Powerpoint Templates and Google slides for Phishing Attacks
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Phishing Attacks And Strategies To Mitigate Them Powerpoint Presentation Slides
Phishing Attacks And Strategies To Mitigate Them Powerpoint Presentation SlidesDeliver an informational PPT on various topics by using this Phishing Attacks And Strategies To Mitigate Them Powerpoint Presentation Slides. This deck focuses and implements best industry practices, thus providing a birds-eye view of the topic. Encompassed with one hundred one slides, designed using high-quality visuals and graphics, this deck is a complete package to use and download. All the slides offered in this deck are subjective to innumerable alterations, thus making you a pro at delivering and educating. You can modify the color of the graphics, background, or anything else as per your needs and requirements. It suits every business vertical because of its adaptable layout.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Powerpoint Presentation Slides
Phishing Attacks And Strategies To Mitigate Them V2 Powerpoint Presentation SlidesThis complete deck covers various topics and highlights important concepts. It has PPT slides which cater to your business needs. This complete deck presentation emphasizes Phishing Attacks And Strategies To Mitigate Them V2 Powerpoint Presentation Slides and has templates with professional background images and relevant content. This deck consists of total of ninety five slides. Our designers have created customizable templates, keeping your convenience in mind. You can edit the color, text and font size with ease. Not just this, you can also add or delete the content if needed. Get access to this fully editable complete presentation by clicking the download button below.
-
 Phishing Attacks Awareness Training IT Powerpoint Ppt Template Bundles
Phishing Attacks Awareness Training IT Powerpoint Ppt Template BundlesDeliver a credible and compelling presentation by deploying this Phishing Attacks Awareness Training IT Powerpoint Ppt Template Bundles. Intensify your message with the right graphics, images, icons, etc. presented in this complete deck. This PPT template is a great starting point to convey your messages and build a good collaboration. The twenty nine slides added to this PowerPoint slideshow helps you present a thorough explanation of the topic. You can use it to study and present various kinds of information in the form of stats, figures, data charts, and many more. This Phishing Attacks Awareness Training It Powerpoint Ppt Template Bundles PPT slideshow is available for use in standard and widescreen aspects ratios. So, you can use it as per your convenience. Apart from this, it can be downloaded in PNG, JPG, and PDF formats, all completely editable and modifiable. The most profound feature of this PPT design is that it is fully compatible with Google Slides making it suitable for every industry and business domain.
-
 Phishing Attack Types In Cyber Attack Training Ppt
Phishing Attack Types In Cyber Attack Training PptPresenting Phishing Attack Types in Cyber Attack. These slides are 100 percent made in PowerPoint and are compatible with all screen types and monitors. They also support Google Slides. Premium Customer Support available. Suitable for use by managers, employees, and organizations. These slides are easily customizable. You can edit the color, text, icon, and font size to suit your requirements.
-
 Overview Of Phishing Attacks Training Ppt
Overview Of Phishing Attacks Training PptPresenting Overview of Phishing Attacks. This PPT presentation is meticulously researched and each slide consists of relevant content. Designed by SlideTeams PowerPoint experts, this PPT is fully customizable alter the colors, text, icons, and font size to meet your requirements. Compatible with Google Slides and backed by excellent customer support. Download to present with poise and assurance.
-
 Working Of Spam And Phishing Attacks Training Ppt
Working Of Spam And Phishing Attacks Training PptPresenting Working of Spam and Phishing Attacks. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
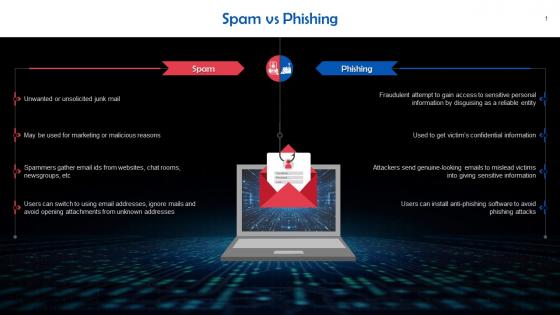 Difference Between Spam And Phishing Attacks Training Ppt
Difference Between Spam And Phishing Attacks Training PptPresenting Difference Between Spam and Phishing Attacks. This PPT presentation is thoroughly researched and each slide consists of appropriate content. Designed by PowerPoint specialists, this PPT is fully customizable alter the colors, text, icons, and font size to meet your needs. Compatible with Google Slides and backed by superior customer support. Download today to deliver your presentation confidently.
