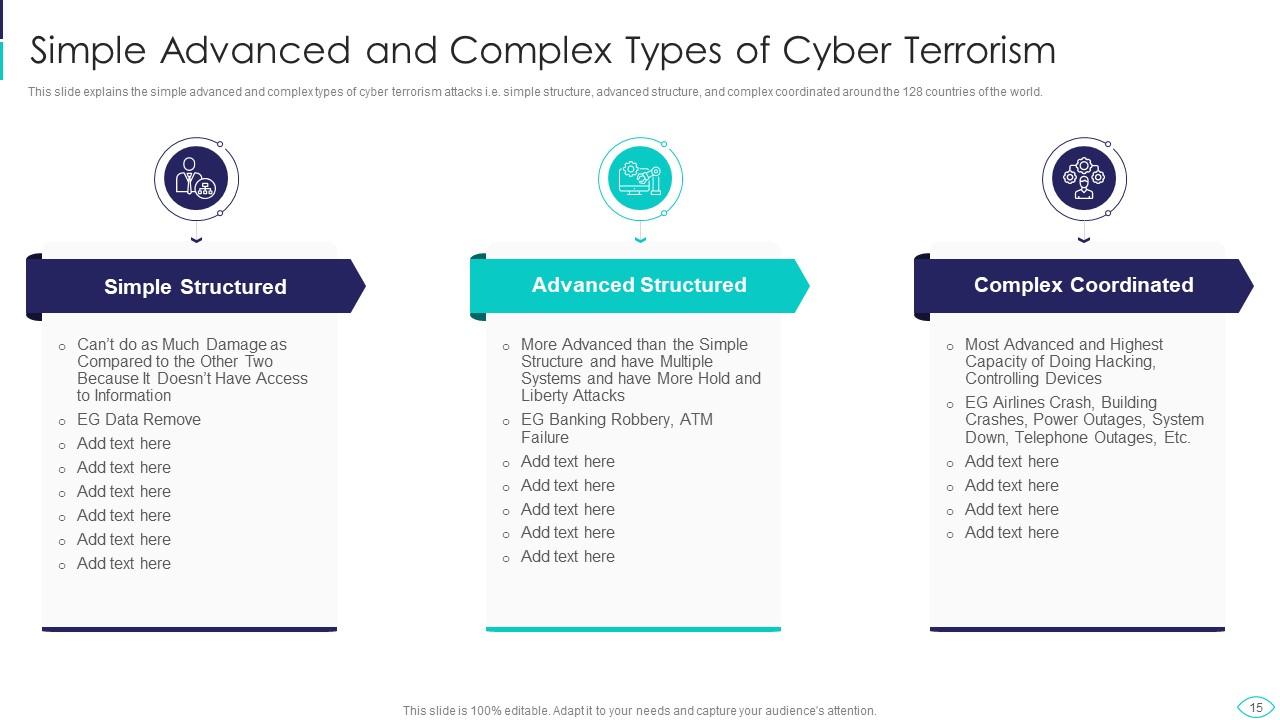
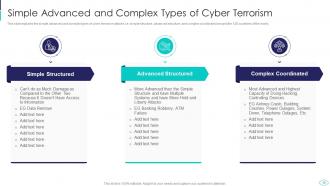
Slide 15: This slide represents Simple Advanced and Complex Types of Cyber Terrorism.
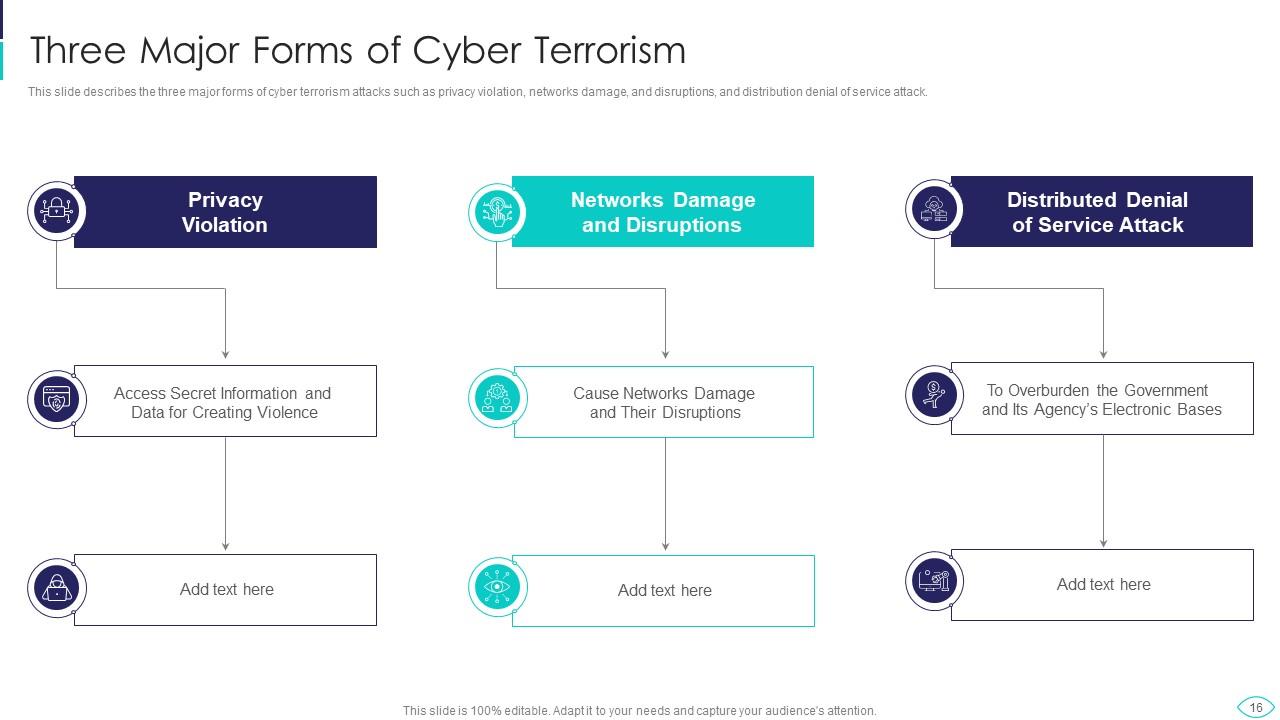
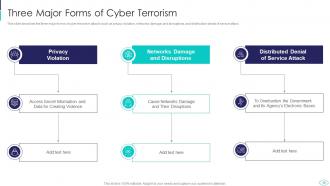
Slide 16: This slide showcases three major forms of cyber terrorism such as privacy violation, networks damage, etc.
Slide 17: This slide shows title for topics that are to be covered next in the template.
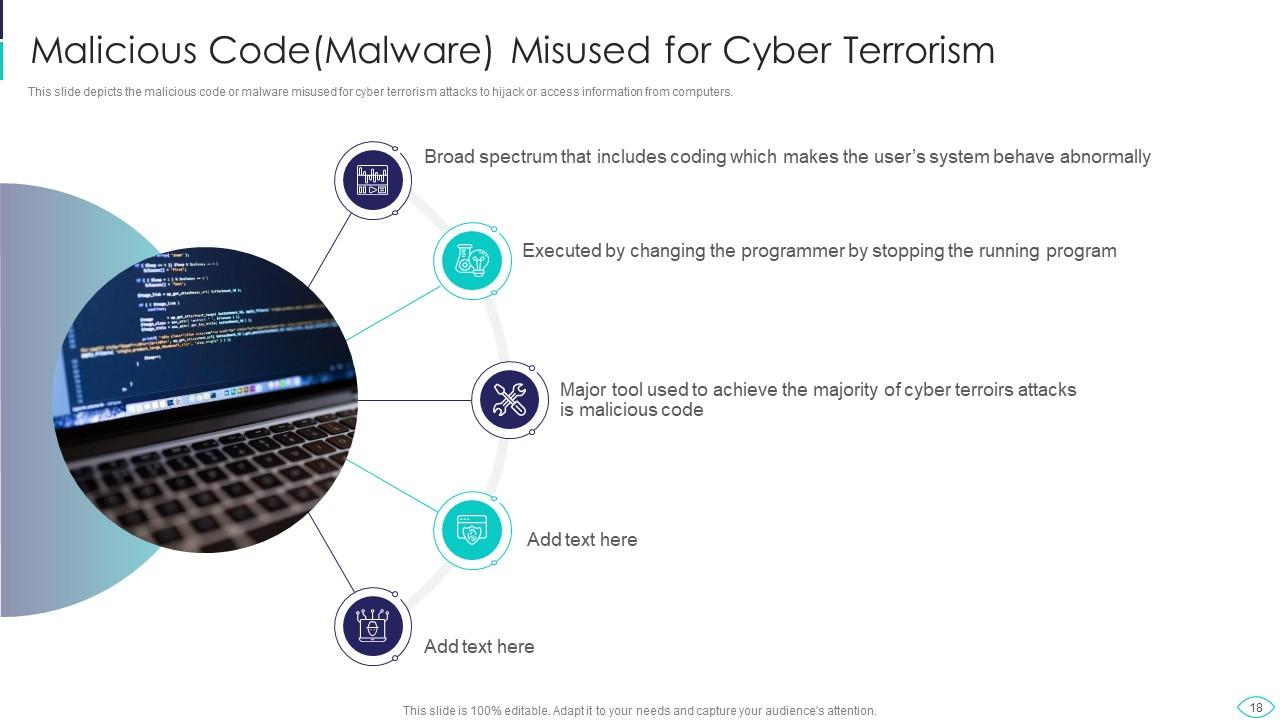
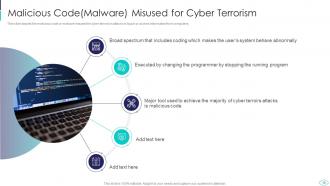
Slide 18: This slide presents malicious code or malware misused for cyber terrorism to hijack or access information.
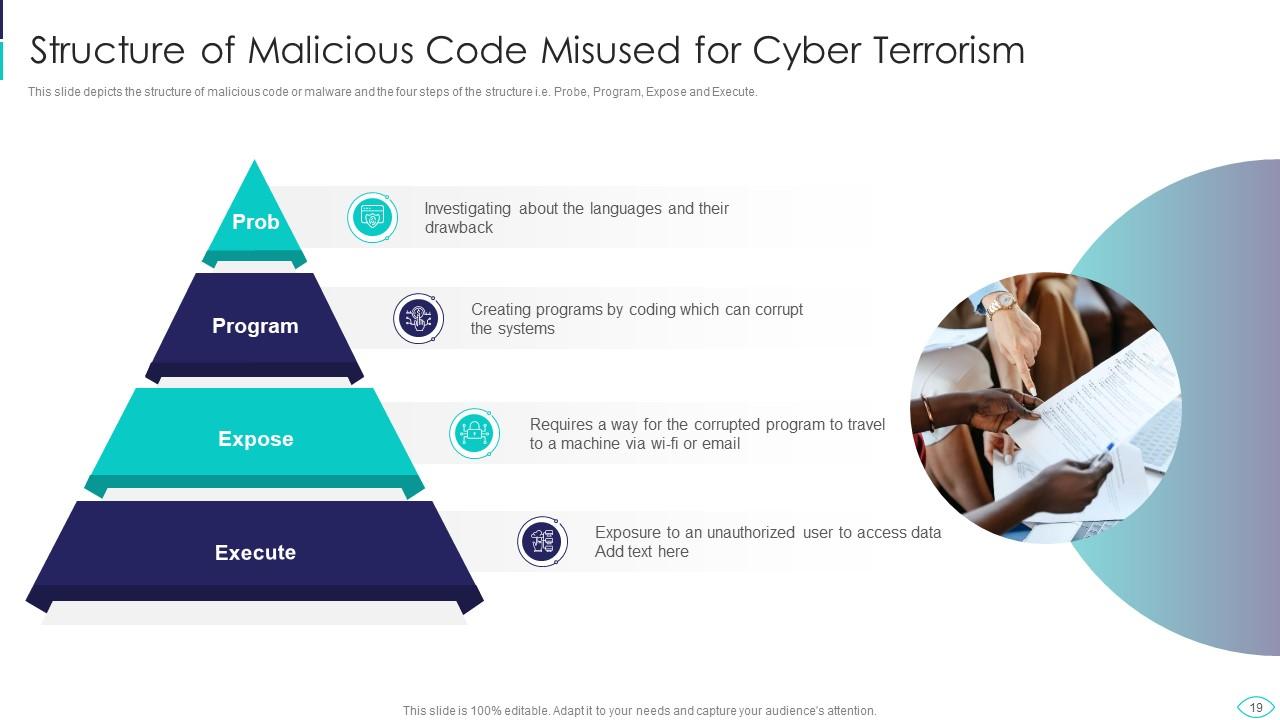
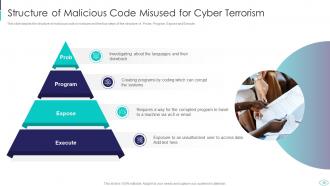
Slide 19: This slide displays Structure of Malicious Code Misused for Cyber Terrorism.
