In a world, where technology is everywhere with computers and networks a major part of our professional and personal lives, risks associated with these gadgets are humongous. Commonly referred to as cyber risks, organizations and businesses have to conduct a thorough cyber risk assessment of their organizations.
This involves finding and analyzing possible risks and weaknesses in a company's digital systems. Experts act as cyber spies by completing this evaluation, finding vulnerabilities, evaluating risks, and making suggestions to strengthen defenses. Think about Sherlock Holmes operating in a virtual environment, inspecting all aspects of your computer systems and networks, and neutralizing all cyber risks.
Businesses have to take this avatar for some time to protect their important data and sensitive information by carrying out a cyber risk assessment. It's similar to donning a digital bulletproof vest and making sure you have a virtual castle to defend against online criminals. Let cyber investigators and risk analysts do their jobs while you relax in the knowledge that your digital world is secure!
As technology advances, so do the threats that target our digital assets and information.
SlideTeam’s expert-curated templates on cyber security help you track and analyze any potential risk that could impede the organization’s productivity.This collection is designed to assist you in evaluating and mitigating cyber risks within your organization. With clear and concise content layout, customizable graphics and intuitive designs you can effectively present your findings and recommendations to ensure the cybersecurity of your organization.
Each of the cyber security ppt templates are 100% editable and customizable. The content-ready nature provides you with the starting point and a much-desired structure. The editability feature means you can tailor the presentation to audience preference and tastes.
Let’s study the templates now!
CYBER RISK ASSESSMENT TEMPLATES TO SAFEGUARD YOUR DIGITAL FRONTIER
Furthermore, access this link in order to get the IT Security Risk Management Plan Templates and make your organization’s digital wall even stronger via a detailed plan.
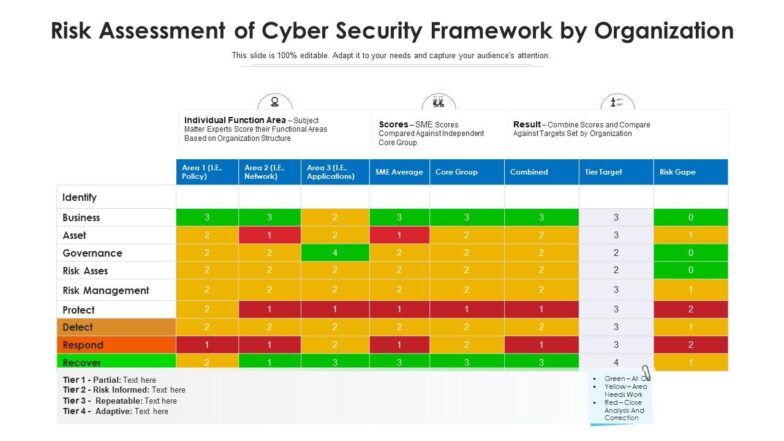
Template 1: Risk Assessment of Cyber Security Framework by Organization
This content-ready slide depicts the level of risk based on four tiers or levels. The first tier shows partial, the second is for informed risk, the third one states repeatable risk and lastly, the tier-4 indicates adaptive risk. This template is color-coded for comprehensive understanding. The color green suggests that this particular area is “all ok”, yellow color is for areas that need work in terms of threat and red areas require close analysis and correction. Adapt this to your needs and capture your audience’s attention. Download now!
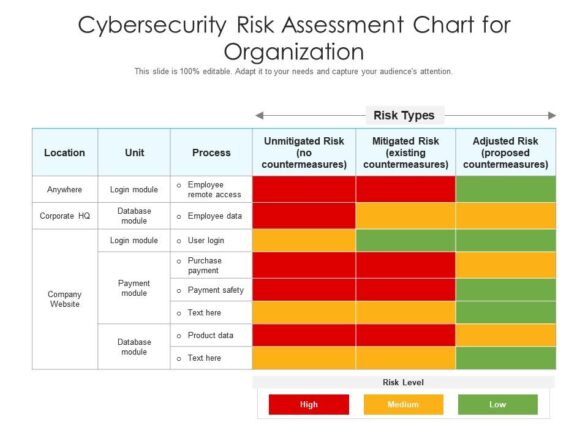
Template 2: Cybersecurity Risk Assessment Chart for Organization
This template in a tabular form shows the areas in an organization which are in a high, medium or low level of cyber risk. It exhibits the location where the risk mostly comes true, its units and the processes earmarked for employee data, user login, payment safety, etc. and their risk type for the organization. The risk type is evaluated under the categories, unmitigated, mitigated and adjusted risk. The risk types are color-coded as well to ensure there is a deeper understanding and effort made to counter the risk. Get this deck now!
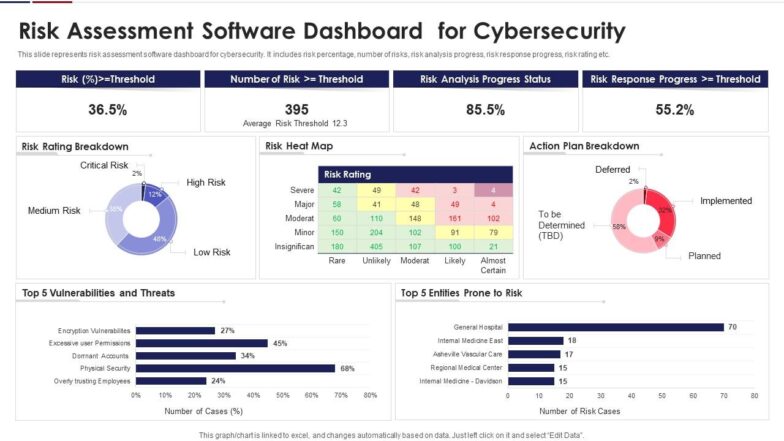
Template 3: Risk Assessment Software Dashboard for Cybersecurity
This template represents a risk assessment dashboard which includes threat percentage, number of risks, risk analysis progress, risk rating and more. Use this template to track the top 5 vulnerabilities and threats along with top 5 entities prone to risk. You can also track whether the impact of the risk will be low, medium, high or critical. This information is presented in the form of a pie chart and color coded for easier understanding. Also, note the risk response progress percentage along with the risk analysis. . The risk rating table in the given slide will help in analyzing whether the probability of it materializing is evere or insignificant. This empirical-evidence dashboard then is the answer to all your queries, as you decide on the action that you will take to ensure cyber security across your organization. Download now!