-
 Different Types Of Phishing Attacks Training Ppt
Different Types Of Phishing Attacks Training PptPresenting Different Types of Phishing Attacks. This PPT presentation is meticulously researched and each slide consists of relevant content. Designed by SlideTeams PowerPoint experts, this PPT is fully customizable alter the colors, text, icons, and font size to meet your requirements. Compatible with Google Slides and backed by excellent customer support. Download to present with poise and assurance.
-
 Spear Phishing As A Type Of Phishing Attack Training Ppt
Spear Phishing As A Type Of Phishing Attack Training PptPresenting Spear Phishing as a Type of Phishing Attack. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 Whaling As A Type Of Phishing Attack Training Ppt
Whaling As A Type Of Phishing Attack Training PptPresenting Whaling as a Type of Phishing Attack. This PPT presentation is thoroughly researched and each slide consists of appropriate content. Designed by PowerPoint specialists, this PPT is fully customizable alter the colors, text, icons, and font size to meet your needs. Compatible with Google Slides and backed by superior customer support. Download today to deliver your presentation confidently.
-
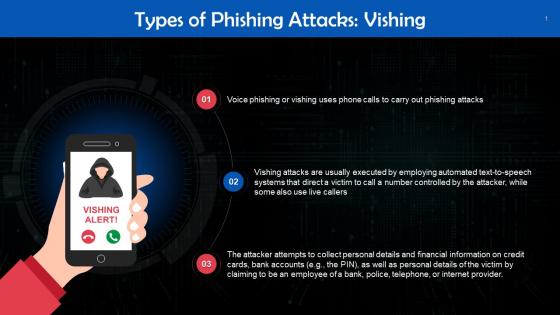 Vishing As A Type Of Phishing Attack Training Ppt
Vishing As A Type Of Phishing Attack Training PptPresenting Vishing as a Type of Phishing Attack. This PPT presentation is meticulously researched and each slide consists of relevant content. Designed by SlideTeams PowerPoint experts, this PPT is fully customizable alter the colors, text, icons, and font size to meet your requirements. Compatible with Google Slides and backed by excellent customer support. Download to present with poise and assurance.
-
 Smishing As A Type Of Phishing Attack Training Ppt
Smishing As A Type Of Phishing Attack Training PptPresenting Smishing as a Type of Phishing Attack. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 Email Phishing As A Type Of Phishing Attack Training Ppt
Email Phishing As A Type Of Phishing Attack Training PptPresenting Email Phishing as a Type of Phishing Attack. This PPT presentation is thoroughly researched and each slide consists of appropriate content. Designed by PowerPoint specialists, this PPT is fully customizable alter the colors, text, icons, and font size to meet your needs. Compatible with Google Slides and backed by superior customer support. Download today to deliver your presentation confidently.
-
 Search Engine Phishing As A Type Of Phishing Attack Training Ppt
Search Engine Phishing As A Type Of Phishing Attack Training PptPresenting Search Engine Phishing as a Type of Phishing Attack. This PPT presentation is meticulously researched and each slide consists of relevant content. Designed by SlideTeams PowerPoint experts, this PPT is fully customizable alter the colors, text, icons, and font size to meet your requirements. Compatible with Google Slides and backed by excellent customer support. Download to present with poise and assurance.
