Diagrams on Computer Networking security hacking DDOS attacks
- Sub Categories
-
 Internal security steps pyramid for laptop ppt slides
Internal security steps pyramid for laptop ppt slidesQuick and easy to download free of any hassles. Fully editable text to suit the context. Absolutely modifiable PPT infographics- change the color and contrast. Alter the size and orientation of presentation images to your liking. Add company logo, tagline, trademark or brand name etc. Fit this slide seamlessly anywhere perfectly within your own presentation.The stages in this process are security.
-
 Ppt strategy is and idea powerpoint slide presentation examples
Ppt strategy is and idea powerpoint slide presentation examplesPresenting ppt strategy is and idea powerpoint slide presentation examples. This is a strategy is and idea powerpoint slide presentation examples. This is a four stage process. The stages in this process are strategy is and idea, goal can be achieved, communication strategies, develop key messages.
-
 Key steps for solution recommended to solve business problem
Key steps for solution recommended to solve business problemPresenting this set of slides with name Key Steps For Solution Recommended To Solve Business Problem. This is a six stage process. The stages in this process are Implement, Evaluate, Develop. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Hw four staged key banners and lock diagram flat powerpoint design
Hw four staged key banners and lock diagram flat powerpoint designPresenting hw four staged key banners and lock diagram flat powerpoint design. Four staged key design banners and lock diagram has been used to design this PPT diagram. This PPT diagram contains the concept of business safety features representation. Use this PPT diagram for business and marketing related presentations.
-
 1114 multiple keys for success in business powerpoint template
1114 multiple keys for success in business powerpoint templateWe are proud to present our 1114 multiple keys for success in business powerpoint template. This Power Point template slide has been designed with graphic of multiple keys. This unique PPT slide can be used for success concept. Use this PPT slide for your business and marketing presentations.
-
 Cyber security icon with lock and computer
Cyber security icon with lock and computerPresenting this set of slides with name Cyber Security Icon With Lock And Computer. This is a two stage process. The stages in this process are Cyber Security Icon With Lock And Computer. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Data and business network security techniques ppt slides
Data and business network security techniques ppt slidesPresenting data and business network security techniques ppt slides. This is a data and business network security techniques ppt slides. This is a one stage process. The stages in this process are security.
-
 Three Lines Of Defense Model For Cyber Security
Three Lines Of Defense Model For Cyber SecurityThis slide represents the cyber security and governance lines of defense model. It includes functions of the three lines of defense such as policies, procedures and standards documentation, penetration testing, review policies and procedures, conduct cyber risk assessments etc. Presenting our set of slides with Three Lines Of Defense Model For Cyber Security. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Processes, Data Classification, Risk Assessments.
-
 Icon Highlighting Cybersecurity In Education Industry
Icon Highlighting Cybersecurity In Education IndustryPresenting our set of slides with Icon Highlighting Cybersecurity In Education Industry. This exhibits information on Three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Icon Highlighting Cybersecurity,In Education Industry
-
 Golden lock with chain for safety powerpoint template
Golden lock with chain for safety powerpoint templateWe are proud to present our golden lock with chain for safety powerpoint template. Concept of safety has been displayed in this professional PPT diagram. This PPT diagram contains the graphic of golden lock and chain. Use this PPT diagram for business and marketing related presentations.
-
 Security roadmap with finger print
Security roadmap with finger printPresenting this set of slides with name - Security Roadmap With Finger Print. This is a four stage process. The stages in this process are Security Roadmap, Security Timeline, Safer Roadmap.
-
 User icon depicting secured personal account
User icon depicting secured personal accountPresenting our set of slides with User Icon Depicting Secured Personal Account. This exhibits information on one stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on User Icon Depicting Secured Personal Account.
-
 Fo multiple icons and lock for internet security powerpoint template
Fo multiple icons and lock for internet security powerpoint templatePresenting fo multiple icons and lock for internet security powerpoint template. This Power Point template diagram has been crafted with graphic of multiple icons and lock. This PPT diagram contains the concept of internet security representation. Use this PPT diagram for business and technology related presentations.
