Data Management PowerPoint Templates, Big Data PPT Slides, and Presentation Graphics
- Sub Categories
-
- 30 60 90 Day Plan
- About Us Company Details
- Action Plan
- Agenda
- Annual Report
- Audit Reports
- Balance Scorecard
- Brand Equity
- Business Case Study
- Business Communication Skills
- Business Plan Development
- Business Problem Solving
- Business Review
- Capital Budgeting
- Career Planning
- Change Management
- Color Palettes
- Communication Process
- Company Location
- Company Vision
- Compare
- Competitive Analysis
- Corporate Governance
- Cost Reduction Strategies
- Custom Business Slides
- Customer Service
- Dashboard
- Data Management
- Decision Making
- Digital Marketing Strategy
- Digital Transformation
- Disaster Management
- Diversity
- Equity Investment
- Financial Analysis
- Financial Services
- Financials
- Growth Hacking Strategy
- Human Resource Management
- Innovation Management
- Interview Process
- Knowledge Management
- Leadership
- Lean Manufacturing
- Legal Law Order
- Management
- Market Segmentation
- Marketing
- Media and Communication
- Meeting Planner
- Mergers and Acquisitions
- Metaverse
- Newspapers
- Operations and Logistics
- Organizational Structure
- Our Goals
- Performance Management
- Pitch Decks
- Pricing Strategies
- Process Management
- Product Development
- Product Launch Ideas
- Product Portfolio
- Project Management
- Purchasing Process
- Quality Assurance
- Quotes and Testimonials
- Real Estate
- Risk Management
- Sales Performance Plan
- Sales Review
- SEO
- Service Offering
- Six Sigma
- Social Media and Network
- Software Development
- Solution Architecture
- Stock Portfolio
- Strategic Management
- Strategic Planning
- Supply Chain Management
- Swimlanes
- System Architecture
- Team Introduction
- Testing and Validation
- Thanks-FAQ
- Time Management
- Timelines Roadmaps
- Value Chain Analysis
- Value Stream Mapping
- Workplace Ethic
-
 Point In Time Copies As A Type Of Disaster Recovery Training Ppt
Point In Time Copies As A Type Of Disaster Recovery Training PptPresenting Point in Time Copies as a Type of Disaster Recovery. This PPT presentation is thoroughly researched and each slide consists of appropriate content. Designed by PowerPoint specialists, this PPT is fully customizable alter the colors, text, icons, and font size to meet your needs. Compatible with Google Slides and backed by superior customer support. Download today to deliver your presentation confidently.
-
 Instant Recovery As A Type Of Disaster Recovery Training Ppt
Instant Recovery As A Type Of Disaster Recovery Training PptPresenting Instant Recovery as a Type of Disaster Recovery. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 Different Reasons Behind Cyber Attacks Training Ppt
Different Reasons Behind Cyber Attacks Training PptPresenting Different Reasons Behind Cyber Attacks. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
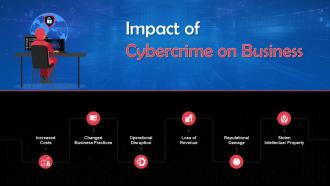 Overview Of Business Impact Of Cybercrime Training Ppt
Overview Of Business Impact Of Cybercrime Training PptPresenting Overview of Business Impact of Cybercrime. This PPT presentation is meticulously researched and each slide consists of relevant content. Designed by SlideTeams PowerPoint experts, this PPT is fully customizable alter the colors, text, icons, and font size to meet your requirements. Compatible with Google Slides and backed by excellent customer support. Download to present with poise and assurance.
-
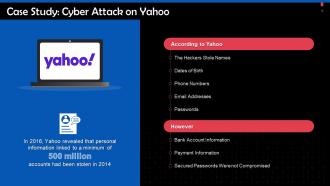 Cyber Attack On Yahoo Case Study Training Ppt
Cyber Attack On Yahoo Case Study Training PptPresenting Cyber Attack on Yahoo Case Study. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 Spear Phishing As A Type Of Phishing Attack Training Ppt
Spear Phishing As A Type Of Phishing Attack Training PptPresenting Spear Phishing as a Type of Phishing Attack. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 Malware As A Type Of Cyber Threat Training Ppt
Malware As A Type Of Cyber Threat Training PptPresenting Malware as a Type of Cyber Threat. This PPT presentation is meticulously researched and each slide consists of relevant content. Designed by SlideTeams PowerPoint experts, this PPT is fully customizable alter the colors, text, icons, and font size to meet your requirements. Compatible with Google Slides and backed by excellent customer support. Download to present with poise and assurance.