Template 4: Information Security Cyber Risk Assessment Dashboard
The PPT Dashboard showcases the color-coded risk levels. It also depicts activities that organizations routinely do that put them at high-risk. The prominent one among them is allowing never-expiring-passwords. Here, the idea is that if the majority of the staff never change their password, the defenses against cyber security weaken. The level of risk is presented in the form of a meter which shifts between low to high based on the data. Here, the color red denotes high level of risk, yellow is for medium risk and lastly, green indicates low risk. Get this presentation template now!
Template 5: Cyber Security Risk Assessment Matrix
The tabular layout of this pre-designed PowerPoint Slide shows the risk assessment of cyber security emphasizing severity of each medium of cyber fraud or threats. The presentation template covers threats like phishing, ransomware, web app attacks, and vendor partner loss. This underlines the impact of risks based on its vulnerability with color-coded tags to promote understandability. Download the bundle now!
Using Cyber Risk Assessment PowerPoint (PPT) templates can greatly enhance the effectiveness and efficiency of communicating cyber risk assessment findings. These templates offer a systematic framework for communicating complicated information in a way that is both aesthetically pleasing and simple to comprehend. They let stakeholders understand the seriousness of the problem.
The USP is the clear visualization of identified vulnerabilities, threats, and potential repercussions. Our PPT Templates also simplify the reporting process, saving both time and money. Organizations may effectively communicate the significance of cybersecurity risk assessment, support informed decision-making, and encourage a proactive strategy for managing cyber threats by leveraging these templates. Adopting Cyber Risk Assessment PPT templates may help to improve overall cybersecurity policies and, in the end, protect important assets and data from potential attacks.
It would be great if you could pre-assess any potential risk, isn’t it? Follow this link in order to get Top 5 Risk Assessment Framework Templates.
FAQs on Cyber Risk Assessment
What is a Cyber Risk Assessment?
A cyber risk assessment is an organized process for risk identification, examining, and assessing possible dangers to a company's digital systems and data. It entails evaluating the likelihood for cyberattacks or security breaches, their potential effects, and assessing the effectiveness of the security measures already in place.
Organizations may use the evaluation to better understand how exposed they are to risk and to decide which risk mitigation techniques will be most effective. An organization's overall cybersecurity posture may be improved. The possibility of data breaches or other cyber events decreased by completing a cyber risk assessment.
What are the 5 steps to cyber security risk assessment?
The evaluation of cybersecurity risk involves five steps. These steps can help organizations get a thorough awareness of their cybersecurity threats and take necessary precautions to safeguard their systems and data.
- Identify Assets: List all digital assets that require security, such as hardware, software, networks, and data.
- Assess Vulnerabilities: Consider potential entry points for attackers while assessing the assets' vulnerabilities and shortcomings.
- Evaluate Threats: Analyze prospective dangers and the possibility that they may materialize, such as insider threats, cybercrime, or natural disasters.
- Measure Impact: Determine the potential impact of a successful attack, including financial loss, reputational damage, and operational disruption.
- Prioritize and Mitigate Risks: Prioritize risks based on their likelihood and effect. Create an incident response plan as part of a risk mitigation approach that also involves putting in place security measures.
What are the 4 phases of security risk assessment?
- Planning: The scope and objectives of the assessment are defined at this phase. The assets that will be evaluated, the assessment team, and the schedule is also established.
- Information Gathering: During this stage, pertinent data is obtained, such as system settings, network diagrams, security procedures, and incident histories. This information aids in comprehending the organization's security environment.
- Risk analysis: Vulnerabilities, dangers, and prospective effects are found by examining the data that has been gathered. To analyze the possibility and effects of security events, risk analysis approaches like qualitative or quantitative risk assessment are utilized.
- Reporting and Recommendations: A thorough report fully details the conclusions and suggestions. An overview of the risks that have been discovered is also provided. It also ranks them by importance, and suggests ways to mitigate them.
What are some essential cybersecurity risk assessment tools?
Organizations may use a number of crucial cybersecurity risk assessment tools to strengthen their security posture. Network, system, and application vulnerabilities may be found using vulnerability scanners like Nessus and Qualys. To find possible holes, instruments for penetration testing like Metasploit replicate actual assaults.
Monitoring and correlating security events throughout the infrastructure is made easier with the help of security information and event management (SIEM) tools like IBM QRadar or Splunk. Platforms for threat intelligence like Recorded Future offer insightful information on new threats and weaknesses. Last but not least, risk assessment frameworks like the NIST Cybersecurity Framework and ISO 27001 support organizations in determining their total cybersecurity risk and developing a systematic risk management strategy.





 Customer Reviews
Customer Reviews