-
 Hi two human head with keyholes and key in hand powerpoint template
Hi two human head with keyholes and key in hand powerpoint templateThoroughly editable content. Personalize the content with company name and logo. Compatibility across various software versions available online and offline. Easy conversion into varied format. Aboriginal designs used for crafting the slide background. Professionally equipped and articulated set of information. Tailor fit the content as per individual need and organization. Advantageous for financial resource team, team leader, team members, company head, students and professors.
-
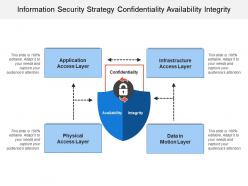 Information security strategy confidentiality availability integrity
Information security strategy confidentiality availability integrityPresenting this set of slides with name - Information Security Strategy Confidentiality Availability Integrity. This is a four stage process. The stages in this process are Information Security Strategy, Information Security Plan, Information Protection Strategy.
-
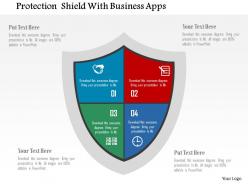 Protection shield with business apps flat powerpoint design
Protection shield with business apps flat powerpoint designWe are proud to present our protection shield with business apps flat powerpoint design. This power point template diagram has been crafted with graphic of protection shield. This PPT diagram contains the concept of safety and security. Use this PPT diagram for business application and create an impact.
-
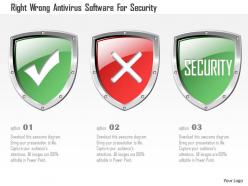 Right wrong antivirus software for security ppt slides
Right wrong antivirus software for security ppt slidesPresenting right wrong antivirus software for security ppt slides. This is a right wrong antivirus software for security ppt slides. This is a three stage process. The stages in this process are security.
-
 Lk house with six boxes and icons and key flat powerpoint design
Lk house with six boxes and icons and key flat powerpoint designPresenting lk house with six boxes and icons and key flat powerpoint design. This Power Point template diagram has been crafted with graphic of house and six text boxes. This PPT diagram contains the concept of home safety measures and real estate marketing .Use this PPT diagram for business and marketing related presentations.
-
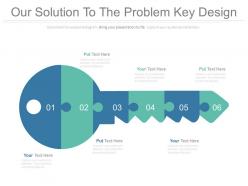 Our solution to the problem key design ppt slides
Our solution to the problem key design ppt slidesPresenting our solution to the problem key design ppt slides. This is a our solution to the problem key design ppt slides. This is a six stage process. The stages in this process are business, marketing, puzzle, strategy, process.
-
 Certification authority service powerpoint show
Certification authority service powerpoint showPresenting certification authority service powerpoint show. This is a certification authority service powerpoint show. This is a four stage process. The stages in this process are certified, professional.
-
 Laptop with lock for internet security ppt slides
Laptop with lock for internet security ppt slidesPresenting laptop with lock for internet security ppt slides. This is a laptop with lock for internet security ppt slides. This is a two stage process. The stages in this process are security.
-
 Lock with security shield design for safety ppt slides
Lock with security shield design for safety ppt slidesPresenting lock with security shield design for safety ppt slides. This is a lock with security shield design for safety ppt slides. This is a one stage process. The stages in this process are security.
-
 Security lock icon
Security lock iconPresenting this set of slides with name Security Lock Icon. This is a three stage process. The stages in this process are Security Icon, Camera Security, Money Security. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
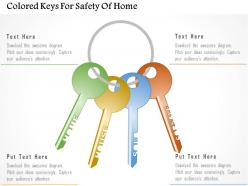 0115 colored keys for safety of home powerpoint template
0115 colored keys for safety of home powerpoint templateBeautifully designed PPT graphic helps in saving time and effort. Include or exclude slide content as per your individual need. Colors, layout and text can be easily changed as the PPT slide is completely editable. Personalize the presentation with individual company name and logo. This PPT Slide is available in both Standard and Widescreen slide size. Easy and quick downloading process.