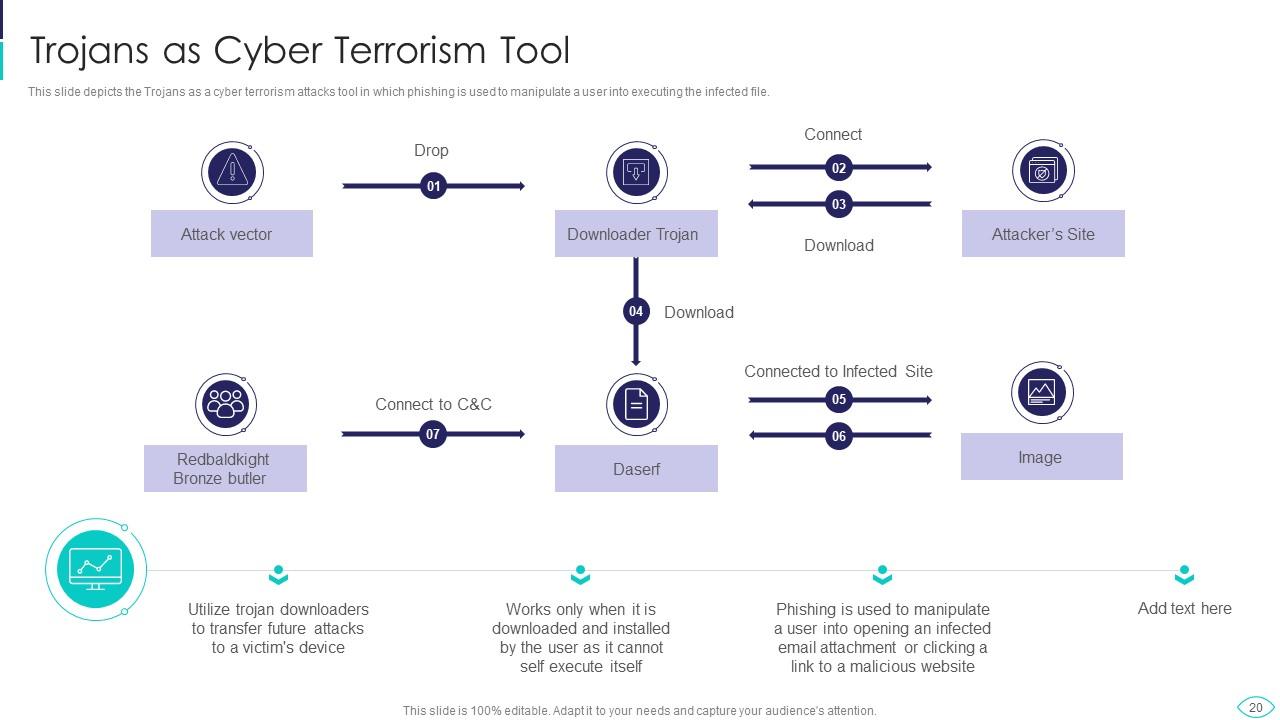
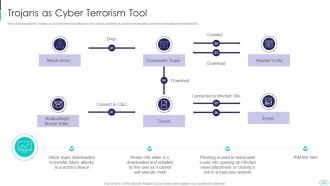
Slide 20: This slide represents Trojans as a cyber terrorism tool in which phishing is used to manipulate a user.
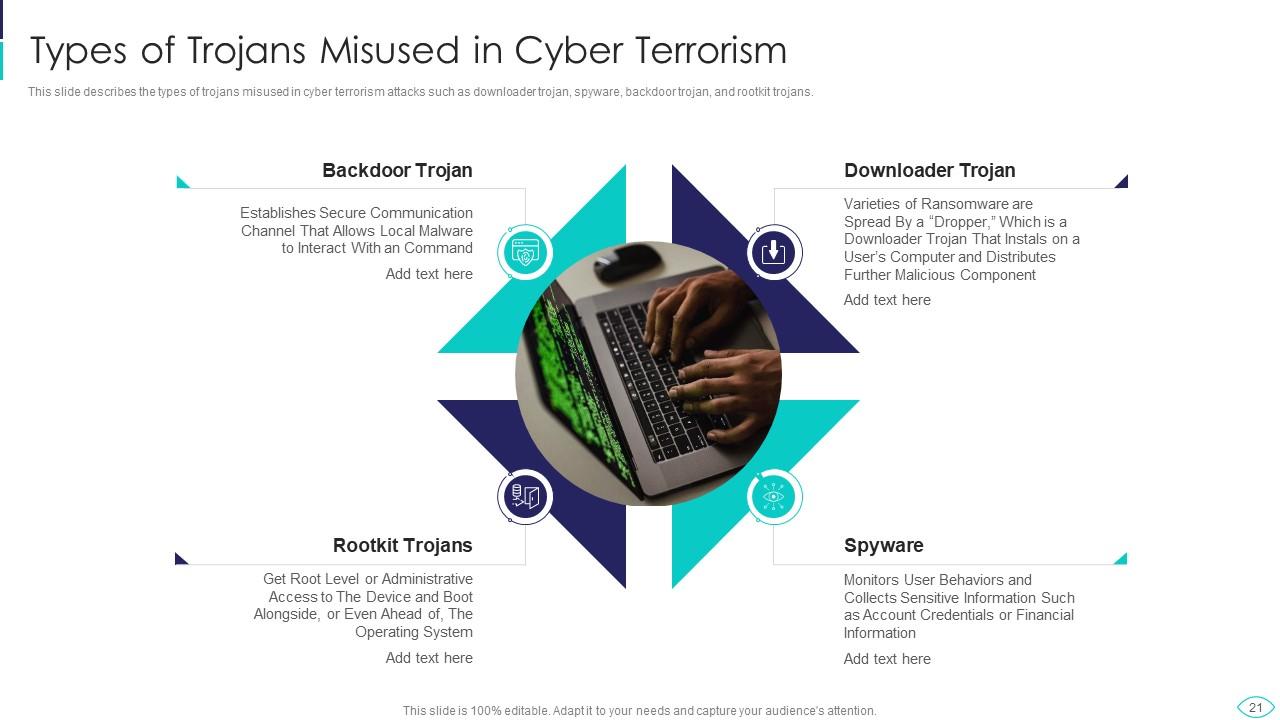
Slide 21: This slide showcases types of trojans misused in cyber terrorism, such as downloader trojan, spyware, backdoor trojan, etc.
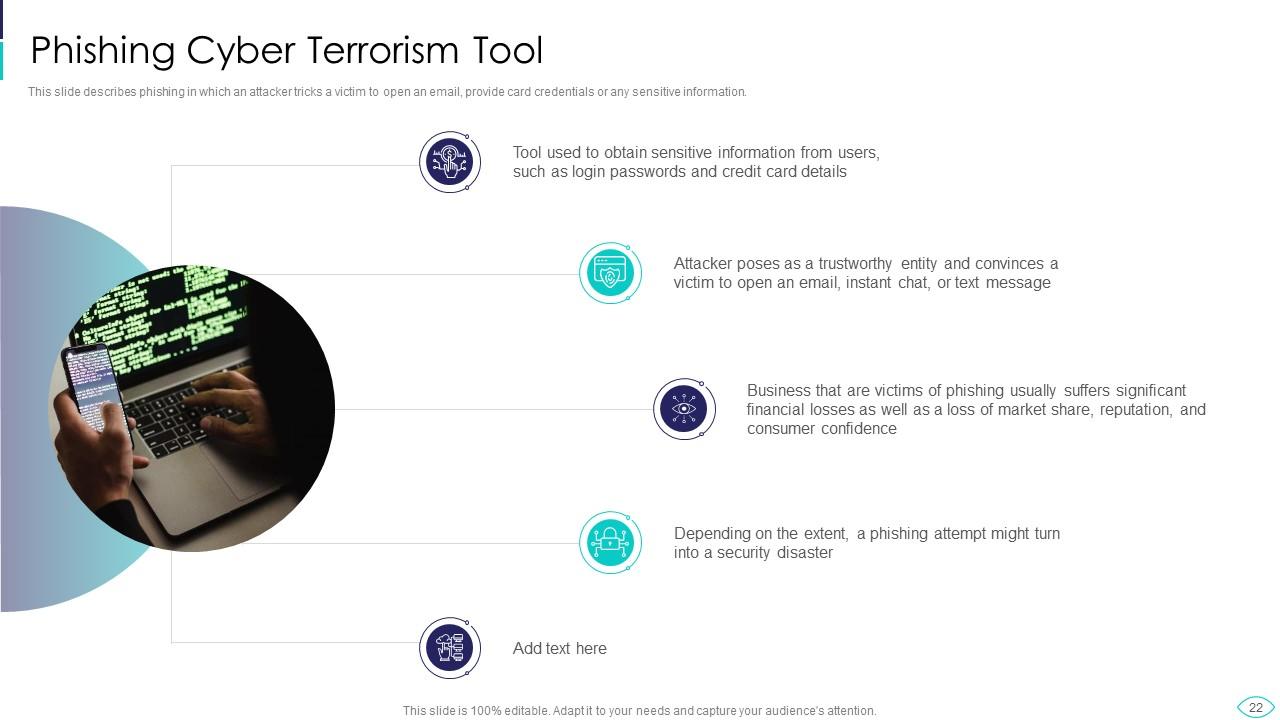
Slide 22: This slide shows phishing in which an attacker tricks a victim to open an email.
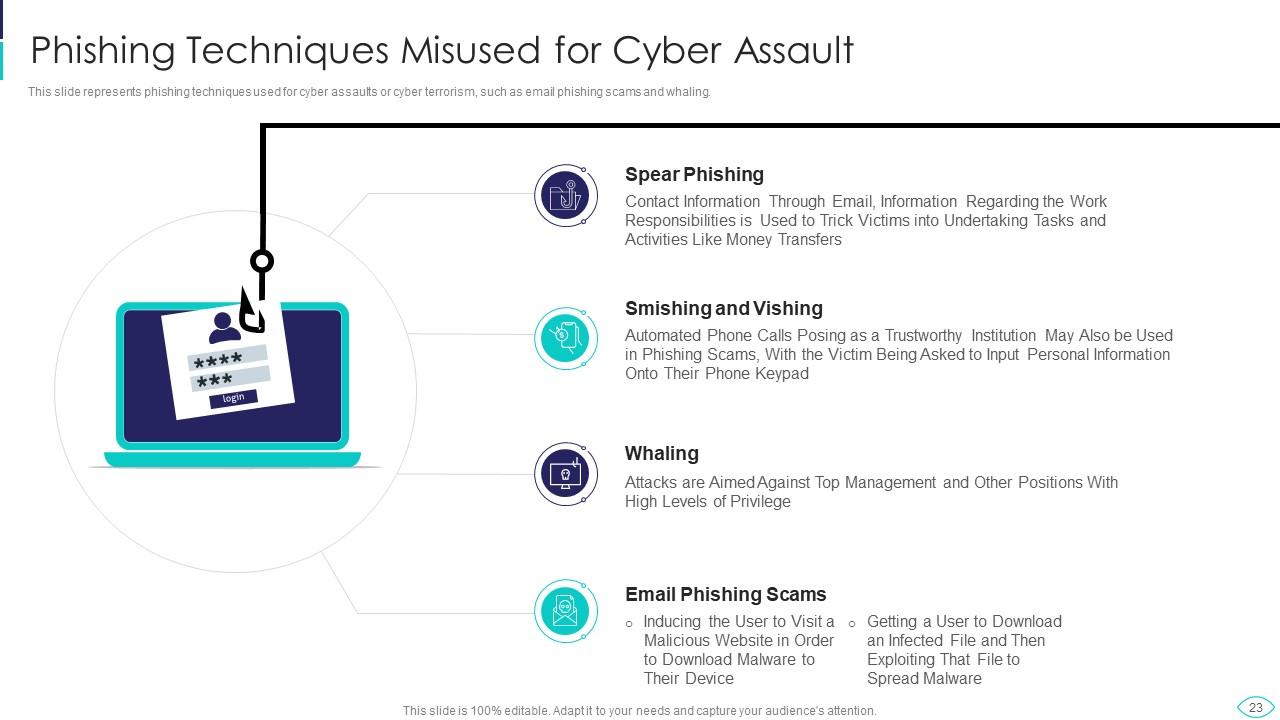
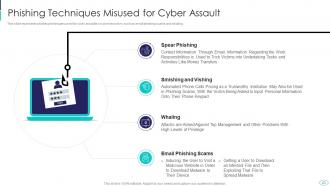
Slide 23: This slide presents Phishing Techniques Misused for Cyber Assault.
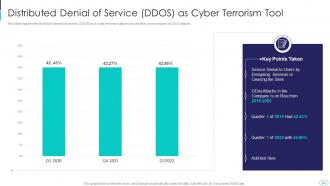
Slide 24: This slide displays Distributed Denial of Service (DDOS) as Cyber Terrorism Too.