-
 Ways Of Spreading Malware Infections Training Ppt
Ways Of Spreading Malware Infections Training PptPresenting Ways of Spreading Malware Infections. This PPT presentation is thoroughly researched and each slide consists of appropriate content. Designed by PowerPoint specialists, this PPT is fully customizable alter the colors, text, icons, and font size to meet your needs. Compatible with Google Slides and backed by superior customer support. Download today to deliver your presentation confidently.
-
 Different Types Of Malware Training Ppt
Different Types Of Malware Training PptPresenting Different Types of Malware. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 Malware Infections On Mobile Devices Training Ppt
Malware Infections On Mobile Devices Training PptPresenting Malware Infections on Mobile Devices. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
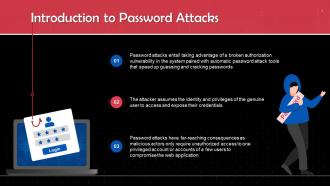 Password Attacks In Cyber Security Training Ppt
Password Attacks In Cyber Security Training PptPresenting Password Attacks in Cyber Security. This PPT presentation is thoroughly researched and each slide consists of appropriate content. Designed by PowerPoint specialists, this PPT is fully customizable alter the colors, text, icons, and font size to meet your needs. Compatible with Google Slides and backed by superior customer support. Download today to deliver your presentation confidently.
-
 Tips To Prevent Password Attacks Training Ppt
Tips To Prevent Password Attacks Training PptPresenting Tips to Prevent Password Attacks. This PPT presentation is meticulously researched and each slide consists of relevant content. Designed by SlideTeams PowerPoint experts, this PPT is fully customizable alter the colors, text, icons, and font size to meet your requirements. Compatible with Google Slides and backed by excellent customer support. Download to present with poise and assurance.
-
 Password Training In Organizations To Prevent Password Attacks Training Ppt
Password Training In Organizations To Prevent Password Attacks Training PptPresenting Password Training in Organizations to Prevent Password Attacks. This PPT presentation is thoroughly researched and each slide consists of appropriate content. Designed by PowerPoint specialists, this PPT is fully customizable alter the colors, text, icons, and font size to meet your needs. Compatible with Google Slides and backed by superior customer support. Download today to deliver your presentation confidently.
-
 SQL Injection In Cybersecurity Training Ppt
SQL Injection In Cybersecurity Training PptPresenting SQL Injection in Cybersecurity. This PPT presentation is thoroughly researched and each slide consists of appropriate content. Designed by PowerPoint specialists, this PPT is fully customizable alter the colors, text, icons, and font size to meet your needs. Compatible with Google Slides and backed by superior customer support. Download today to deliver your presentation confidently.
-
 Social Engineering Attacks In Cybersecurity Training Ppt
Social Engineering Attacks In Cybersecurity Training PptPresenting Social Engineering Attacks in Cybersecurity. This PPT presentation is thoroughly researched and each slide consists of appropriate content. Designed by PowerPoint specialists, this PPT is fully customizable alter the colors, text, icons, and font size to meet your needs. Compatible with Google Slides and backed by superior customer support. Download today to deliver your presentation confidently.
-
 Types Of Social Engineering Techniques Training Ppt
Types Of Social Engineering Techniques Training PptPresenting Types of Social Engineering Techniques. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
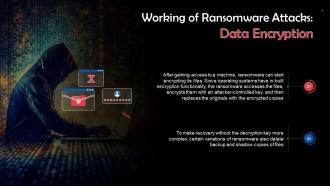 Data Encryption In Ransomware Attacks Training Ppt
Data Encryption In Ransomware Attacks Training PptPresenting Data Encryption in Ransomware Attacks. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 Differences Between Malvertising And Adware Training Ppt
Differences Between Malvertising And Adware Training PptPresenting Differences Between Malvertising and Adware. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 Physical Security And Environmental Controls In Cybersecurity Training Ppt
Physical Security And Environmental Controls In Cybersecurity Training PptPresenting Physical Security and Environmental Controls in Cybersecurity. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 Backup Policy And Its Importance Training Ppt
Backup Policy And Its Importance Training PptPresenting Backup Policy and its Importance. This PPT presentation is meticulously researched and each slide consists of relevant content. Designed by SlideTeams PowerPoint experts, this PPT is fully customizable alter the colors, text, icons, and font size to meet your requirements. Compatible with Google Slides and backed by excellent customer support. Download to present with poise and assurance.
