Diagrams on Computer Networking security hacking DDOS attacks
- Sub Categories
-
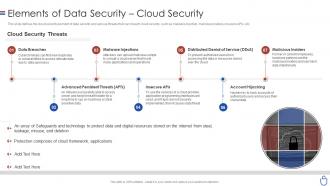 Data security it elements of data security cloud security
Data security it elements of data security cloud securityThis slide defines the cloud security element of data security and various threats that can breach cloud security, such as malware injection, malicious insiders, insecure APIs, etc. Increase audience engagement and knowledge by dispensing information using Data Security IT Elements Of Data Security Cloud Security. This template helps you present information on seven stages. You can also present information on Data Breaches, Malware Injections, Distributed Denial Service Ddos, Malicious Insiders, Account Hijacking, Advanced Persistent Threats using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Data protection icon
Data protection iconPresenting this set of slides with name Data Protection Icon. This is a one stage process. The stages in this process are Data Protection, Protection Techniques, Strategic Guidance. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
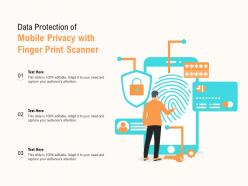 Data protection of mobile privacy with finger print scanner
Data protection of mobile privacy with finger print scannerIntroducing our premium set of slides with Data Protection Of Mobile Privacy With Finger Print Scanner. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Data Protection Of Mobile Privacy With Finger Print Scanner. So download instantly and tailor it with your information.
-
 1114 bar graph with text boxes for data display powerpoint template
1114 bar graph with text boxes for data display powerpoint templateWe are proud to present our 1114 bar graph with text boxes for data display powerpoint template. Graphic of bar graph and text boxes are used to decorate this power point template slide. This PPT slide contains the concept of data analysis and result display. Use this PPT slide for your business and data related presentations.
-
 Key messages in advertising campaign powerpoint slide designs
Key messages in advertising campaign powerpoint slide designsPresenting key messages in advertising campaign powerpoint slide designs. This is a key messages in advertising campaign powerpoint slide designs. This is a six stage process. The stages in this process are key messages.
-
 Circular shield icon
Circular shield iconPresenting Circular Shield Icon template. Make as many changes as you want on the slide Transform this template into various document or image formats like PDF or JPEG. The slide is fully customizable in PowerPoint and other office suites. Alter the font style, font color, and other components with ease. The slide is also compatible with Google Slides. High-quality graphics ensure that quality is always maintained.
-
 Two locked unlocked grey color padlock
Two locked unlocked grey color padlockPresenting two locked unlocked grey color padlock. This is a two locked unlocked grey color padlock. This is a two stage process. The stages in this process are padlock, lock, locker.
-
 Access rights security lock image
Access rights security lock imagePresenting this set of slides with name - Access Rights Security Lock Image. This is a one stage. The stage in this process are Access Rights, Access Privilege, Access Management.
-
 Cctv camera security icon
Cctv camera security iconPresenting this set of slides with name CCTV Camera Security Icon. This is a three stage process. The stages in this process are Security Icon, Camera Security, Money Security. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
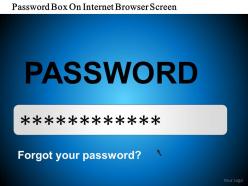 Password box on internet browser screen ppt slides
Password box on internet browser screen ppt slidesPresenting password box on internet browser screen ppt slides. This is a password box on internet browser screen ppt slides. This is a one stage process. The stages in this process are security.
-
 Custom requirements management ppt sample file
Custom requirements management ppt sample filePresenting custom requirements management ppt sample file. This is a requirements management ppt sample file. This is a two stage process. The stages in this process are implementation governance, requirements management.
-
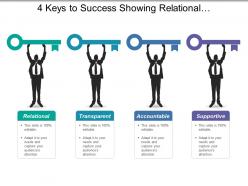 4 keys to success showing relational transparent supportive and accountable
4 keys to success showing relational transparent supportive and accountablePresenting this set of slides with name - 4 Keys To Success Showing Relational Transparent Supportive And Accountable. This is a four stage process. The stages in this process are 4 Keys To Success, Motivation, 4 Keys To Growth.