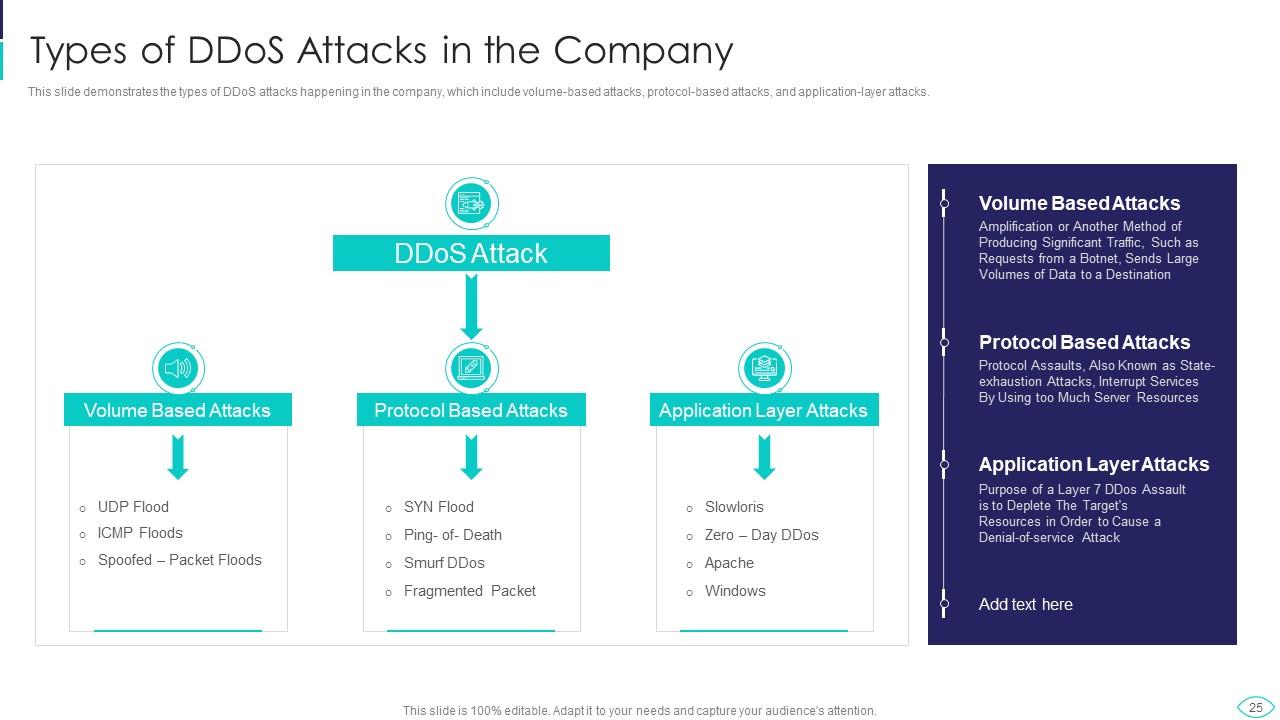
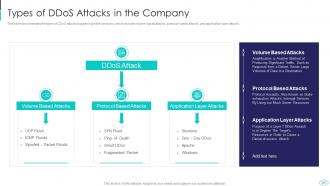
Slide 25: This slide represents types of DDoS attacks happening in the company, which include volume-based attacks, protocol-based attacks, etc.
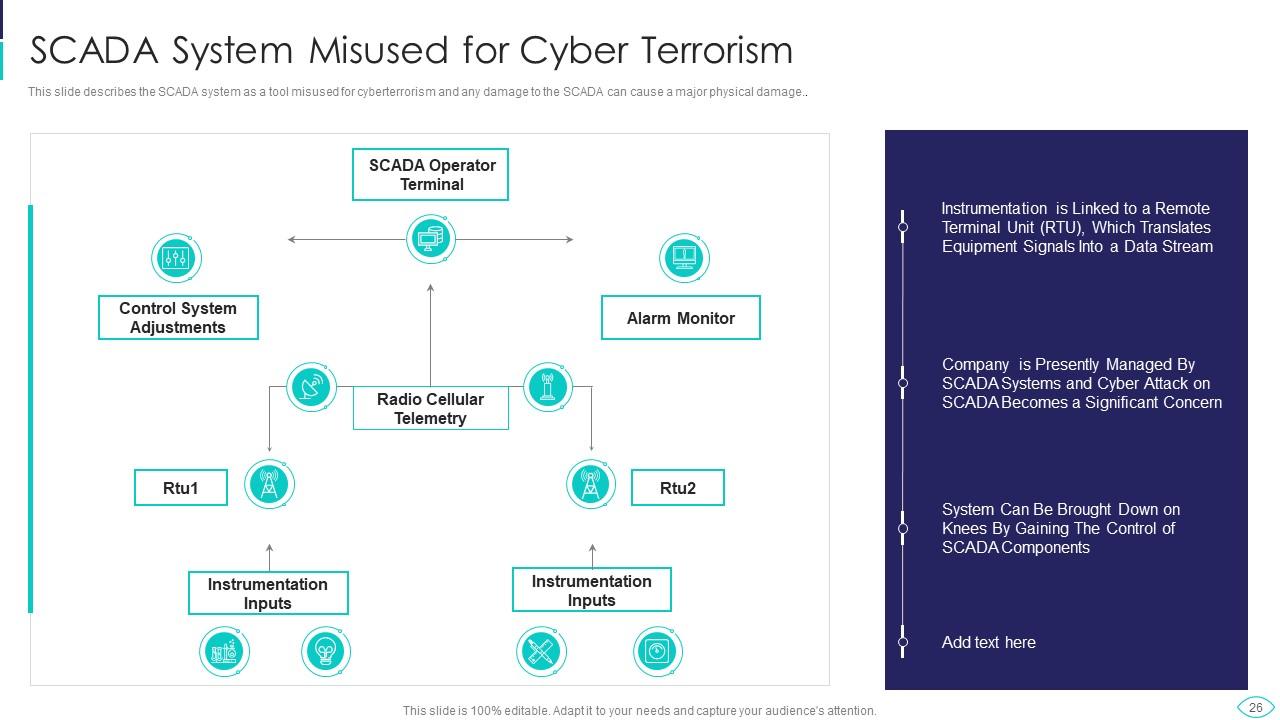
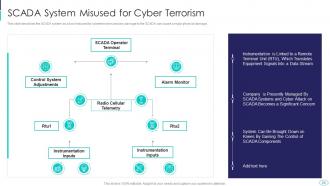
Slide 26: This slide showcases SCADA system as a tool misused for cyberterrorism and any damage to the SCADA.
Slide 27: This slide shows title for topics that are to be covered next in the template.
Slide 28: This slide presents How to Protect Company from Trojan Attacks.
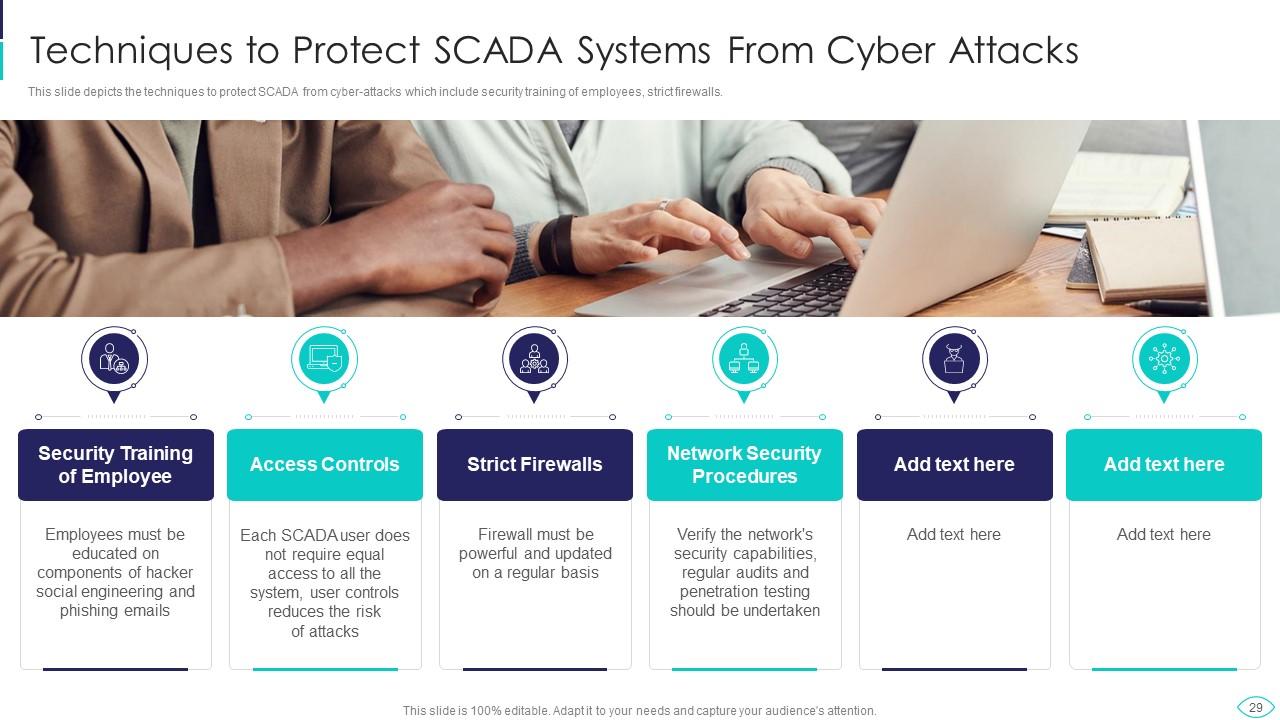
Slide 29: This slide displays Techniques to Protect SCADA Systems From Cyber Attacks.
Slide 30: This slide represents How to Prevent DDoS Attacks in the Company.
Slide 31: This slide showcases title for topics that are to be covered next in the template.
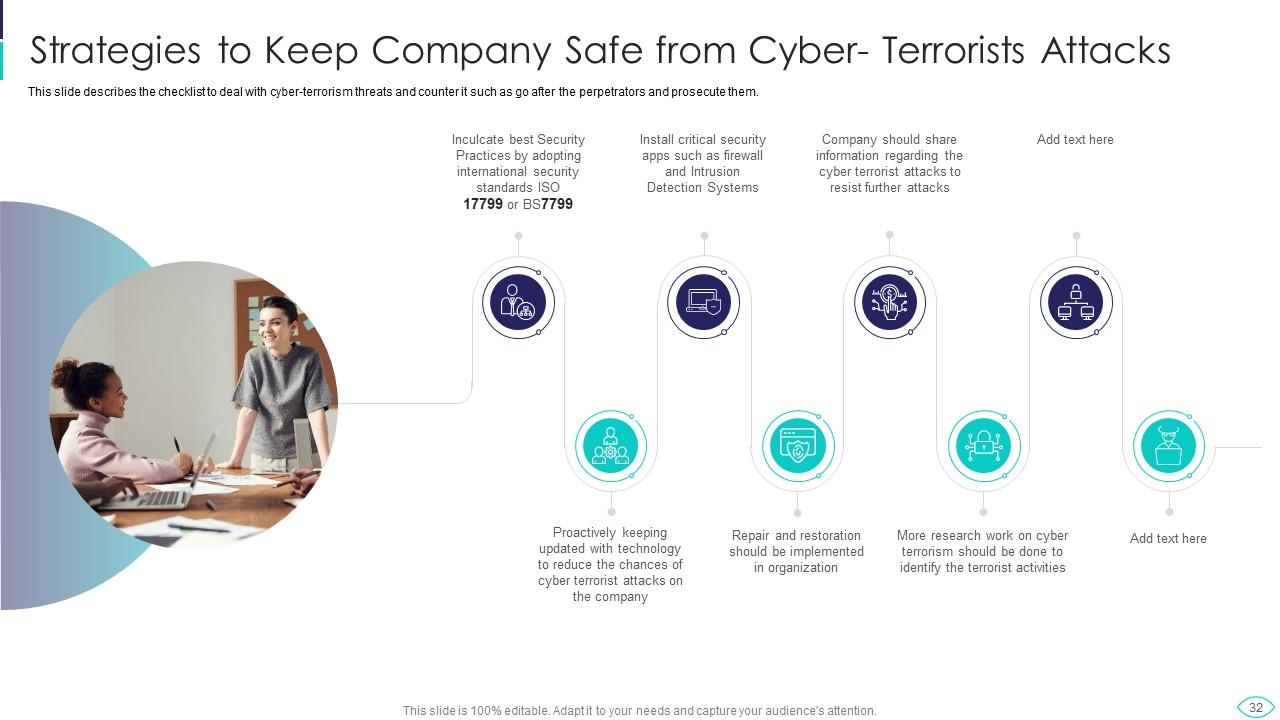
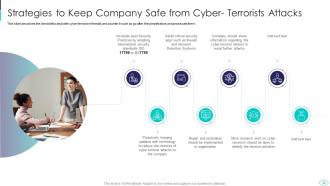
Slide 32: This slide shows Strategies to Keep Company Safe from Cyber- Terrorists attacks.
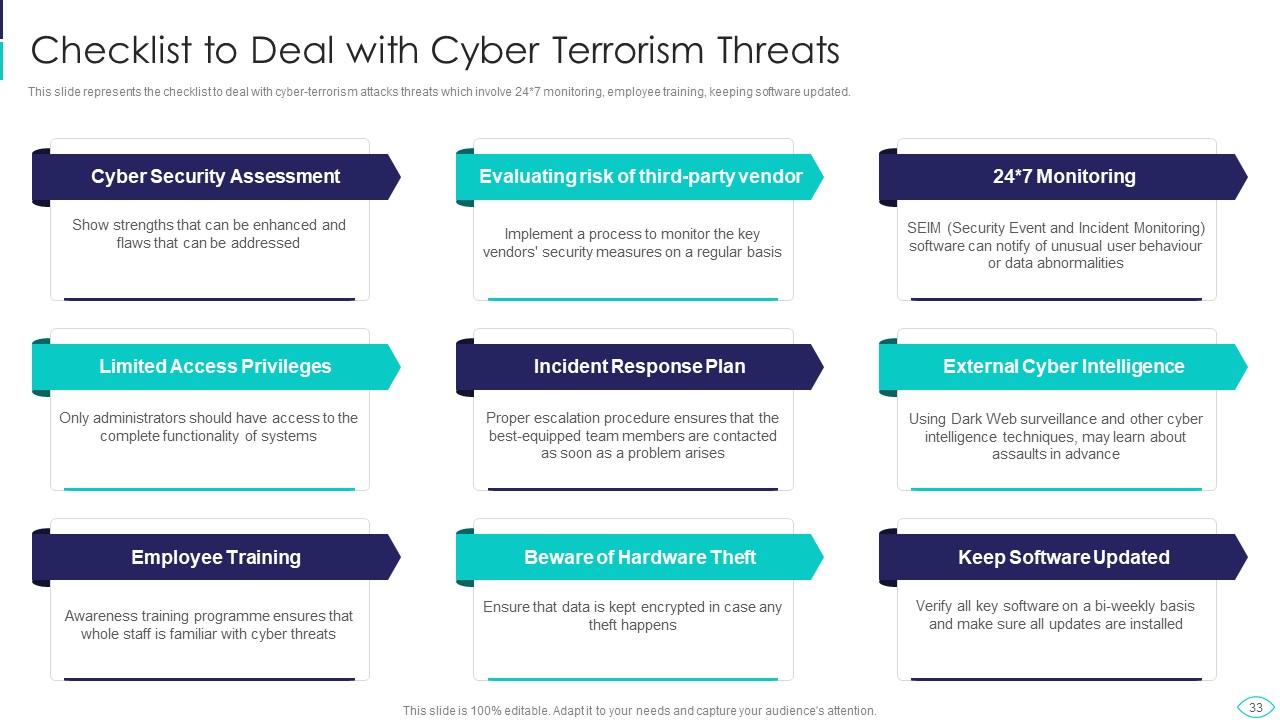
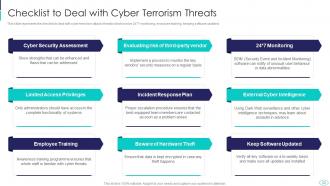
Slide 33: This slide presents Checklist to Deal with Cyber Terrorism Threats.