-
 Backup And Restoration Procedure Essentials Training Ppt
Backup And Restoration Procedure Essentials Training PptPresenting Backup and Restoration Procedure Essentials. This PPT presentation is thoroughly researched and each slide consists of appropriate content. Designed by PowerPoint specialists, this PPT is fully customizable alter the colors, text, icons, and font size to meet your needs. Compatible with Google Slides and backed by superior customer support. Download today to deliver your presentation confidently.
-
 Data Retention Policy Or Matrix Training Ppt
Data Retention Policy Or Matrix Training PptPresenting Data Retention Policy or Matrix. This PPT presentation is meticulously researched and each slide consists of relevant content. Designed by SlideTeams PowerPoint experts, this PPT is fully customizable alter the colors, text, icons, and font size to meet your requirements. Compatible with Google Slides and backed by excellent customer support. Download to present with poise and assurance.
-
 Working Of Cyber Insurance Training Ppt
Working Of Cyber Insurance Training PptPresenting Working of Cyber Insurance. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 Overview Of Identity Access Management Policy Training Ppt
Overview Of Identity Access Management Policy Training PptPresenting Overview of Identity Access Management Policy. This PPT presentation is meticulously researched and each slide consists of relevant content. Designed by SlideTeams PowerPoint experts, this PPT is fully customizable alter the colors, text, icons, and font size to meet your requirements. Compatible with Google Slides and backed by excellent customer support. Download to present with poise and assurance.
-
 Security Awareness And Training Policy Training Ppt
Security Awareness And Training Policy Training PptPresenting Security Awareness and Training Policy. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 Binary digits flow data streams layout
Binary digits flow data streams layoutPresenting this set of slides with name - Binary Digits Flow Data Streams Layout. This is a one stage process. The stages in this process are Data Stream, Binary Code, Binary Data.
-
 Data stream multiple waves transfer layout
Data stream multiple waves transfer layoutPresenting this set of slides with name - Data Stream Multiple Waves Transfer Layout. This is a four stage process. The stages in this process are Data Stream, Binary Code, Binary Data.
-
 4 steps data profiling icon
4 steps data profiling iconPresenting this set of slides with name - 4 Steps Data Profiling Icon. This is a four stage process. The stages in this process are Data Profiling, Data Management, Data Examination.
-
 6 steps data profiling icon
6 steps data profiling iconPresenting this set of slides with name - 6 Steps Data Profiling Icon. This is a six stage process. The stages in this process are Data Profiling, Data Management, Data Examination.
-
 Six steps process with data icon in center
Six steps process with data icon in centerPresenting this set of slides with name - Six Steps Process With Data Icon In Center. This is a six stage process. The stages in this process are Data Profiling, Data Management, Data Examination.
-
 Data cleaning using circles and dotted lines
Data cleaning using circles and dotted linesPresenting this set of slides with name - Data Cleaning Using Circles And Dotted Lines. This is a two stage process. The stages in this process are Data Cleaning, Data Management, Data Cleansing.
-
 Data mapping connecting circular links chart icons
Data mapping connecting circular links chart iconsPresenting this set of slides with name - Data Mapping Connecting Circular Links Chart Icons. This is a three stage process. The stages in this process are Data Preparation, Data Management, Data Mapping.
-
 Data mapping icon with three horizontal layers and connecting dots
Data mapping icon with three horizontal layers and connecting dotsPresenting this set of slides with name - Data Mapping Icon With Three Horizontal Layers And Connecting Dots. This is a three stage process. The stages in this process are Data Preparation, Data Management, Data Mapping.
-
 Payment security and fraud management market entry report transformation
Payment security and fraud management market entry report transformationFrom prevention to detection and resolution, data fraud management solutions allow you to leverage proven technologies to create customized strategies that help limit losses while maintaining a high level of customer satisfaction. Increase audience engagement and knowledge by dispensing information using Payment Security And Fraud Management Market Entry Report Transformation. This template helps you present information on three stages. You can also present information on Market Basket Analysis, Customer ID Analysis, Device Fingerprinting, Geolocation Analysis using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Overview Of Components Of Cybersecurity Training Ppt
Overview Of Components Of Cybersecurity Training PptPresenting Overview of Components of Cybersecurity. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 Information Security Policy In Cybersecurity Training Ppt
Information Security Policy In Cybersecurity Training PptPresenting Information Security Policy in Cybersecurity. This PPT presentation is meticulously researched and each slide consists of relevant content. Designed by SlideTeams PowerPoint experts, this PPT is fully customizable alter the colors, text, icons, and font size to meet your requirements. Compatible with Google Slides and backed by excellent customer support. Download to present with poise and assurance.