-
 Action items icon for information security management
Action items icon for information security managementPresenting this set of slides with name Action Items Icon For Information Security Management. This is a three stage process. The stages in this process are Action Items Icon For Information Security Management. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Digital data security powerpoint slide
Digital data security powerpoint slidePresenting digital data security PowerPoint slide. Slideshow is fully editable. You can change all the design components and customize is according to your business requirements. Include business related data into text place holders provided in PPT design. Complete error free downloading is available. Download the design into JPEG and PDF formats. PPT is fully supported on Google Slides, MS PowerPoint and other compatible software.
-
 Key features of business analysis toolkit
Key features of business analysis toolkitPresenting this set of slides with name Key Features Of Business Analysis Toolkit. This is a five stage process. The stages in this process are Modern Requirements, Jama Software, ABBYY Finereader, Blueprint, Axure. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Impact analysis implementing cybersecurity framework metric ppt gallery inspiration
Impact analysis implementing cybersecurity framework metric ppt gallery inspirationThis slide portrays information regarding the impact of successful implementation of cybersecurity framework or core functional areas. This slide portrays how IT department is progressing on different aspects. Presenting this set of slides with name Impact Analysis Implementing Cybersecurity Framework Metric Ppt Gallery Inspiration. This is a one stage process. The stages in this process are Impact Analysis Implementing Cybersecurity Framework. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Shield with multiple icons safety indication flat powerpoint design
Shield with multiple icons safety indication flat powerpoint designWe are proud to present our shield with multiple icons safety indication flat powerpoint design. Graphic of shield with multiple icons has been used to design this power point template diagram. This PPT diagram contains the concept of safety indication. Use this PPT diagram for business and marketing related presentations.
-
 House key icon
House key iconPresenting house key icon. This is a house key icon. This is a four stage process. The stages in this process are key icon, lock icon.
-
 Source code icons
Source code iconsPresenting the Source Code Icons template. This PPT layout is 100% customizable. Alter the font size, font type, font color, and shape used according to your needs This easy to download PPT theme can be easily opened and saved in various formats like JPG, PDF, and PNG. This PowerPoint template is Google Slides compatible and is easily accessible.
-
 Pass document approval using stamp holder
Pass document approval using stamp holderPresenting pass document approval using stamp holder. This is a pass document approval using stamp holder. This is a one stage process. The stages in this process are pass, progress, proceed.
-
 Number one shield icon
Number one shield iconPresenting number one shield icon. This is a number one shield icon. This is a one stage process. The stages in this process are shield icon, protection icon, safety icon.
-
 Access control showing business man and lock
Access control showing business man and lockPresenting this set of slides with name - Access Control Showing Business Man And Lock. This is a one stage process. The stages in this process are Access Control, Information Security, Identity Management.
-
 Lock with three text boxes icons flat powerpoint design
Lock with three text boxes icons flat powerpoint designWe are proud to present our lock with three text boxes icons flat powerpoint design. This power point template diagram has been crafted with graphic of lock and three text boxes. This PPT diagram contains the concept of safety features and data representation. Use this PPT diagram for business and marketing related presentations.
-
 Icon reprinting cybersecurity measures for strong protecting
Icon reprinting cybersecurity measures for strong protectingIntroducing our premium set of slides with Icon Reprinting Cybersecurity Measures For Strong Protecting. Elucidate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Icon Reprinting Cybersecurity Measures For Strong Protecting. So download instantly and tailor it with your information.
-
 Lock icon for cybersecurity network protection
Lock icon for cybersecurity network protectionPresenting our set of slides with Lock Icon For Cybersecurity Network Protection. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Lock Icon For Cybersecurity Network Protection.
-
 IT Cyber Security Incident Response Icon
IT Cyber Security Incident Response IconIntroducing our premium set of slides with name IT Cyber Security Incident Response Icon. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like IT Cyber, Security Incident, Response Icon. So download instantly and tailor it with your information.