Slide 34: This slide displays title for topics that are to be covered next in the template.
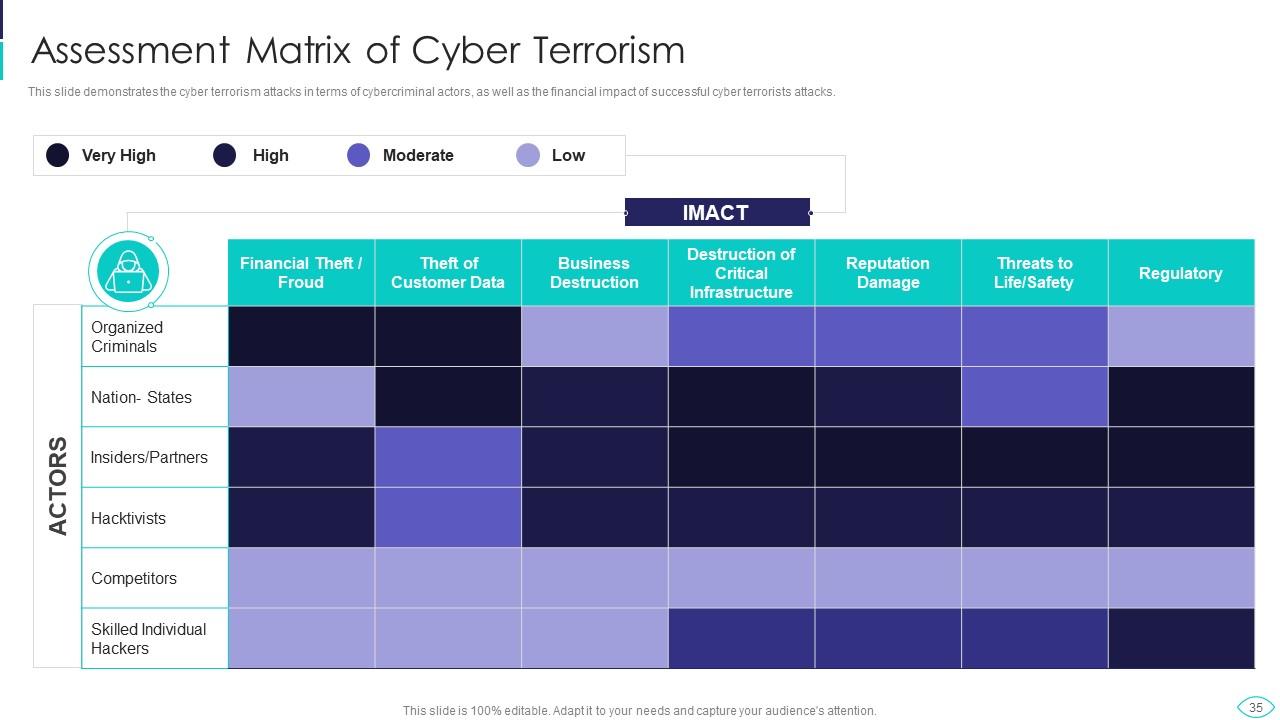
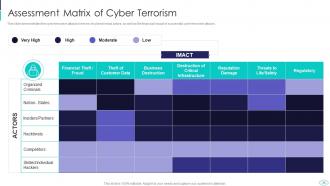
Slide 35: This slide represents cyber terrorism in terms of cybercriminal actors, as well as the financial impact of successful cyber terrorists attacks.
Slide 36: This slide showcases title for topics that are to be covered next in the template.
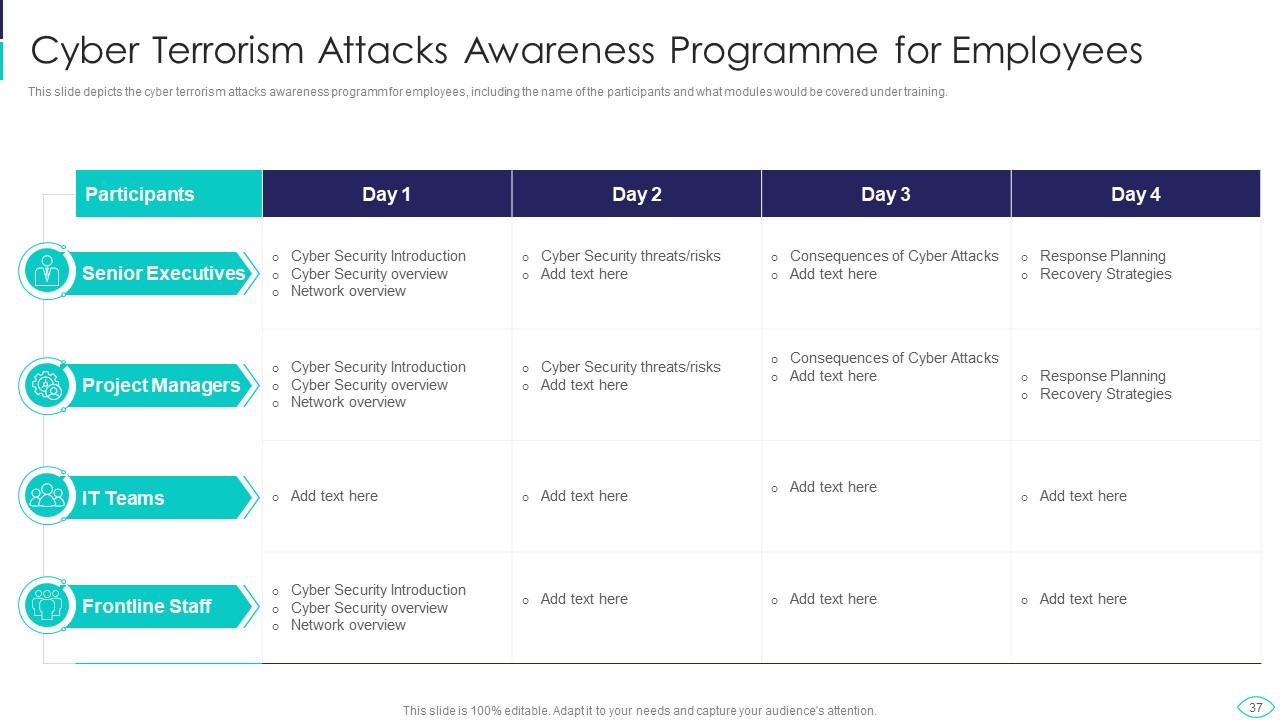
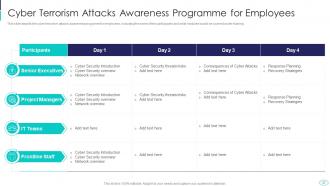
Slide 37: This slide shows Cyber Terrorism Awareness Programme for Employees.
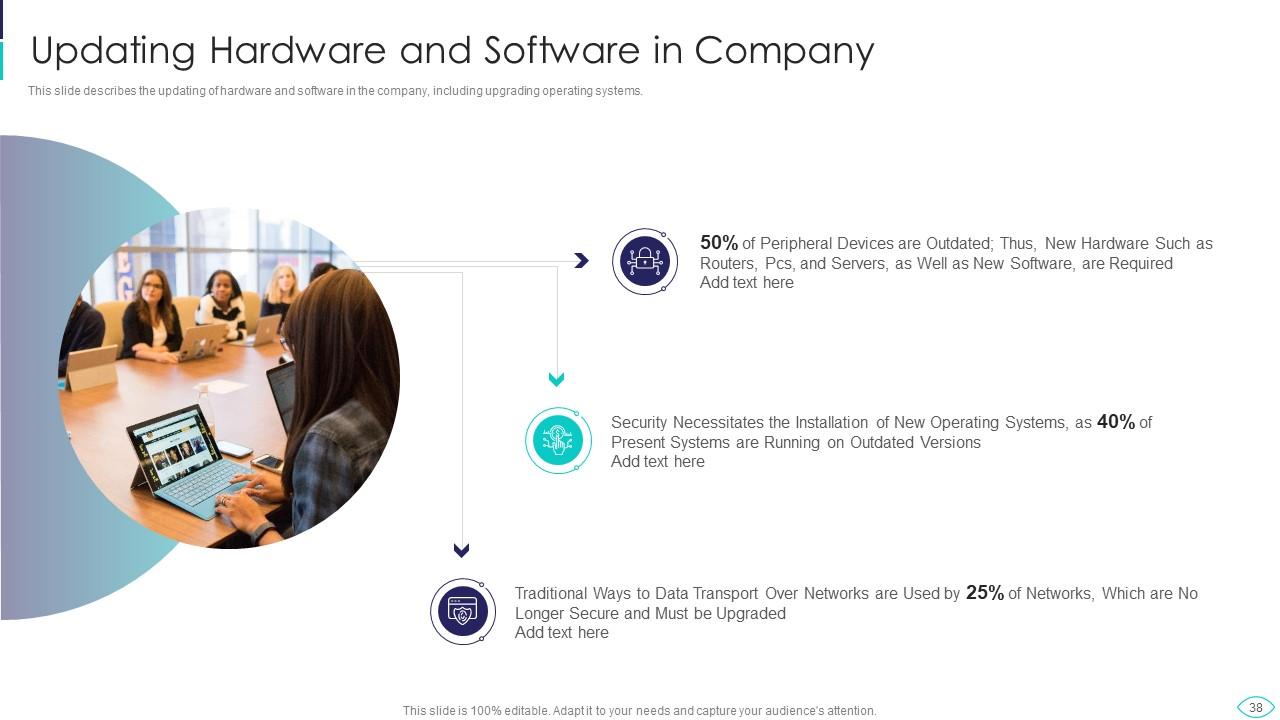
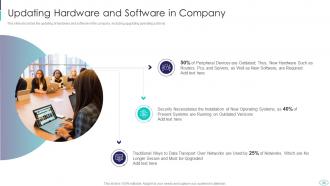
Slide 38: This slide presents updating of hardware and software in the company, including upgrading operating systems.
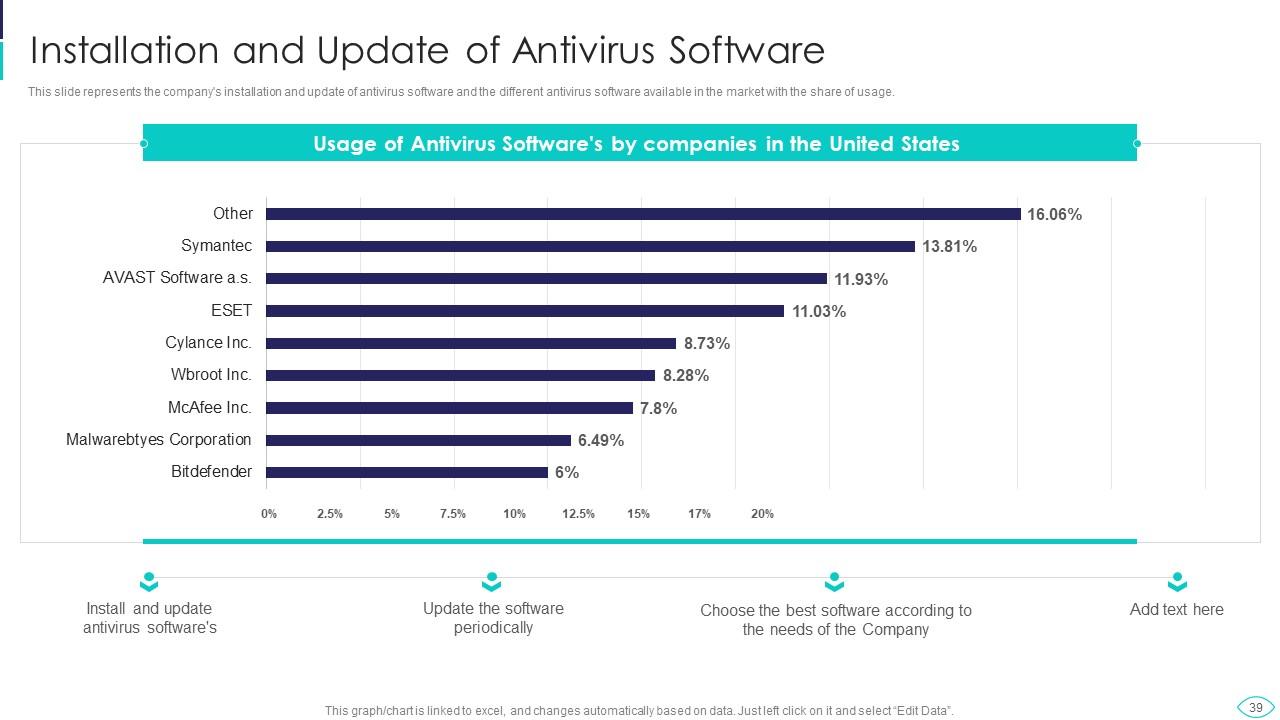
Slide 39: This slide displays company's installation and update of antivirus software and the different antivirus software available in the market.