-
 Application Security Controls In Cybersecurity Training Ppt
Application Security Controls In Cybersecurity Training PptPresenting Application Security Controls in Cybersecurity. This PPT presentation is thoroughly researched and each slide consists of appropriate content. Designed by PowerPoint specialists, this PPT is fully customizable alter the colors, text, icons, and font size to meet your needs. Compatible with Google Slides and backed by superior customer support. Download today to deliver your presentation confidently.
-
 Preventative Controls In Application Security Training Ppt
Preventative Controls In Application Security Training PptPresenting Preventative Controls in Application Security. This PPT presentation is meticulously researched and each slide consists of relevant content. Designed by SlideTeams PowerPoint experts, this PPT is fully customizable alter the colors, text, icons, and font size to meet your requirements. Compatible with Google Slides and backed by excellent customer support. Download to present with poise and assurance.
-
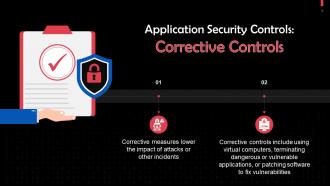 Corrective Controls In Application Security Training Ppt
Corrective Controls In Application Security Training PptPresenting Corrective Controls in Application Security. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 Detective Controls In Application Security Training Ppt
Detective Controls In Application Security Training PptPresenting Detective Controls in Application Security. This PPT presentation is thoroughly researched and each slide consists of appropriate content. Designed by PowerPoint specialists, this PPT is fully customizable alter the colors, text, icons, and font size to meet your needs. Compatible with Google Slides and backed by superior customer support. Download today to deliver your presentation confidently.
-
 Denial Of Service DoSas An Application Security Risk Training Ppt
Denial Of Service DoSas An Application Security Risk Training PptPresenting Denial of Service DoSas an Application Security Risk. This PPT presentation is thoroughly researched and each slide consists of appropriate content. Designed by PowerPoint specialists, this PPT is fully customizable alter the colors, text, icons, and font size to meet your needs. Compatible with Google Slides and backed by superior customer support. Download today to deliver your presentation confidently.
-
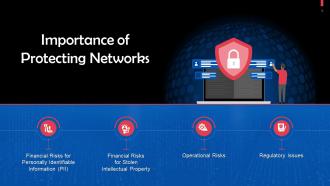 Most Important Reasons For Network Security Training Ppt
Most Important Reasons For Network Security Training PptPresenting Most Important Reasons for Network Security. This PPT presentation is meticulously researched and each slide consists of relevant content. Designed by SlideTeams PowerPoint experts, this PPT is fully customizable alter the colors, text, icons, and font size to meet your requirements. Compatible with Google Slides and backed by excellent customer support. Download to present with poise and assurance.
-
 Anti Virus And Anti Malware Software For Network Security Training Ppt
Anti Virus And Anti Malware Software For Network Security Training PptPresenting Anti-virus and Anti-malware Software for Network Security. This PPT presentation is thoroughly researched and each slide consists of appropriate content. Designed by PowerPoint specialists, this PPT is fully customizable alter the colors, text, icons, and font size to meet your needs. Compatible with Google Slides and backed by superior customer support. Download today to deliver your presentation confidently.
-
 Network Segmentation As A Type Of Network Security Training Ppt
Network Segmentation As A Type Of Network Security Training PptPresenting Network Segmentation as a Type of Network Security. This PPT presentation is meticulously researched and each slide consists of relevant content. Designed by SlideTeams PowerPoint experts, this PPT is fully customizable alter the colors, text, icons, and font size to meet your requirements. Compatible with Google Slides and backed by excellent customer support. Download to present with poise and assurance.
-
 Virtual Private Network VPN For Network Security Training Ppt
Virtual Private Network VPN For Network Security Training PptPresenting Virtual Private Network VPN for Network Security. This PPT presentation is meticulously researched and each slide consists of relevant content. Designed by SlideTeams PowerPoint experts, this PPT is fully customizable alter the colors, text, icons, and font size to meet your requirements. Compatible with Google Slides and backed by excellent customer support. Download to present with poise and assurance.
-
 Sandboxing As A Type Of Network Security Training Ppt
Sandboxing As A Type Of Network Security Training PptPresenting Sandboxing as a Type of Network Security. This PPT presentation is meticulously researched and each slide consists of relevant content. Designed by SlideTeams PowerPoint experts, this PPT is fully customizable alter the colors, text, icons, and font size to meet your requirements. Compatible with Google Slides and backed by excellent customer support. Download to present with poise and assurance.