-
 Laptop with fingerprint and lock for secured login ppt slides
Laptop with fingerprint and lock for secured login ppt slidesPresenting laptop with fingerprint and lock for secured login ppt slides. This is a laptop with fingerprint and lock for secured login ppt slides. This is a one stage process. The stages in this process are security,.
-
 Three colored locks for security techniques ppt slides
Three colored locks for security techniques ppt slidesPresenting three colored locks for security techniques ppt slides. This is a three colored locks for security techniques ppt slides. This is a three stage process. The stages in this process are security.
-
 Key issues lock format
Key issues lock formatPresenting this set of slides with name - Key Issues Lock Format. This is a three stage process. The stages in this process are Key Issues, Key Problems, Key Challenges.
-
 Six folders for data security analysis ppt slides
Six folders for data security analysis ppt slidesPresenting six folders for data security analysis ppt slides. This is a six folders for data security analysis ppt slides. This is a six stage process. The stages in this process are big data analytics, security.
-
 Ransomware Tabletop Exercise Icon For Ensuring Cyber Security
Ransomware Tabletop Exercise Icon For Ensuring Cyber SecurityIntroducing our premium set of slides with Ransomware Tabletop Exercise Icon For Ensuring Cyber Security. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Ransomware Tabletop Exercise, Icon, Ensuring Cyber Security. So download instantly and tailor it with your information.
-
 Budgeting planning power point guide
Budgeting planning power point guidePresenting budgeting planning power point guide. This is a budgeting planning power point guide. This is a nine stage process. The stages in this process are direct procurement, human resources, marketing and sales, delivery and after sale, indirect procurement, budgeting planning, design and development, strategic and planning, compliance and risk management.
-
 Secured internet connection for safety ppt slides
Secured internet connection for safety ppt slidesPresenting secured internet connection for safety ppt slides. This is a secured internet connection for safety ppt slides. This is a two stage process. The stages in this process are security.
-
 Target informational posts ppt background designs
Target informational posts ppt background designsPresenting target informational posts ppt background designs. This is a target informational posts ppt background designs. This is a four stage process. The stages in this process are problems solutions, solutions.
-
 Access rights key with five security access
Access rights key with five security accessPresenting this set of slides with name - Access Rights Key With Five Security Access. This is a one stage process. The stages in this process are Access Rights, Permission, Logins.
-
 Workforce utilization availability analysis ppt example
Workforce utilization availability analysis ppt examplePresenting workforce utilization availability analysis ppt example. This is a workforce utilization availability analysis ppt example. This is a five stage process. The stages in this process are affirmative action plan, applicant tracking, workforce utilization, availability analysis, union negotiation costing.
-
 Compliance and security icon ppt example file
Compliance and security icon ppt example filePresenting compliance and security icon ppt example file. An easy access to make desired changes has been provided; you can edit the slide as per your business needs. This PPT design offers great compatible with Google Slides and Microsoft PowerPoint software. High quality images and icons are used in designing this PPT design; they improve the performance of the presentation. Instant and easy downloading available; slides can be saved as JPEG or PDF formats.
-
 Key business benefits including teamwork
Key business benefits including teamworkPresenting this set of slides with name Key Business Benefits Including Teamwork. This is a five stage process. The stages in this process are Key Business Benefits, Success, Analysis. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Platform technology icon circuit board computer information
Platform technology icon circuit board computer informationPresenting this set of slides with name - Platform Technology Icon Circuit Board Computer Information. This is a one stage process. The stages in this process are Platform Technology Icon, Technology Application Icon.