-
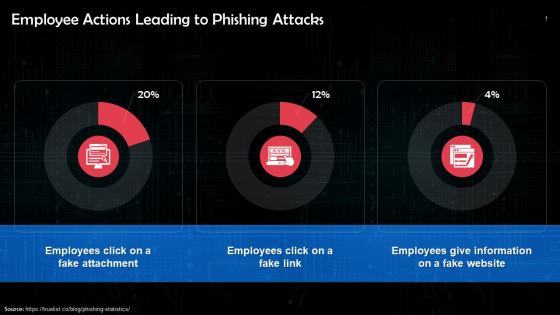 Employee Actions Leading To Phishing Attacks Training Ppt
Employee Actions Leading To Phishing Attacks Training PptPresenting Employee Actions Leading to Phishing Attacks. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
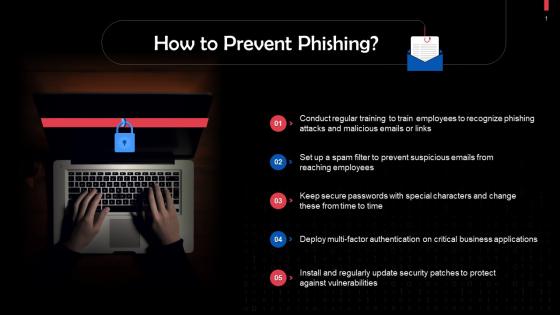 Tips To Prevent Phishing Attacks Training Ppt
Tips To Prevent Phishing Attacks Training PptPresenting Tips to Prevent Phishing Attacks. This PPT presentation is thoroughly researched and each slide consists of appropriate content. Designed by PowerPoint specialists, this PPT is fully customizable alter the colors, text, icons, and font size to meet your needs. Compatible with Google Slides and backed by superior customer support. Download today to deliver your presentation confidently.
-
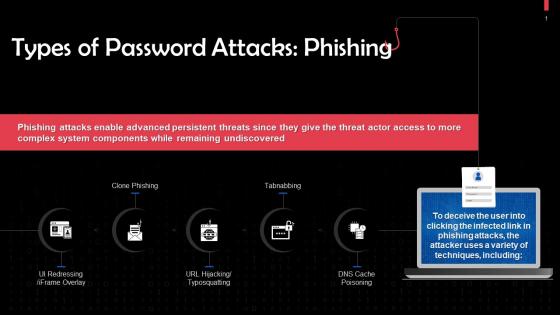 Types Of Phishing Password Attacks In Cyber Security Training Ppt
Types Of Phishing Password Attacks In Cyber Security Training PptPresenting Types of Phishing Password Attacks in Cyber Security. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
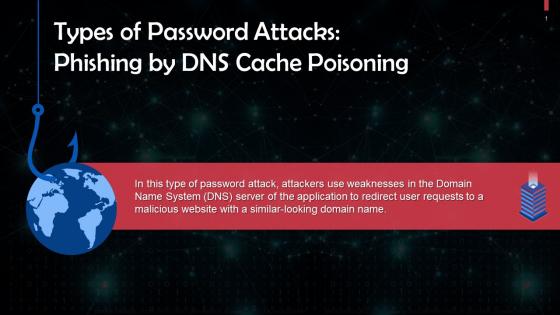 Phishing Password Attack By DNS Cache Poisoning Training Ppt
Phishing Password Attack By DNS Cache Poisoning Training PptPresenting Phishing Password Attack by DNS Cache Poisoning. This PPT presentation is thoroughly researched and each slide consists of appropriate content. Designed by PowerPoint specialists, this PPT is fully customizable alter the colors, text, icons, and font size to meet your needs. Compatible with Google Slides and backed by superior customer support. Download today to deliver your presentation confidently.
-
 Phishing Password Attack By Tabnabbing Training Ppt
Phishing Password Attack By Tabnabbing Training PptPresenting Phishing Password Attack by Tabnabbing. This PPT presentation is meticulously researched and each slide consists of relevant content. Designed by SlideTeams PowerPoint experts, this PPT is fully customizable alter the colors, text, icons, and font size to meet your requirements. Compatible with Google Slides and backed by excellent customer support. Download to present with poise and assurance.