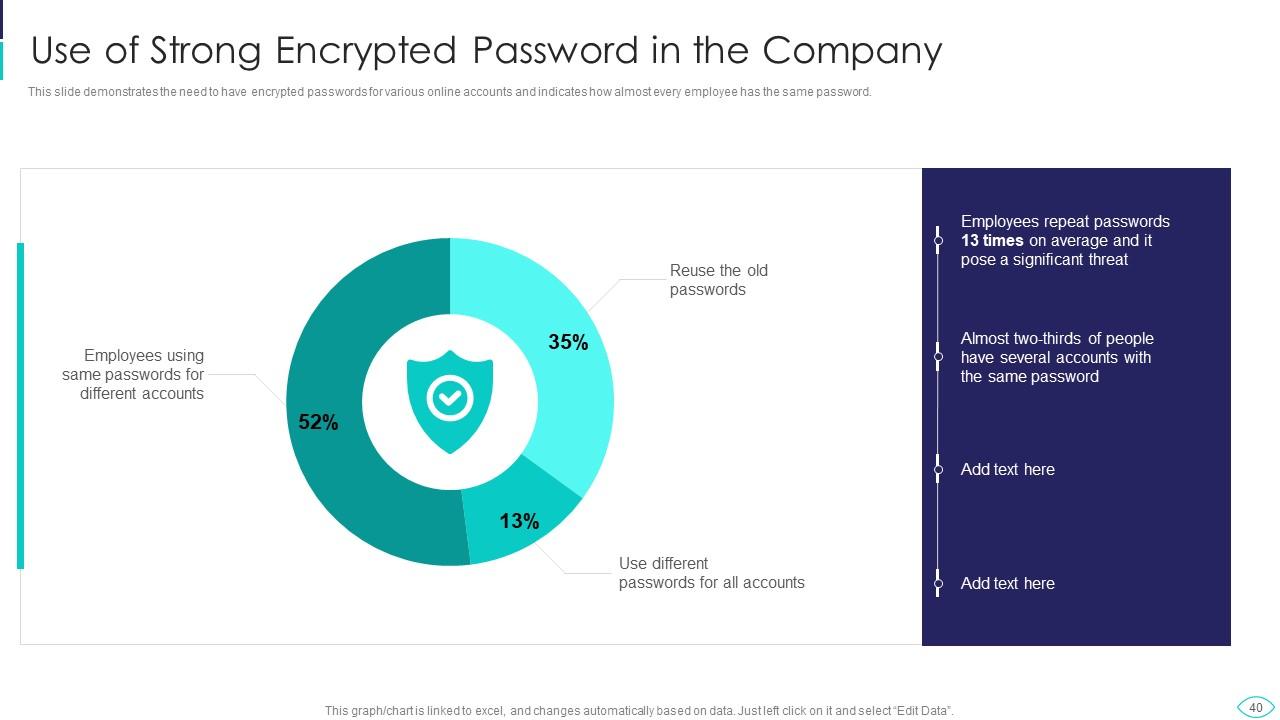
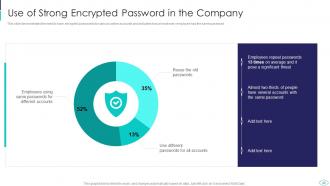
Slide 40: This slide represents Use of Strong Encrypted Password in the Company.
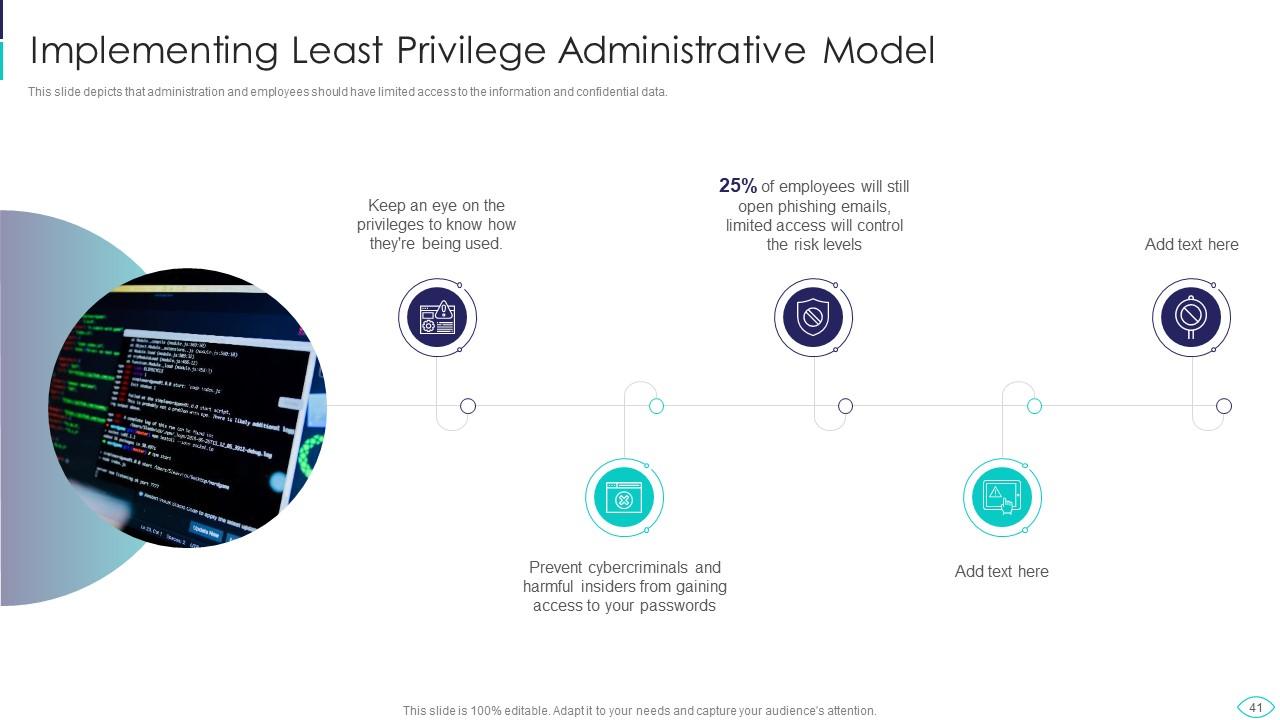
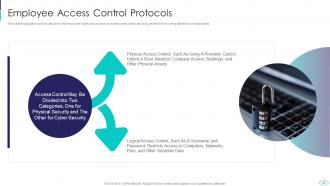
Slide 41: This slide showcases administration and employees should have limited access to the information.
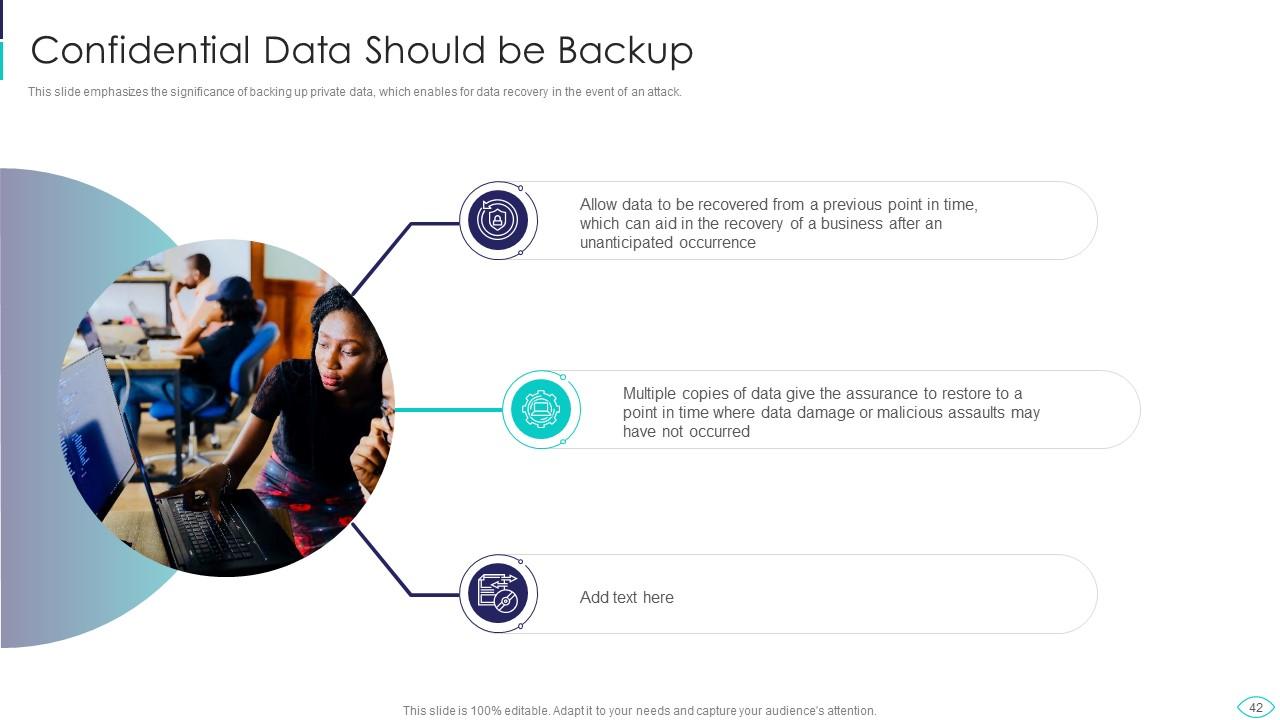
Slide 42: This slide shows significance of backing up private data, which enables for data recovery in the event.
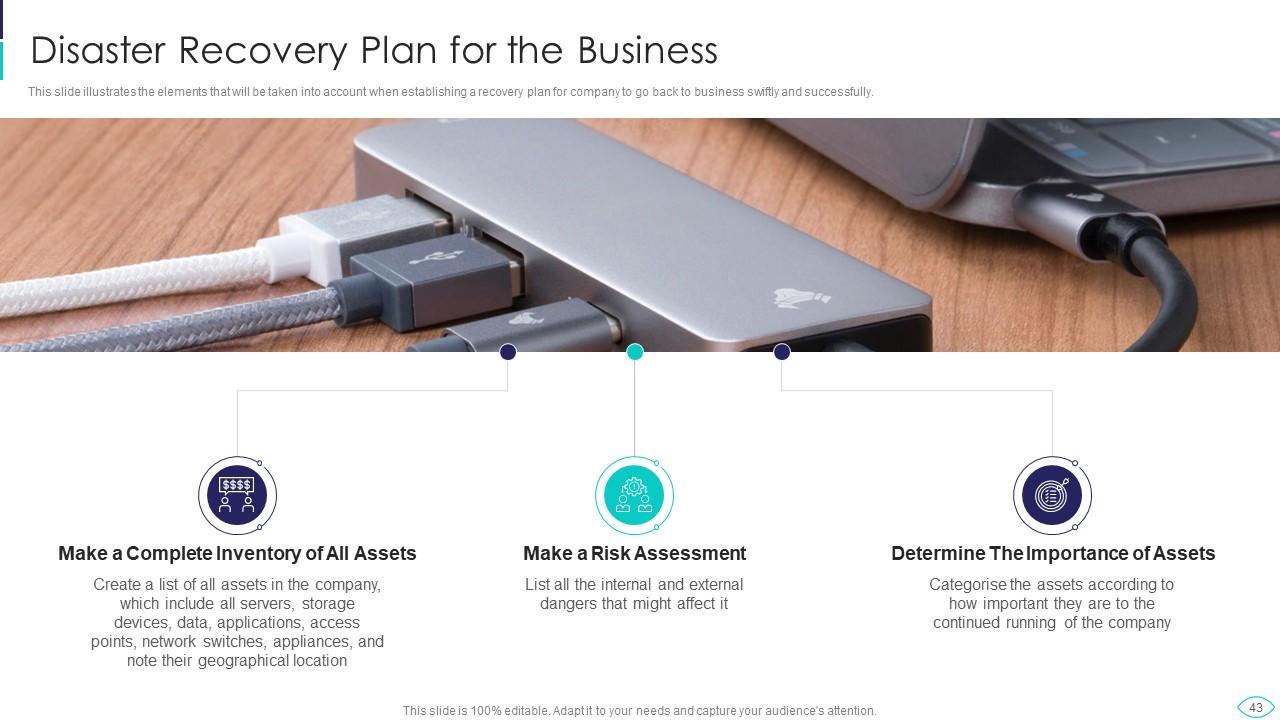
Slide 43: This slide presents elements that will be taken into account when establishing a recovery plan.