-
 Icon For Zero Trust Network Architecture
Icon For Zero Trust Network ArchitectureIntroducing our premium set of slides with Icon For Zero Trust Network Architecture. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Icon Zero Trust, Network Architecture. So download instantly and tailor it with your information.
-
 Fraud identity protection finger print chain icon
Fraud identity protection finger print chain iconPresenting fraud identity protection finger print chain icon. This is a fraud identity protection finger print chain icon. This is a one stage process. The stages in this process are fraud, cheater, stabber.
-
 Blockchain technology icon with cybersecurity symbol
Blockchain technology icon with cybersecurity symbolPresenting our set of slides with Blockchain Technology Icon With Cybersecurity Symbol. This exhibits information on three stages of the process. This is an easy-to-edit and innovatively designed PowerPoint template. So download immediately and highlight information on Blockchain Technology Icon With Cybersecurity Symbol.
-
 1214 four staged business key stair case diagram powerpoint template
1214 four staged business key stair case diagram powerpoint templateWe are proud to present our 1214 four staged business key stair case diagram powerpoint template. Four staged business key has been used to design this power point template. This PPT contains the concept of success. Use this PPT for your business and marketing related presentations.
-
 Shield icon with star sign
Shield icon with star signPresenting shield icon with star sign. This is a shield icon with star sign. This is a one stage process. The stages in this process are shield icon, protection icon, safety icon.
-
 Security company showing building with security lock
Security company showing building with security lockPresenting this set of slides with name - Security Company Showing Building With Security Lock. This is a two stage process. The stages in this process are Security Company, Safety Company, Security Firm.
-
 IT Risk Management Strategies Prioritized Cyber Security Threats With Risk Mitigation Plan
IT Risk Management Strategies Prioritized Cyber Security Threats With Risk Mitigation PlanThis slide highlights the cyber security threats with key risks and their mitigation plan and owner with risk reduction timeline. Increase audience engagement and knowledge by dispensing information using IT Risk Management Strategies Prioritized Cyber Security Threats With Risk Mitigation Plan. This template helps you present information on one stages. You can also present information on Threat, Risk, Risk Priority, Risk Reduction Timeline using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Ds key with success text and four tags flat powerpoint design
Ds key with success text and four tags flat powerpoint designPresenting ds key with success text and four tags flat powerpoint design. This Power Point template slide has been designed with graphic of key and success text with four tags. This PPT diagram contains the concept of key of success analysis Use this PPT slide for business and finance related presentations.
-
 Car icon secured under insurance protect plan
Car icon secured under insurance protect planPresenting this set of slides with name Car Icon Secured Under Insurance Protect Plan. This is a three stage process. The stages in this process are Car Icon Secured Under Insurance Protect Plan. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Computer security icon with shield
Computer security icon with shieldPresenting this set of slides with name Computer Security Icon With Shield. This is a three stage process. The stages in this process are Computer Security Icon With Shield. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 File encryption with lock icon
File encryption with lock iconPresenting this set of slides with name File Encryption With Lock Icon. This is a one stage process. The stage in this process is File Encryption With Lock Icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 User authentication human firewall security icon
User authentication human firewall security iconPresenting this set of slides with name User Authentication Human Firewall Security Icon. This is a three stage process. The stages in this process are User Authentication Human Firewall Security Icon. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
 Mobile security access system with lock icon
Mobile security access system with lock iconIntroducing our premium set of slides with Mobile Security Access System With Lock Icon. Ellicudate the three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Mobile Security Access System With Lock Icon. So download instantly and tailor it with your information.
-
 Lock For Safety Measures And Risk Management Flat Powerpoint Design
Lock For Safety Measures And Risk Management Flat Powerpoint DesignWe are proud to present our lock for safety measures and risk management flat powerpoint design. Graphic of lock has been used to craft this power point template. This PPT diagram contains the concept of safety and security. This PPT contains the details of risk management. Use this PPT diagram for business and marketing related presentation.