-
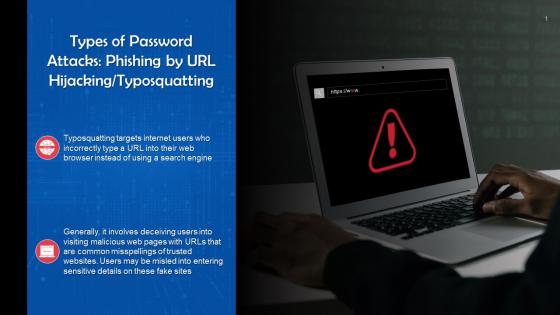 Phishing Password Attack By URL Hijacking Or Typosquatting Training Ppt
Phishing Password Attack By URL Hijacking Or Typosquatting Training PptPresenting Phishing Password Attack by URL Hijacking or Typosquatting. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. It is well crafted and designed by our PowerPoint specialists. Suitable for use by managers, employees, and organizations. You can edit the color, text, icon, and font size to suit your requirements. The PPT also supports Google Slides. Even Premium Customer Support is also available. Download now and present with confidence.
-
 Clone Phishing As A Type Of Password Attack Training Ppt
Clone Phishing As A Type Of Password Attack Training PptPresenting Clone Phishing as a Type of Password Attack. This PPT presentation is thoroughly researched and each slide consists of appropriate content. Designed by PowerPoint specialists, this PPT is fully customizable alter the colors, text, icons, and font size to meet your needs. Compatible with Google Slides and backed by superior customer support. Download today to deliver your presentation confidently.
-
 Phishing Password Attack By UI Redressing And Iframe Overlay Training Ppt
Phishing Password Attack By UI Redressing And Iframe Overlay Training PptPresenting Phishing Password Attack by UI Redressing and iFrame Overlay. This PPT presentation is meticulously researched and each slide consists of relevant content. Designed by SlideTeams PowerPoint experts, this PPT is fully customizable alter the colors, text, icons, and font size to meet your requirements. Compatible with Google Slides and backed by excellent customer support. Download to present with poise and assurance.
-
 Phishing Attack Powerpoint PPT Template Bundles
Phishing Attack Powerpoint PPT Template BundlesIf you require a professional template with great design, then this Phishing Attack Powerpoint PPT Template Bundles is an ideal fit for you. Deploy it to enthrall your audience and increase your presentation threshold with the right graphics, images, and structure. Portray your ideas and vision using twelve slides included in this complete deck. This template is suitable for expert discussion meetings presenting your views on the topic. With a variety of slides having the same thematic representation, this template can be regarded as a complete package. It employs some of the best design practices, so everything is well structured. Not only this, it responds to all your needs and requirements by quickly adapting itself to the changes you make. This PPT slideshow is available for immediate download in PNG, JPG, and PDF formats, further enhancing its usability. Grab it by clicking the download button.
-
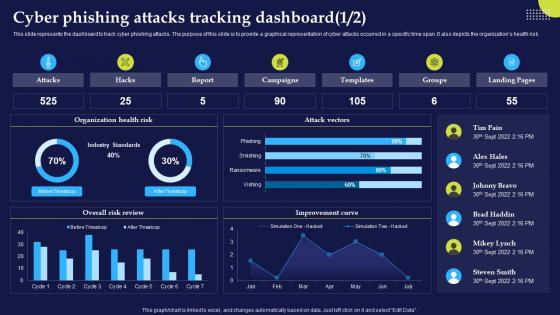 Phishing Attacks And Strategies To Mitigate Them V2 Cyber Phishing Attacks Tracking Dashboard
Phishing Attacks And Strategies To Mitigate Them V2 Cyber Phishing Attacks Tracking DashboardThis slide represents the dashboard to track cyber phishing attacks. The purpose of this slide is to provide a graphical representation of cyber attacks occurred in a specific time span. It also depicts the organizations health risk. Deliver an outstanding presentation on the topic using this Phishing Attacks And Strategies To Mitigate Them V2 Cyber Phishing Attacks Tracking Dashboard. Dispense information and present a thorough explanation of Dashboard To Track, Cyber Phishing Attacks, Graphical Representation, Specific Time Span, Organizations Health Risk using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
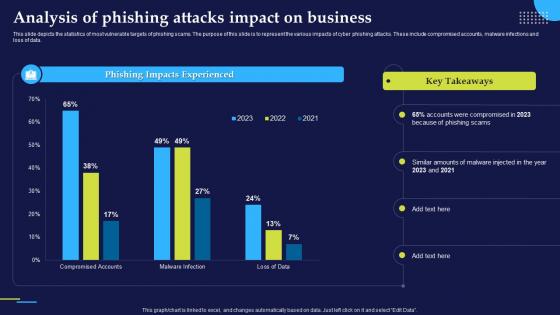 Phishing Attacks And Strategies To Mitigate Them V2 Analysis Of Phishing Attacks Impact On Business
Phishing Attacks And Strategies To Mitigate Them V2 Analysis Of Phishing Attacks Impact On BusinessThis slide depicts the statistics of most vulnerable targets of phishing scams. The purpose of this slide is to represent the various impacts of cyber phishing attacks. These include compromised accounts, malware infections and loss of data. Deliver an outstanding presentation on the topic using this Phishing Attacks And Strategies To Mitigate Them V2 Analysis Of Phishing Attacks Impact On Business. Dispense information and present a thorough explanation of Analysis Of Phishing Attacks, Cyber Phishing Attacks, Malware Infections, Targets Of Phishing Scams using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
