Information security risk assessment process ppt powerpoint presentation shapes cpb
Our Information Security Risk Assessment Process Ppt Powerpoint Presentation Shapes Cpb are explicit and effective. They combine clarity and concise expression.
Our Information Security Risk Assessment Process Ppt Powerpoint Presentation Shapes Cpb are explicit and effective. They co..
- Google Slides is a new FREE Presentation software from Google.
- All our content is 100% compatible with Google Slides.
- Just download our designs, and upload them to Google Slides and they will work automatically.
- Amaze your audience with SlideTeam and Google Slides.
-
Want Changes to This PPT Slide? Check out our Presentation Design Services
- WideScreen Aspect ratio is becoming a very popular format. When you download this product, the downloaded ZIP will contain this product in both standard and widescreen format.
-

- Some older products that we have may only be in standard format, but they can easily be converted to widescreen.
- To do this, please open the SlideTeam product in Powerpoint, and go to
- Design ( On the top bar) -> Page Setup -> and select "On-screen Show (16:9)” in the drop down for "Slides Sized for".
- The slide or theme will change to widescreen, and all graphics will adjust automatically. You can similarly convert our content to any other desired screen aspect ratio.
Compatible With Google Slides

Get This In WideScreen
You must be logged in to download this presentation.
PowerPoint presentation slides
Presenting this set of slides with name Information Security Risk Assessment Process Ppt Powerpoint Presentation Shapes Cpb. This is an editable Powerpoint five stages graphic that deals with topics like Information Security Risk Assessment Process to help convey your message better graphically. This product is a premium product available for immediate download and is 100 percent editable in Powerpoint. Download this now and use it in your presentations to impress your audience.
People who downloaded this PowerPoint presentation also viewed the following :
Related Products
Content of this Powerpoint Presentation
Description:
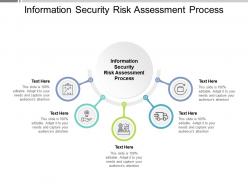
The image features a PowerPoint slide designed for presenting an Information Security Risk Assessment Process. It comprises a structured layout with a central title and four surrounding circles, each linked to the center. These elements convey a systematic process to be discussed. Within each circle, there is an associated icon representing different aspects or steps of the risk assessment process. Beneath each icon, a placeholder text, "Text Here," is provided, enabling presenters to insert specific information or details related to each step or aspect under consideration. Additionally, a reminder at the bottom of the slide emphasizes its complete editability, encouraging users to tailor it to suit their precise presentation needs and effectively engage the audience.
Use Cases:
This versatile slide template is suitable for various industry settings where information security and risk assessment are of paramount importance. Here are seven industry sectors where this slide can be effectively utilized:
1. Finance:
Use: Outlining steps for identifying and mitigating financial data risks.
Presenter: Chief Information Security Officer (CISO) or IT security expert.
Audience: Financial analysts, bank managers, and IT security teams.
2. Healthcare:
Use: Educating on protecting patient records and ensuring compliance with health data regulations.
Presenter: IT Security Manager or Healthcare Compliance Officer.
Audience: Healthcare administrators, medical staff, and compliance teams.
3. Government:
Use: Presenting strategies for safeguarding sensitive government data and enhancing cybersecurity.
Presenter: Director of Government Cybersecurity or Chief Information Officer (CIO).
Audience: Policy makers, government officials, and security personnel.
4. Technology:
Use: Illustrating the protection of intellectual property and customer data.
Presenter: Chief Technical Officer (CTO) or Information Security Director.
Audience: Product developers, data management teams, and IT professionals.
5. Education:
Use: Demonstrating how to protect student information systems and research data.
Presenter: Director of Information Technology or IT Security Coordinator.
Audience: Educational administrators, IT staff, and faculty members.
6. Retail:
Use: Discussing the secure handling of customer transactions and data.
Presenter: Head of Retail Risk Management or Security Analyst.
Audience: Customer service managers, security analysts, and retail staff.
7. Manufacturing:
Use: Outlining how to secure industrial control systems and protect trade secrets.
Presenter: Industrial Cybersecurity Specialist or Plant Security Manager.
Audience: Plant managers, engineers, and operational staff.
Information security risk assessment process ppt powerpoint presentation shapes cpb with all 2 slides:
Give your audience a fulfilling experience. They will find our Information Security Risk Assessment Process Ppt Powerpoint Presentation Shapes Cpb elevating.
No Reviews