-
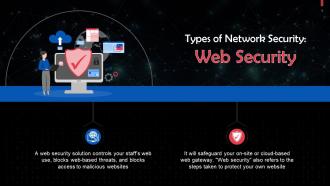 Web Security As A Type Of Network Security Training Ppt
Web Security As A Type Of Network Security Training PptPresenting Web Security as a Type of Network Security. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 End User Security As A Component Of Cybersecurity Training Ppt
End User Security As A Component Of Cybersecurity Training PptPresenting End User Security as a Component of Cybersecurity. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 Detection As An Element Of Endpoint Security Training Ppt
Detection As An Element Of Endpoint Security Training PptPresenting Detection as an Element of Endpoint Security. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
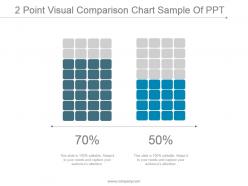 2 point visual comparison chart sample of ppt
2 point visual comparison chart sample of pptPresenting 2 point visual comparison chart sample of ppt. This is a 2 point visual comparison chart sample of ppt. This is a two stage process. The stages in this process are business, comparison, percentage, strategy, finance, success.
-
 Backup upload and download from cloud
Backup upload and download from cloudPresenting backup upload and download from cloud. This is a backup upload and download from cloud. This is a four stage process. The stages in this process are backup, recovery, database.
-
 Content page with four contents
Content page with four contentsPresenting this Content Page with Four Contents PowerPoint presentation. Transform this into common images or document formats like JPEG and PDF. It supports both the standard and widescreen viewing angles. It is also compatible with Google Slides and MS PowerPoint. Alter the style, size, background and other attributes of the PPT. High-quality graphics will ensure that picture quality always remains the same.
-
 Data landscape unstructured semi structured structured data
Data landscape unstructured semi structured structured dataPresenting data landscape unstructured semi structured structured data. This is a data landscape unstructured semi structured structured data. This is a three stage process. The stages in this process are data landscape, big data machine learning, artificial intelligence.
-
 Icon table blue grid cells management
Icon table blue grid cells managementPresenting icon table blue grid cells management. This is a icon table blue grid cells management. This is a six stage process. The stages in this process are icon table, database icon, table grid icon.
-
 Data model with employee and city lookup
Data model with employee and city lookupPresenting, with our data model with employee and city lookup PPT deck. Effective use of colors and pattern. Eye catchy visuals. Images are of great resolution. No fear of pixilation when thrown on a wide screen. Fit with a large number of online and offline software options. Suitable with numerous format options. Completely editable slide. Include or exclude the content in a snap. Personalize the exhibition with business name and logo or company trademark.
-
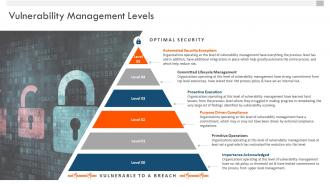 Vulnerability management whitepaper vulnerability management levels ppt styles show
Vulnerability management whitepaper vulnerability management levels ppt styles showIntroducing Vulnerability Management Whitepaper Vulnerability Management Levels Ppt Styles Show to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Automated Security Ecosystem, Committed Lifecycle Management, Proactive Execution, Purpose Driven Compliance, Primitive Operations, Importance Acknowledged, using this template. Grab it now to reap its full benefits.
-
 Data analytics process circular diagrams ppt slides
Data analytics process circular diagrams ppt slidesPresenting data analytics process circular diagrams ppt slides. This is a data analytics process circular diagrams ppt slides. This is a four stage process. The stages in this process are data analytics process, data, insight, decision, info.
-
 Data center bases with hybrid cloud ppt images gallery
Data center bases with hybrid cloud ppt images galleryPresenting Data Center Bases With Hybrid Cloud PPT. Made up of high-resolution graphics. Easy to download and can be saved in a variety of formats. Access to open on a widescreen preview. Compatible with the Google Slides and PowerPoint software. Edit the style, size, and the background of the slide icons as per your needs. Useful for business owners, students, and managers. It can be viewed on a standard screen and widescreen without any fear of pixelation.
-
 Document management sample ppt summary
Document management sample ppt summaryPresenting Document Management Sample PPT Summary which is professionally designed for your convenience. The template is compatible with Google Slides, which makes it accessible at once. The template is readily available in both standard and widescreen. Edit the fonts, colors, font type, and font size of the slide as per your requirements. You can open and save your presentation in various formats like PDF, JPG, and PNG.
-
 Data integration hub ppt infographics
Data integration hub ppt infographicsPresenting Data Integration Hub PPT Infographics which is fully editable. The slide is easily available in both 4:3 and 16:9 aspect ratio. This template is adaptable with Google Slides which makes it accessible at once. Save your presentation in various formats like PDF, JPG, and PNG. Modify the color, font, font size, and font types of the slides as per your requirement.