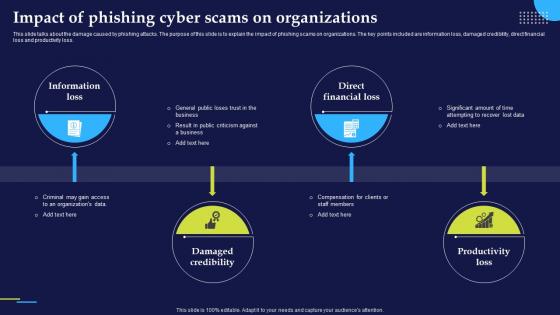 Phishing Attacks And Strategies To Mitigate Them V2 Impact Of Phishing Cyber Scams On Organizations
Phishing Attacks And Strategies To Mitigate Them V2 Impact Of Phishing Cyber Scams On OrganizationsThis slide talks about the damage caused by phishing attacks. The purpose of this slide is to explain the impact of phishing scams on organizations. The key points included are information loss, damaged credibility, direct financial loss and productivity loss. Increase audience engagement and knowledge by dispensing information using Phishing Attacks And Strategies To Mitigate Them V2 Impact Of Phishing Cyber Scams On Organizations. This template helps you present information on four stages. You can also present information on Direct Financial Loss, Productivity Loss, Damaged Credibility, Phishing Cyber Scams using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Targeted Industries Of Cyber Phishing Attacks
Phishing Attacks And Strategies To Mitigate Them V2 Targeted Industries Of Cyber Phishing AttacksThis slide represents the statistics of most targeted industries of phishing scams. The purpose of this slide is to outline the various sectors which are more prone to phishing attacks. These industries are retail, manufacturing, food and beverage, tech, etc. Deliver an outstanding presentation on the topic using this Phishing Attacks And Strategies To Mitigate Them V2 Targeted Industries Of Cyber Phishing Attacks. Dispense information and present a thorough explanation of Phishing Scams, Phishing Attacks, Manufacturing, Food And Beverage using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Vishing Cyber Scams In Different Businesses
Phishing Attacks And Strategies To Mitigate Them V2 Vishing Cyber Scams In Different BusinessesThis slide demonstrates the various types of vishing scams. The purpose of this slide is to illustrate the ways in which attackers conduct scams in different businesses using vishing technique. These are banking vishing and internal revenue service vishing. Present the topic in a bit more detail with this Phishing Attacks And Strategies To Mitigate Them V2 Vishing Cyber Scams In Different Businesses. Use it as a tool for discussion and navigation on Attackers Conduct Scams, Vishing Technique, Internal Revenue Service Vishing. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Various Types Of Crypto Phishing Attacks Securing Blockchain Transactions A Beginners Guide BCT SS V
Various Types Of Crypto Phishing Attacks Securing Blockchain Transactions A Beginners Guide BCT SS VThe following slide illustrates various types of phishing attacks to analyze how cryptocurrency funds are stolen from blockchain network. It includes elements such as spear, whaling, clone, spoof emails, accessibility to personal details, replacing original link with fake one, etc. Increase audience engagement and knowledge by dispensing information using Various Types Of Crypto Phishing Attacks Securing Blockchain Transactions A Beginners Guide BCT SS V. This template helps you present information on three stages. You can also present information on Spear Phishing, Whaling Phishing, Clone Phishing using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Various Types Of Crypto Phishing Attacks Guide For Blockchain BCT SS V
Various Types Of Crypto Phishing Attacks Guide For Blockchain BCT SS VThe following slide illustrates various types of phishing attacks to analyze how cryptocurrency funds are stolen from blockchain network. It includes elements such as spear, whaling, clone, spoof emails, accessibility to personal details, replacing original link with fake one, etc. Introducing Various Types Of Crypto Phishing Attacks Guide For Blockchain BCT SS V to increase your presentation threshold. Encompassed with three stages, this template is a great option to educate and entice your audience. Dispence information on Spear Phishing, Whaling Phishing, Clone Phishing using this template. Grab it now to reap its full benefits.