-
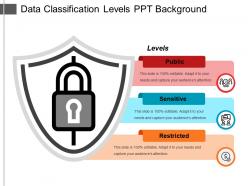 Data classification levels ppt background
Data classification levels ppt backgroundPresenting Data Classification Level Ppt Background as a presentation template. This template is designed by professionals of SlideTeam for proper data classification. The design is completely editable in PowerPoint as well as compatible with Google Slides. You can even change size of the table as per the requirement. A user can do changes in aspect ratio, font type and font size, because this template is 100% editable template along with that it is easily customizable i.e. text, colors, and boxes. You can save the slide into JPG or PDF formats.
-
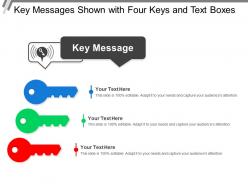 Key messages shown with four keys and text boxes
Key messages shown with four keys and text boxesPresenting this set of slides with name - Key Messages Shown With Four Keys And Text Boxes. This is a three stage process. The stages in this process are Key Messages, Key Notes, Comments.
-
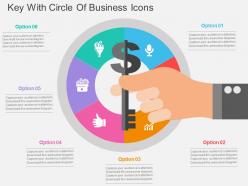 Key with circle of business icons flat powerpoint design
Key with circle of business icons flat powerpoint designModifiable PPT Slide with key with circle of business icons. Convertible into numerous format options like JPEG, JPG or PDF. Provides a professional outlook to your PowerPoint presentation. Icons are also be added. Customization of each PowerPoint graphic and text according to your desire and want. Multiple display option such as standard and widescreen view. Freedom to customize it with company name and logo.
-
 Icon showing hacker launching cyber attacks through malware
Icon showing hacker launching cyber attacks through malwareIntroducing our premium set of slides with Web Portal For Providing Services To Users. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Web Portal For Providing Services To Users. So download instantly and tailor it with your information.
-
 Multi level password selection for secured login ppt slides
Multi level password selection for secured login ppt slidesPresenting multi level password selection for secured login ppt slides. This is a multi level password selection for secured login ppt slides. This is a one stage process. The stages in this process are security.
-
 Vpn security icon
Vpn security iconPresenting this set of slides with name - Vpn Security Icon. This is a four stage process. The stages in this process are Vpn, Virtual Private Network.
-
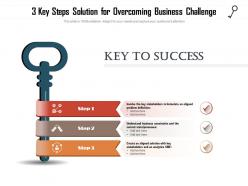 3 key steps solution for overcoming business challenge
3 key steps solution for overcoming business challengePresenting this set of slides with name 3 Key Steps Solution For Overcoming Business Challenge. This is a three stage process. The stages in this process are Business, Processes, Analytics. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Security guard icon
Security guard iconPresenting this set of slides with name Security Guard Icon. This is a three stage process. The stages in this process are Security Icon, Camera Security, Money Security. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Business man with target achievement success key flat powerpoint design
Business man with target achievement success key flat powerpoint designWe are proud to present our business man with target achievement success key flat powerpoint design. Concept of target achievement and success has been displayed in this power point template diagram. This PPT diagram contains the graphic of business man and key. Use this PPt diagram for business and sales related presentations.
-
 Assembly chain supply planning and control diagram presentation slides
Assembly chain supply planning and control diagram presentation slidesPresenting assembly chain supply planning and control diagram presentation slides. This is a assembly chain supply planning and control diagram presentation slides. This is a six stage process. The stages in this process are material requirement planning, assembly, dispatch, master production schedule, aggregate production planning, strategic planning, manufacturing planning.
-
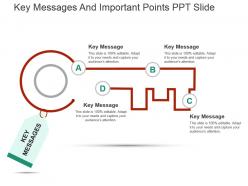 Key messages and important points ppt slide
Key messages and important points ppt slidePresenting key messages and important points ppt slide. This is a key messages and important points ppt slide. This is a one stage process. The stages in this process are key messages.
-
 Access rights lock privacy image
Access rights lock privacy imageFully creative and editable Access Rights Lock Privacy Image design, you can modify and personalize the presentation by including company name, logo and content in PPT. Useful for privacy centric presentations. The slide is easily modifiable by any user without having any professional experience. Easy and fast downloading process, slides can be downloaded as JPEG or PDF format. The PPT is compatible with Microsoft PowerPoint and Google Slides software.
