Five years organization cyber security management solution roadmap
Our Five Years Organization Cyber Security Management Solution Roadmap are topically designed to provide an attractive backdrop to any subject. Use them to look like a presentation pro.
Our Five Years Organization Cyber Security Management Solution Roadmap are topically designed to provide an attractive back..
- Google Slides is a new FREE Presentation software from Google.
- All our content is 100% compatible with Google Slides.
- Just download our designs, and upload them to Google Slides and they will work automatically.
- Amaze your audience with SlideTeam and Google Slides.
-
Want Changes to This PPT Slide? Check out our Presentation Design Services
- WideScreen Aspect ratio is becoming a very popular format. When you download this product, the downloaded ZIP will contain this product in both standard and widescreen format.
-

- Some older products that we have may only be in standard format, but they can easily be converted to widescreen.
- To do this, please open the SlideTeam product in Powerpoint, and go to
- Design ( On the top bar) -> Page Setup -> and select "On-screen Show (16:9)” in the drop down for "Slides Sized for".
- The slide or theme will change to widescreen, and all graphics will adjust automatically. You can similarly convert our content to any other desired screen aspect ratio.
Compatible With Google Slides

Get This In WideScreen
You must be logged in to download this presentation.
PowerPoint presentation slides
Presenting Five Years Organization Cyber Security Management Solution Roadmap PowerPoint slide. This PPT slide is available at 4,3 and 16,9 aspect ratios. You can download this PPT theme in various formats like PDF, PNG, and JPG. This PowerPoint template is completely editable and you can modify the font size, font type, and shapes as per your requirements. Our PPT layout is compatible with Google Slides.
People who downloaded this PowerPoint presentation also viewed the following :
Content of this Powerpoint Presentation
Description:
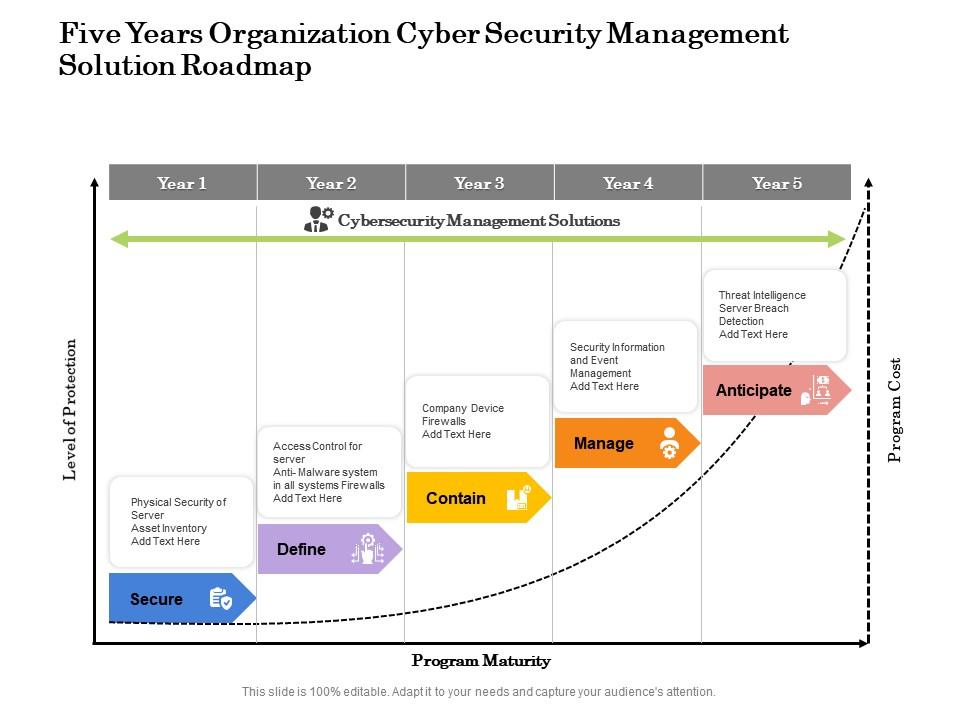
The image is a PowerPoint slide titled "Five Years Organization Cyber Security Management Solution Roadmap." The slide illustrates a five-year strategic plan for enhancing an organization's cybersecurity posture. It's presented as a roadmap with a timeline from Year 1 to Year 5, indicating progressive levels of cyber protection and program maturity.
Key phases of the cybersecurity strategy include:
"Secure" in Year 1, focusing on the physical security of servers and asset inventory.
"Define" in Year 2, which includes implementing access control for servers and anti-malware systems.
"Contain" in Year 3, with actions like deploying company device firewalls.
"Manage" in Year 4, involving security information and event management.
"Anticipate" in Year 5, aiming for advanced measures like threat intelligence and server breach detection.
Each phase is marked with different icons representing the security focus, and there are text placeholders for each step to add specific details. The vertical dotted line indicates the increase in program costs over time as the level of protection escalates.
Use Cases:
Industries where this slide can be effectively utilized:
1. Financial Services:
Use: Protecting against financial cyber threats.
Presenter: Chief Information Security Officer.
Audience: IT Security Team, Company Executives.
2. Healthcare:
Use: Securing patient data and healthcare systems.
Presenter: IT Compliance Manager.
Audience: Healthcare Administrators, Data Protection Officers.
3. Retail:
Use: Safeguarding customer transaction data.
Presenter: Data Security Analyst.
Audience: E-commerce Team, Payment Processors.
4. Technology:
Use: Defending against cyber attacks on technology infrastructure.
Presenter: Network Security Architect.
Audience: Network Team, System Administrators.
5. Government:
Use: Protecting sensitive government data and communications.
Presenter: Cybersecurity Policy Advisor.
Audience: Policy Makers, Security Personnel.
6. Education:
Use: Ensuring the security of educational data and online learning platforms.
Presenter: IT Director.
Audience: School Board, IT Staff.
7. Manufacturing:
Use: Securing industrial control systems and proprietary information.
Presenter: Plant IT Manager.
Audience: Operations Managers, Plant Engineers.
Five years organization cyber security management solution roadmap with all 2 slides:
Use our Five Years Organization Cyber Security Management Solution Roadmap to effectively help you save your valuable time. They are readymade to fit into any presentation structure.
-
Unique research projects to present in meeting.