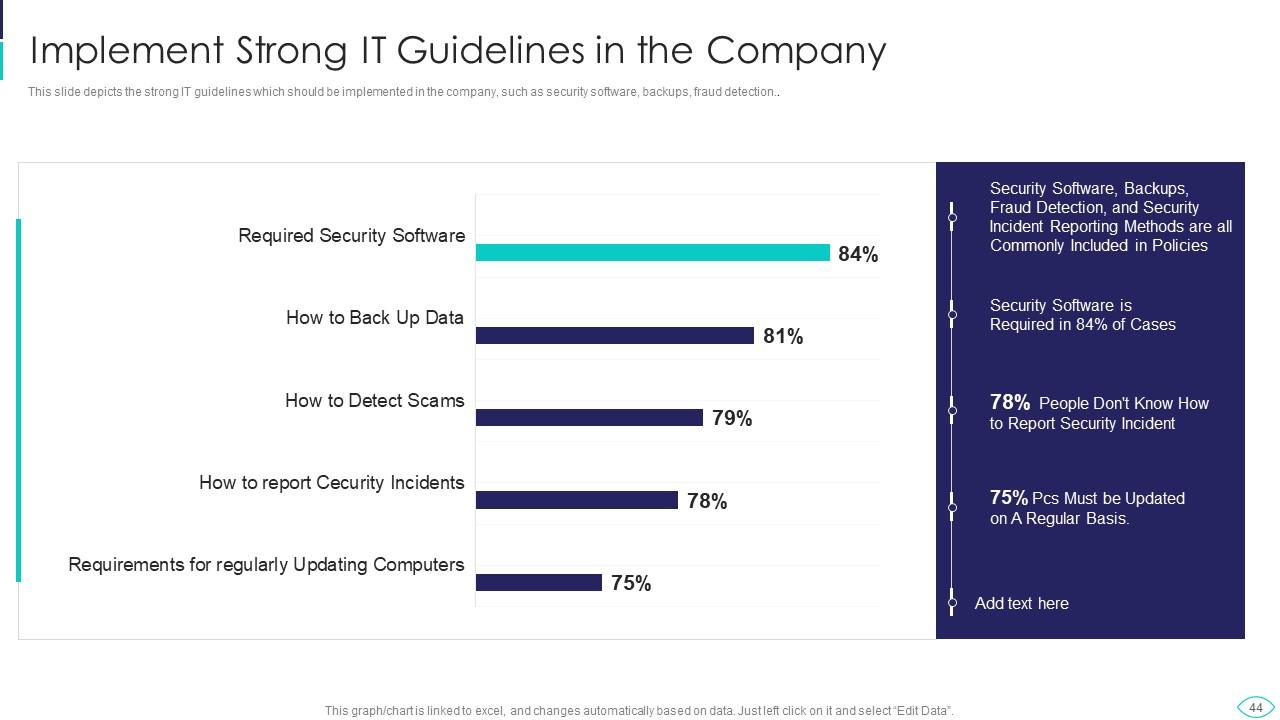
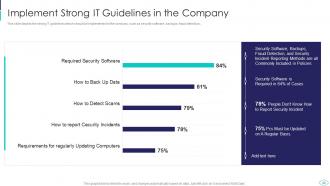
Slide 44: This slide displays strong IT guidelines which should be implemented in the company.
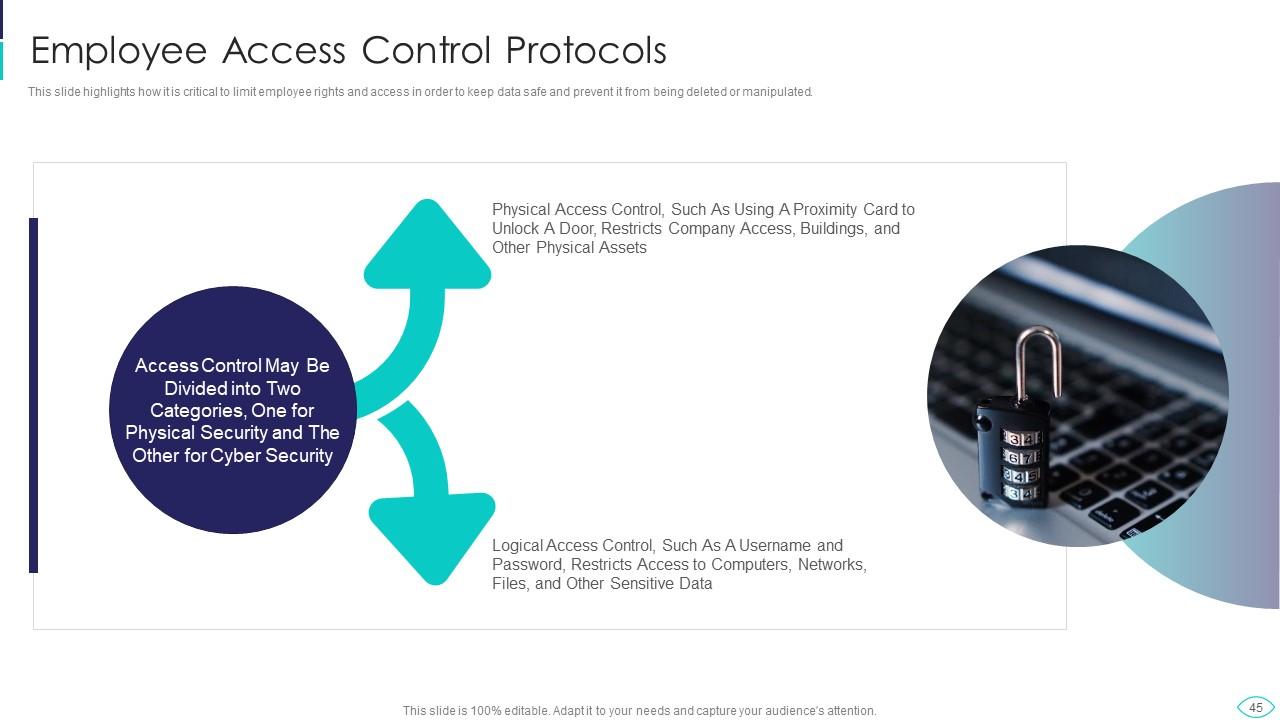
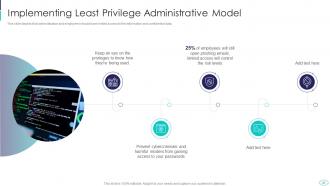
Slide 45: This slide represents how it is critical to limit employee rights and access in order to keep data safe.
Slide 46: This slide showcases title for topics that are to be covered next in the template.
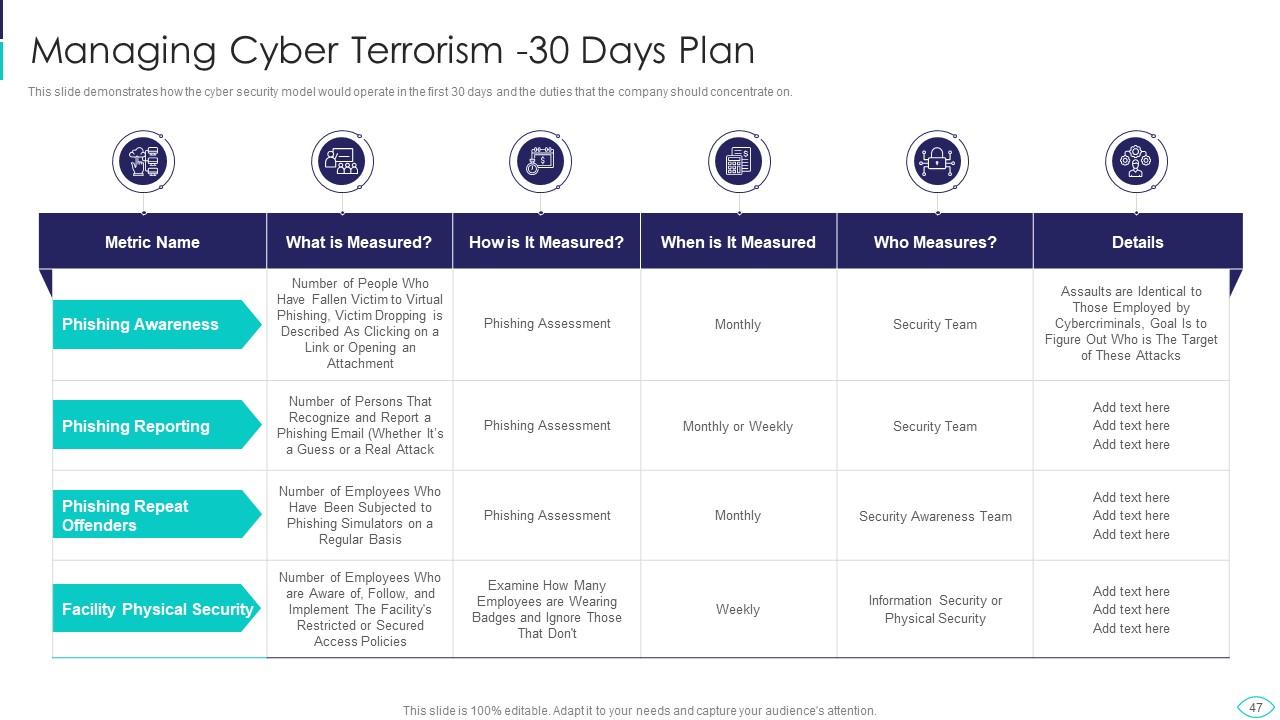
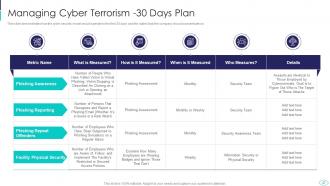
Slide 47: This slide shows how the cyber security model would operate in the first 30 days.
Slide 48: This slide presents plan for the next 60 days after the firm has implemented the cyber security model.
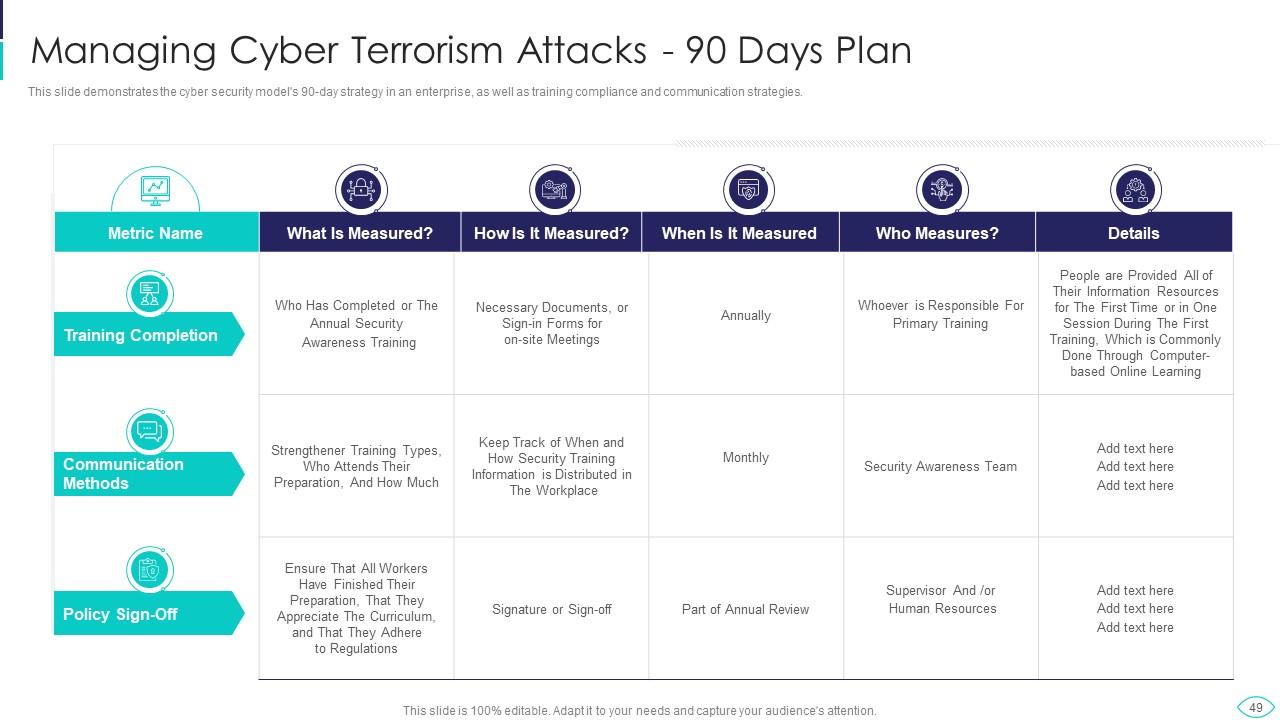
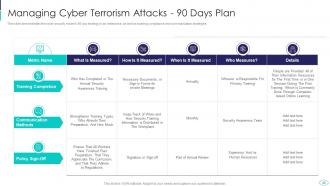
Slide 49: This slide displays cyber security model's 90-day strategy in an enterprise.
Slide 50: This slide represents title for topics that are to be covered next in the template.