-
 Key for success showing the important factor to accomplish the desired business goal
Key for success showing the important factor to accomplish the desired business goalPresenting desired business goal accomplishment PPT slide. The key for success presentation template designed professionally to share the business strategies which enables you to achieve the desired target. The PowerPoint business target template is editable as well as compatible with Google Slide so you can share it easily over the internet. You can do changes in font size, font type, color and design of icon because the ions are customizable. As you need to explain the strategies in an easy way so you can take help of this presentation template. The unique design key icon helps you to grab the attention of your audience.
-
 Core icon with chip and data protection
Core icon with chip and data protectionPresenting this set of slides with name Core Icon With Chip And Data Protection. This is a three stage process. The stages in this process are Core Icon With Chip And Data Protection. This is a completely editable PowerPoint presentation and is available for immediate download. Download now and impress your audience.
-
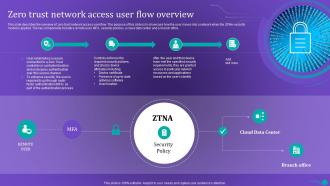 Zero Trust Network Access User Flow Overview Ppt Outline Design Inspiration
Zero Trust Network Access User Flow Overview Ppt Outline Design InspirationThis slide describes the overview of zero trust network access user flow. The purpose of this slide is to showcase how the user moves into a network when the ZTNA security model is applied. The key components include a remote user, MFA, security policies, a cloud data center and a branch office. Increase audience engagement and knowledge by dispensing information using Zero Trust Network Access User Flow Overview Ppt Outline Design Inspiration. This template helps you present information on four stages. You can also present information on Particular Network, Security, Device using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Key messages marketing plan powerpoint slide images
Key messages marketing plan powerpoint slide imagesPresenting key messages marketing plan powerpoint slide images. This is a key messages marketing plan powerpoint slide images. This is a four stage process. The stages in this process are key messages.
-
 Unlock the laptop with passcode icon
Unlock the laptop with passcode iconPresenting Unlock The Laptop With Passcode Icon template. This PPT template is available in both 4:3 and 16:9 aspect ratios. As this PowerPoint template is 100% editable, you can modify the color, font size, font type, and shapes as per your requirements. This PPT presentation is Google Slides compatible hence it is easily accessible. You can download and save this PowerPoint layout in different formats like PDF, PNG, and JPG
-
 Data Privacy It Purpose Limitation Principle Of Gdpr Law
Data Privacy It Purpose Limitation Principle Of Gdpr LawThis slide depicts the purpose limitation principle, which states that you should be clear from the start about the reasons and intentions for collecting and processing data. Introducing Data Privacy It Purpose Limitation Principle Of Gdpr Law to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Authorization, Limitation, Principle, using this template. Grab it now to reap its full benefits.
-
 Lg three staged business staircase diagram powerpoint template
Lg three staged business staircase diagram powerpoint templatePresenting lg three staged business staircase diagram powerpoint template. Three staged staircase diagram has been used to craft this Power Point template diagram. This PPT diagram contains the concept of business success representation. Use this PPT diagram for business and marketing related presentations.
-
 Code coding icons
Code coding iconsPresenting Code Coding Icons. This slide is 100% editable and is designed professionally for your convenience. The slide is readily available in both 4:3 and 16:9 aspect ratio. Alter the colors, fonts, font size, and font types of the template as per the requirements. It can be changed into formats like PDF, JPG, and PNG. The template is adaptable with Google Slides, which makes it accessible at once.
-
 Enterprise Security Operation System Icon
Enterprise Security Operation System IconPresenting our set of slides with Enterprise Security Operation System Icon. This exhibits information on four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Enterprise Security Operation, System Icon.
-
 Safety features for business flat powerpoint design
Safety features for business flat powerpoint designWe are proud to present our safety features for business flat powerpoint design. Define the safety features for any business process with this unique PPT diagram. This diagram contains the graphic of keys and lock.. Use this PPT diagram for business presentations and get good remarks.