-
 Slide having problem solution and result
Slide having problem solution and resultPresenting this set of slides with name Slide Having Problem Solution And Result. This is a three stage process. The stages in this process are Problem Slide, Common Business Problem, Analysis. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Network security technology for data privacy
Network security technology for data privacyPresenting this set of slides with name Network Security Technology For Data Privacy. This is a two stage process. The stages in this process are Network Security Technology For Data Privacy. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
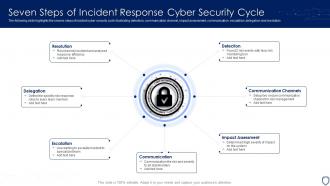 Seven Steps Of Incident Response Cyber Security Cycle
Seven Steps Of Incident Response Cyber Security CycleThe following slide highlights the sevens steps of incident cyber security cycle illustrating detection, communication channel, impact assessment, communication, escalation, delegation and resolution. Introducing our premium set of slides with name Seven Steps Of Incident Response Cyber Security Cycle. Ellicudate the seven stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Resolution, Detection, Communication Channels, Impact Assessment. So download instantly and tailor it with your information.
-
 Usb security shield and tools for data safety ppt slides
Usb security shield and tools for data safety ppt slidesPresenting usb security shield and tools for data safety ppt slides. This is a usb security shield and tools for data safety ppt slides. This is a two stage process. The stages in this process are security.
-
 Security systems deployed to countermeasure cyber attacks launched by hackers
Security systems deployed to countermeasure cyber attacks launched by hackersIntroducing our premium set of slides with Web Portal Requires Username And Password For Login. Ellicudate the one stage and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Web Portal Requires Username And Password For Login. So download instantly and tailor it with your information.
-
 Icon depicting computer security from cyber threat
Icon depicting computer security from cyber threatPresenting this set of slides with name Icon Depicting Computer Security From Cyber Threat. This is a three stage process. The stages in this process are Icon Depicting Computer Security From Cyber Threat. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Laptop with chain and lock for computer networking ppt slides
Laptop with chain and lock for computer networking ppt slidesPresenting laptop with chain and lock for computer networking ppt slides. This is a laptop with chain and lock for computer networking ppt slides. This is a two stage process. The stages in this process are security.
-
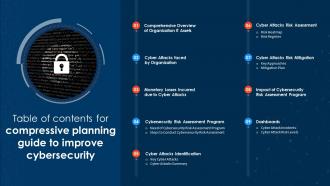 Table Of Contents For Compressive Planning Guide To Improve Cybersecurity
Table Of Contents For Compressive Planning Guide To Improve CybersecurityIntroducing Table Of Contents For Compressive Planning Guide To Improve Cybersecurity to increase your presentation threshold. Encompassed with nine stages, this template is a great option to educate and entice your audience. Dispence information on Cyber Attack Incidents, Cyber Attack Risk Levels, Cybersecurity Risk Assessment Program, Monetary Losses Incurred Due, using this template. Grab it now to reap its full benefits.
-
 Campaign management example of ppt presentation
Campaign management example of ppt presentationPresenting campaign management example of ppt presentation. This is a campaign management example of ppt presentation. This is a six stage process. The stages in this process are business analytics, loans origination, campaign management, customer onboarding, content management, statements and reporting.
-
 Working with people powerpoint slides presentation tips
Working with people powerpoint slides presentation tipsPresenting working with people powerpoint slides presentation tips. This is a working with people powerpoint slides presentation tips. This is a three stage process. The stages in this process are developing self and other, working self and other, achieving results.
-
 Four points curly braces icon with source code in middle
Four points curly braces icon with source code in middlePresenting four points curly braces icon with source code in middle. This is a four points curly braces icon with source code in middle. This is a four stage process. The stages in this process are code, programming, script, brackets.