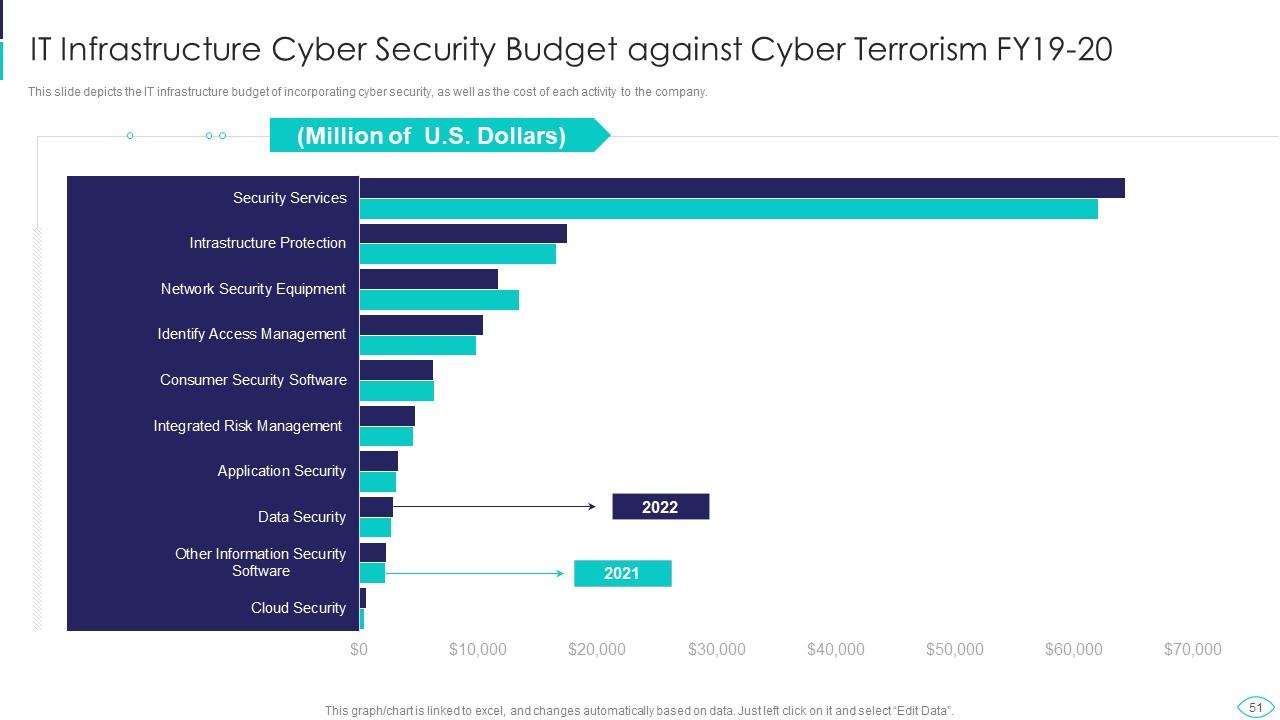
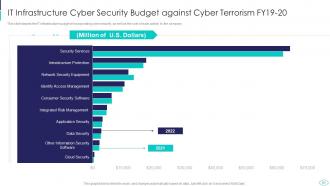
Slide 51: This slide showcases IT infrastructure budget of incorporating cyber security.
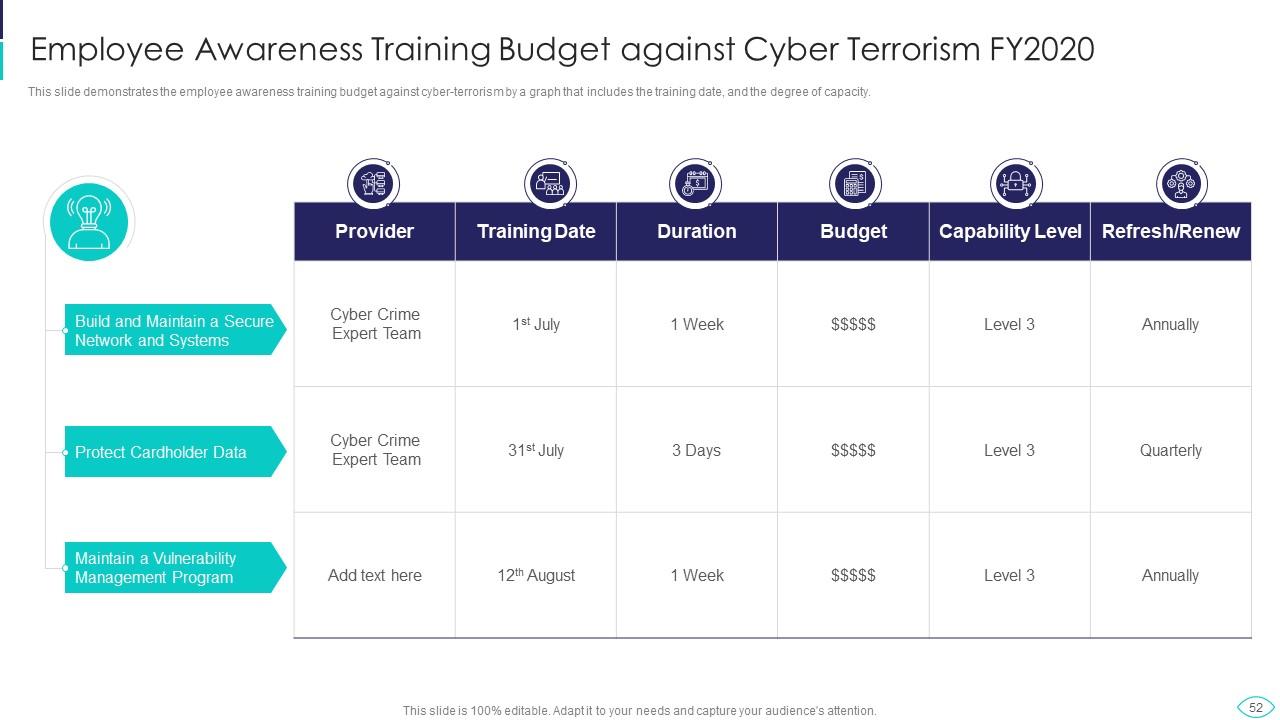
Slide 52: This slide shows Employee Awareness Training Budget against Cyber Terrorism FY2020.
Slide 53: This slide presents title for topics that are to be covered next in the template.
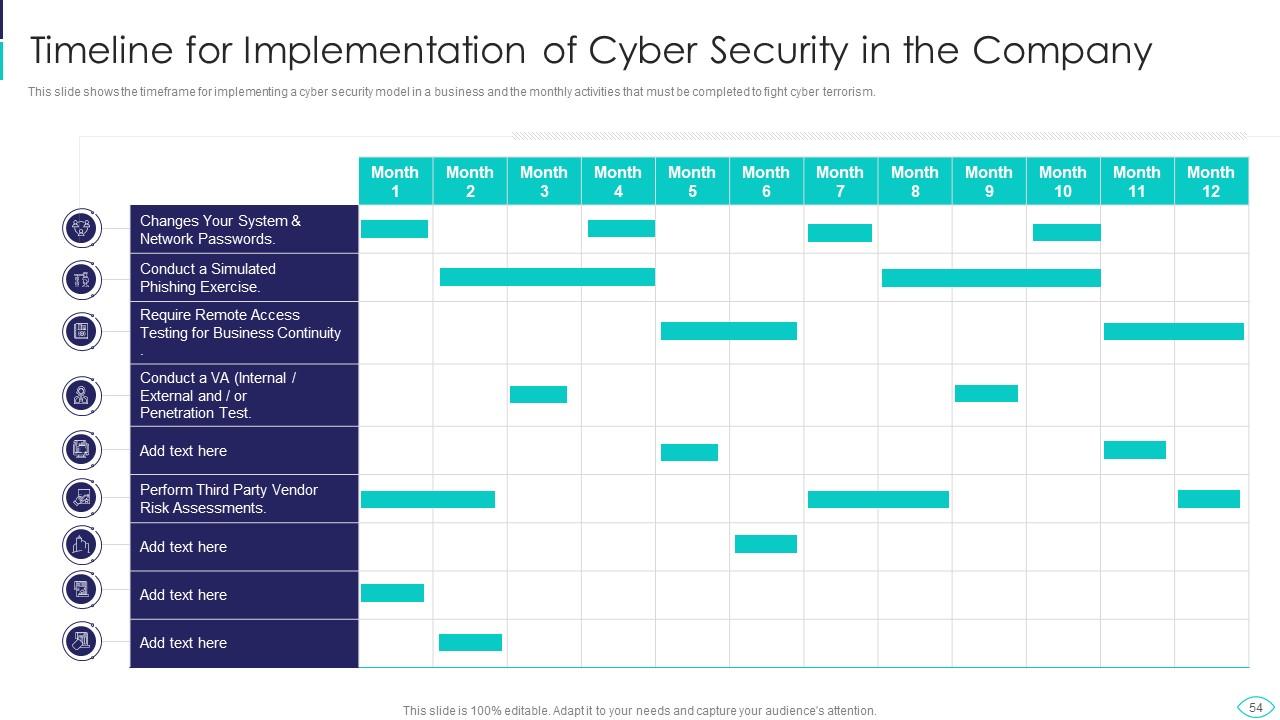
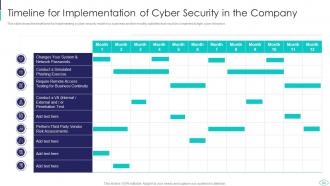
Slide 54: This slide displays Timeline for Implementation of Cyber Security in the Company.
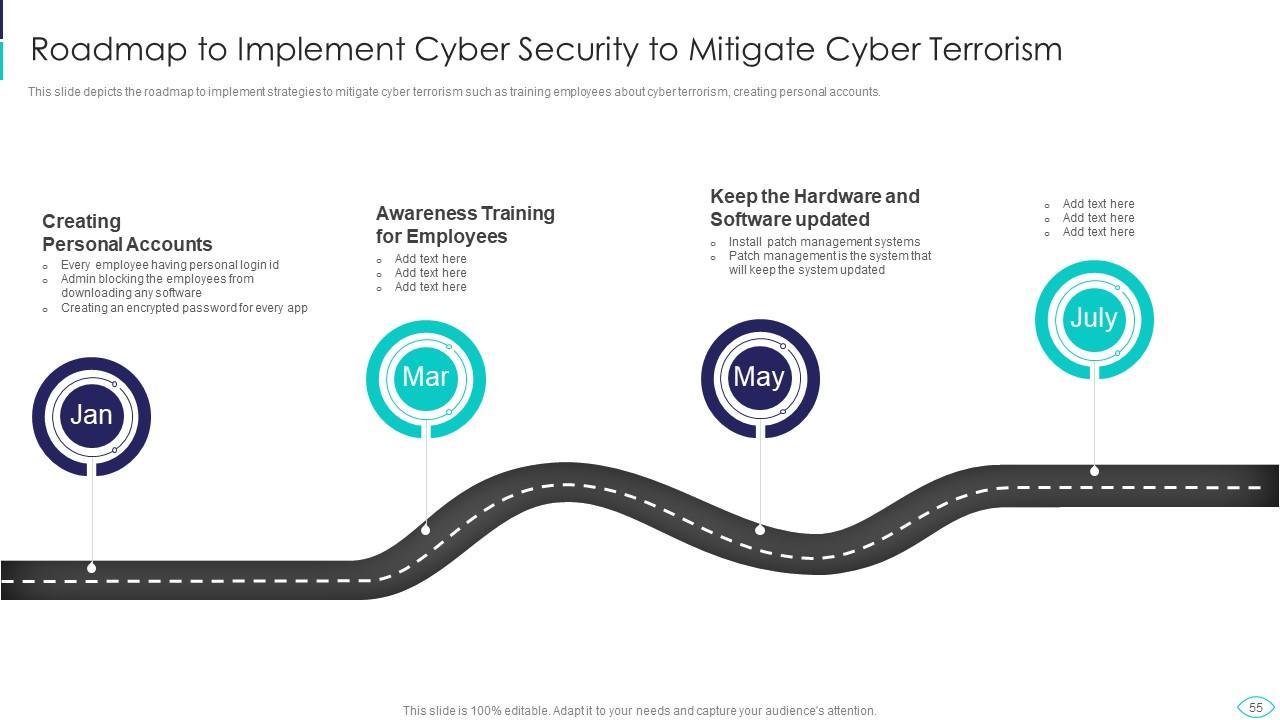
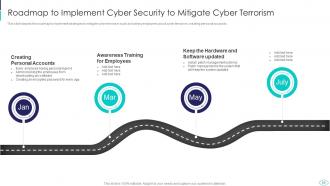
Slide 55: This slide represents Roadmap to Implement Cyber Security to Mitigate Cyber Terrorism.
Slide 56: This slide showcases title for topics that are to be covered next in the template.