-
 Ss key lock graphics and icons bar graph flat powerpoint design
Ss key lock graphics and icons bar graph flat powerpoint designPresenting ss key lock graphics and icons bar graph flat powerpoint design. Graphic of key and lock has been used to craft this power point template diagram. This PPT diagram contains the concept of security. Use this PPT diagram for business and sales related presentations
-
 Firewall installation to prevent cyber attacks
Firewall installation to prevent cyber attacksPresenting our set of slides with Firewall Installation To Prevent Cyber Attacks. This exhibits information on one stage of the process. This is an easy-to-edit and innovatively designed PowerPoint template. So download immediately and highlight information on Firewall Installation To Prevent Cyber Attacks.
-
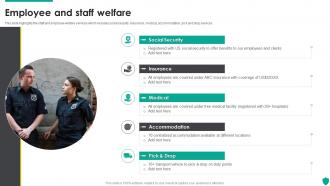 Employee And Staff Welfare Security Guard Service Company Profile
Employee And Staff Welfare Security Guard Service Company ProfileThis slide highlights the staff and employee welfare services which includes social security, insurance, medical, accommodation, pick and drop services. Introducing Employee And Staff Welfare Security Guard Service Company Profile to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Social Security, Insurance, Medical, Accommodation, using this template. Grab it now to reap its full benefits.
-
 Lock with chain for safety issues flat powerpoint design
Lock with chain for safety issues flat powerpoint designWe are proud to present our lock with chain for safety issues flat powerpoint design. Concept of safety issues has been displayed in this PPT diagram with suitable graphics. This PPT diagram contains the graphic of lock with chain. Use this PPT diagram for business and marketing related presentations and build an innovative presentation for your viewers.
-
 Login page of account with user id and password
Login page of account with user id and passwordPresenting this set of slides with name - Login Page Of Account With User Id And Password. This is a one stage process. The stages in this process are Security, Login, Authentication.
-
 Key for success describing the combination of important factors for
Key for success describing the combination of important factors forPresenting combined business success factor PPT slide. The business success element presentation template designed by the professional team of SlideTeam for the business objective achievement. The essential factor slide is editable in PowerPoint as well as compatible with Google Slides so that you do not have to face any problem while sharing it. Whether it is font size, font type, colors or shapes of the icon, you can modify all these in the slide as per your requirements. You can insert the text to address the specific business success key because SlideTeam has designed it by added dummy text in the slide.
-
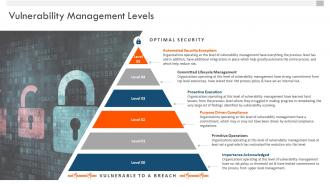 Vulnerability management whitepaper vulnerability management levels ppt styles show
Vulnerability management whitepaper vulnerability management levels ppt styles showIntroducing Vulnerability Management Whitepaper Vulnerability Management Levels Ppt Styles Show to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Automated Security Ecosystem, Committed Lifecycle Management, Proactive Execution, Purpose Driven Compliance, Primitive Operations, Importance Acknowledged, using this template. Grab it now to reap its full benefits.
-
 Payment security and fraud management market entry report transformation
Payment security and fraud management market entry report transformationFrom prevention to detection and resolution, data fraud management solutions allow you to leverage proven technologies to create customized strategies that help limit losses while maintaining a high level of customer satisfaction. Increase audience engagement and knowledge by dispensing information using Payment Security And Fraud Management Market Entry Report Transformation. This template helps you present information on three stages. You can also present information on Market Basket Analysis, Customer ID Analysis, Device Fingerprinting, Geolocation Analysis using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Code brackets icons
Code brackets iconsPresenting Code Brackets Icons. Alter the colors, fonts, font size, and font types of the template as per the requirements. This slide is 100% editable and is designed professionally for your convenience. The slide is readily available in both 4:3 and 16:9 aspect ratio. It can be changed into formats like PDF, JPG, and PNG. The template is adaptable with Google Slides, which makes it accessible at once.
-
 Four unlocked locked padlock showcasing phases
Four unlocked locked padlock showcasing phasesPresenting four unlocked locked padlock showcasing phases. This is a four unlocked locked padlock showcasing phases. This is a four stage process. The stages in this process are padlock, lock, locker.