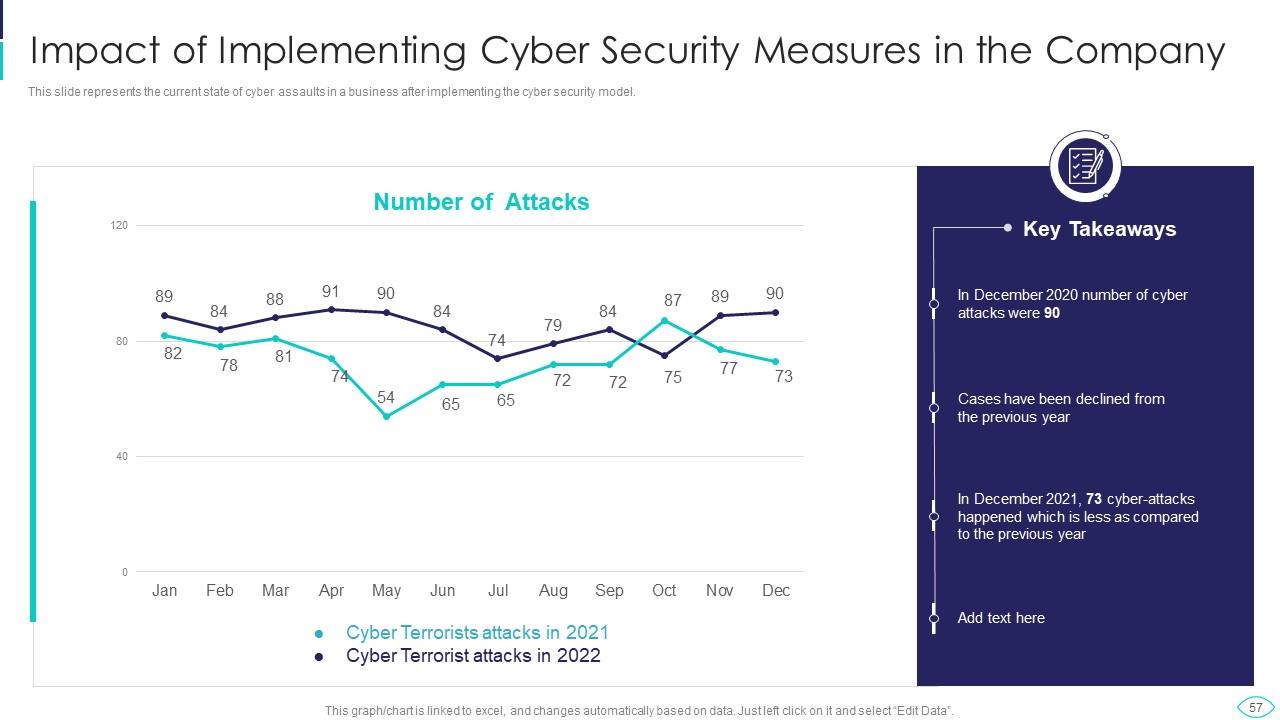
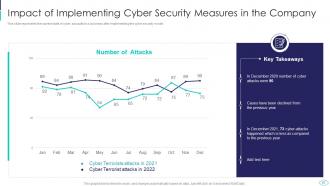
Slide 57: This slide shows Impact of Implementing Cyber Security Measures in the Company.
Slide 58: This slide presents title for topics that are to be covered next in the template.
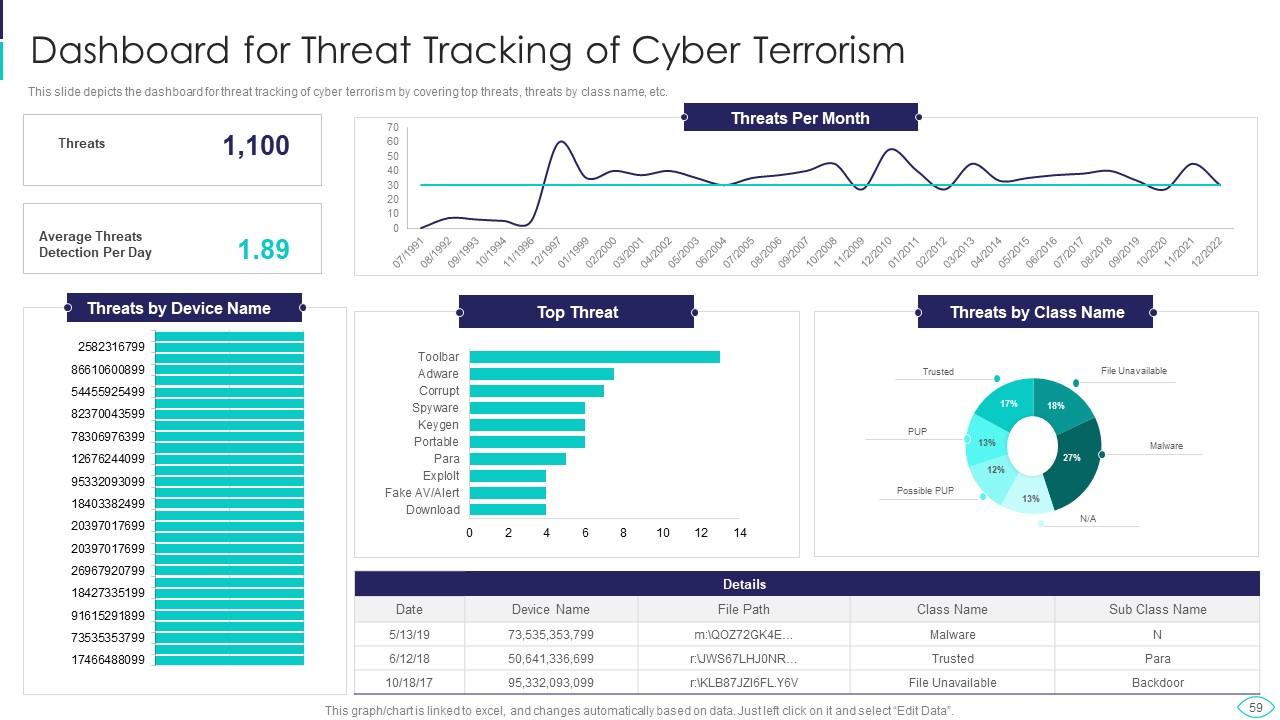
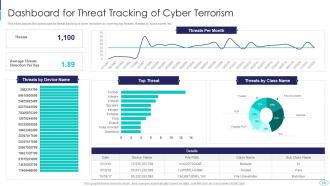
Slide 59: This slide displays dashboard for threat tracking of cyber terrorism by covering top threats, threats by class name, etc.
Slide 60: This slide showcases Icons for Cyber Terrorism Attacks.
Slide 61: This slide is titled as Additional Slides for moving forward.
Slide 62: This slide describes cyber-terrorism and how it is used to access sensitive information.
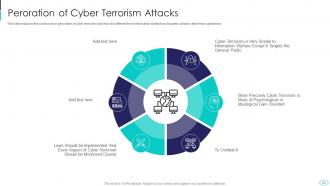
Slide 63: This slide displays Peroration of Cyber Terrorism Attacks.
Slide 64: This is About Us slide to show company specifications etc.
Slide 65: This is Our Target slide. State your targets here.
Slide 66: This slide shows Post It Notes. Post your important notes here.
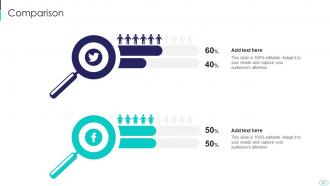
Slide 67: This is a Comparison slide to state comparison between commodities, entities etc.
Slide 68: This is an Idea Generation slide to state a new idea or highlight information, specifications etc.
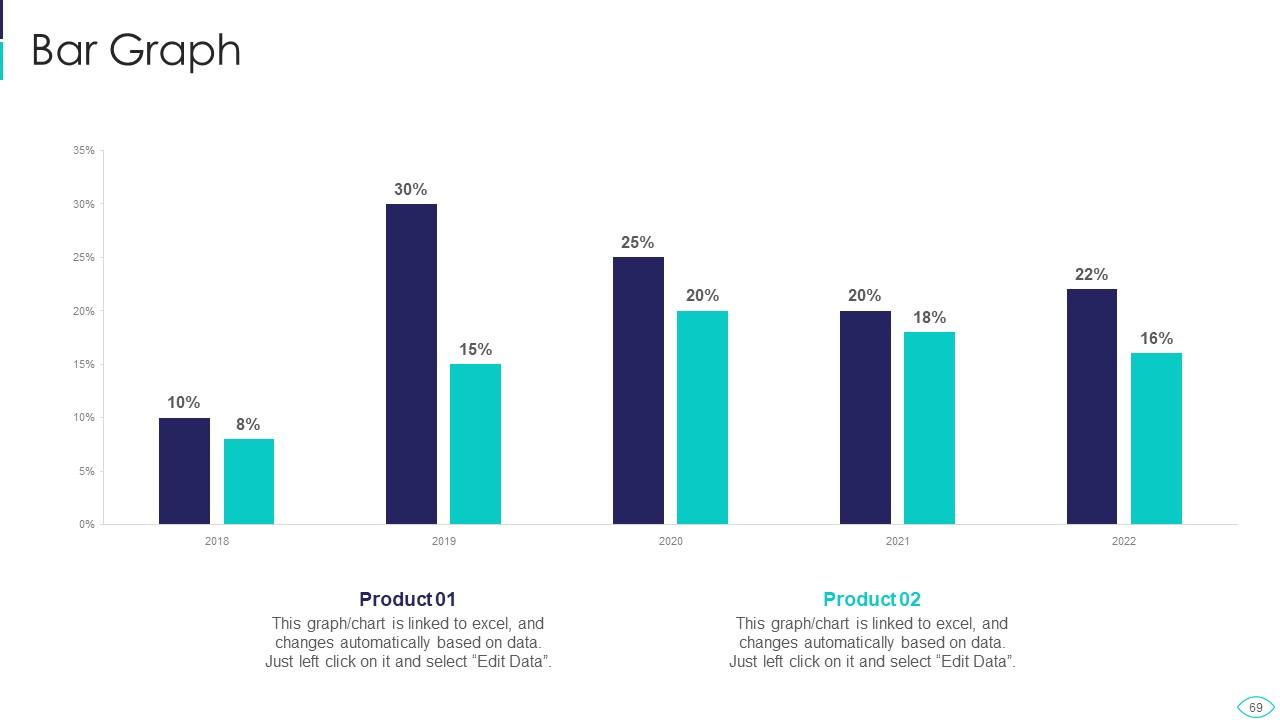
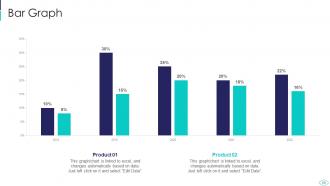
Slide 69: This slide presents Bar chart with two products comparison.
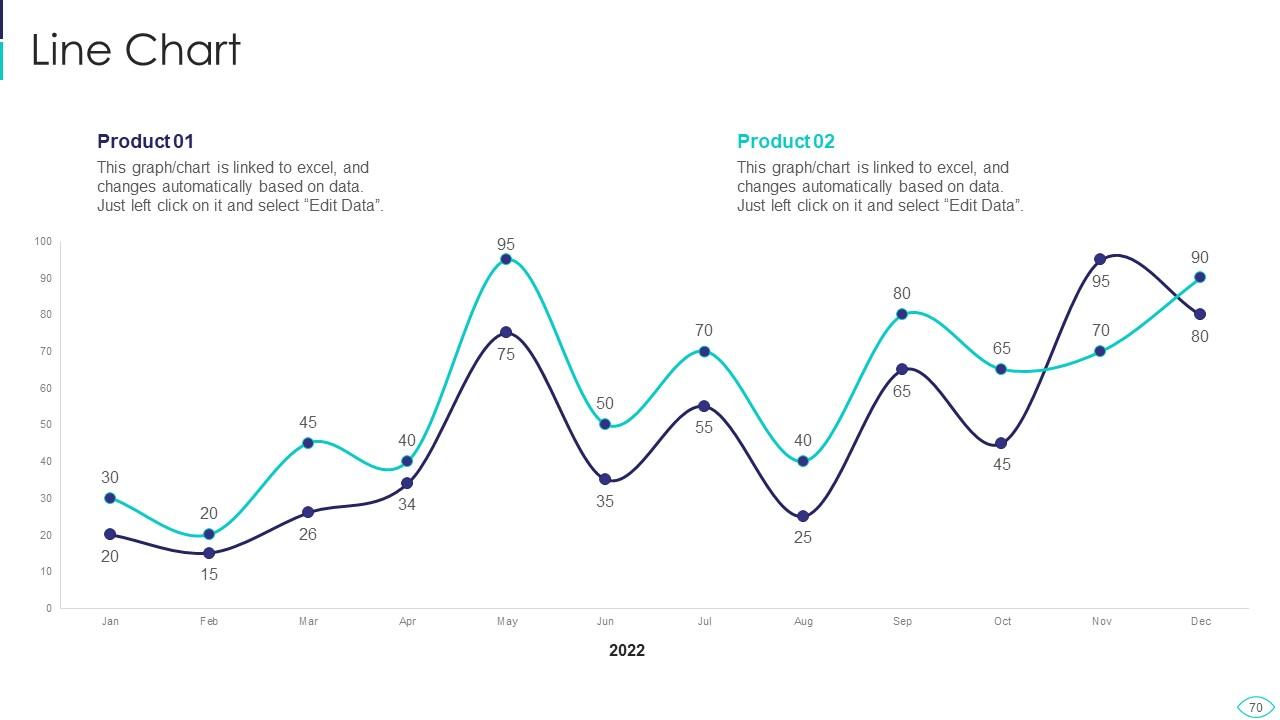
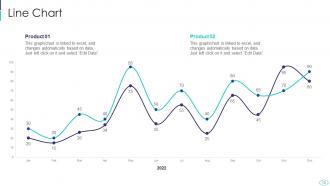
Slide 70: This slide describes Line chart with two products comparison.
Slide 71: This is a Thank You slide with address, contact numbers and email address.
Cyber Terrorism Attacks Powerpoint Presentation Slides with all 76 slides:
Use our Cyber Terrorism Attacks Powerpoint Presentation Slides to effectively help you save your valuable time. They are readymade to fit into any presentation structure.
FAQs
Cyber Terrorism refers to the use of digital attacks, such as hacking, denial of service, and the spread of malware, to cause harm to people, organizations, or governments.
The different types of Cyber Terrorism include privacy violation, network damage, malware, phishing, and Distributed Denial of Service (DDoS) attacks.
Various industries, including health, finance, media, and more, are affected by Cyber Terrorism.
Companies can protect themselves from Cyber Terrorism by implementing IT guidelines, updating hardware and software, installing and updating antivirus software, using strong encrypted passwords, limiting employee access to information, backing up private data, and creating a recovery plan.
Employees can be made aware of Cyber Terrorism through Cyber Terrorism Awareness Programme for Employees and Employee Awareness Training Budget against Cyber Terrorism.
-
“Detailed and great to save your time.”
-
“I always have a wonderful experience with SlideTeam. It's my ""go to"" when I need a template.”