-
 Cyber Threats In Blockchain Various Types Of Crypto Phishing Attacks BCT SS V
Cyber Threats In Blockchain Various Types Of Crypto Phishing Attacks BCT SS VThe following slide illustrates various types of phishing attacks to analyze how cryptocurrency funds are stolen from blockchain network. It includes elements such as spear, whaling, clone, spoof emails, accessibility to personal details, replacing original link with fake one, etc. Increase audience engagement and knowledge by dispensing information using Cyber Threats In Blockchain Various Types Of Crypto Phishing Attacks BCT SS V This template helps you present information on Three stages. You can also present information on Spear Phishing, Whaling Phishing, Clone Phishing using this PPT design. This layout is completely editable so personaize it now
-
 Healthcare Cybersecurity Icon For Protection Against Phishing Attacks
Healthcare Cybersecurity Icon For Protection Against Phishing AttacksIntroducing our Healthcare Cybersecurity Icon For Protection Against Phishing Attacks set of slides. The topics discussed in these slides are Healthcare Cybersecurity Icon, Protection Against Phishing Attacks. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
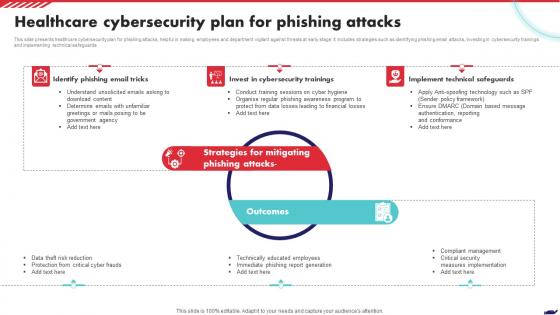 Healthcare Cybersecurity Plan For Phishing Attacks
Healthcare Cybersecurity Plan For Phishing AttacksThis slide presents healthcare cybersecurity plan for phishing attacks, helpful in making employees and department vigilant against threats at early stage. It includes strategies such as identifying phishing email attacks, investing in cybersecurity trainings and implementing technical safeguards Presenting our set of slides with Healthcare Cybersecurity Plan For Phishing Attacks. This exhibits information on Six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Phishing Email Tricks, Cybersecurity Trainings, Technical Safeguards.
-
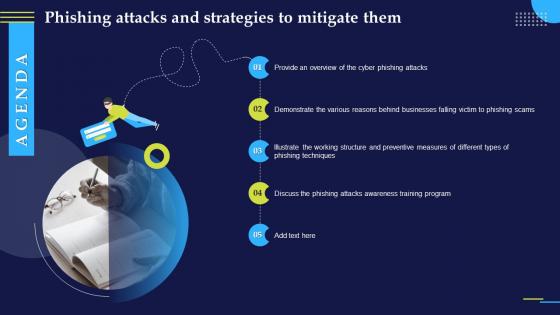 Agenda For Phishing Attacks And Strategies To Mitigate Them V2 Ppt Ideas Infographic Template
Agenda For Phishing Attacks And Strategies To Mitigate Them V2 Ppt Ideas Infographic TemplateIntroducing Agenda For Phishing Attacks And Strategies To Mitigate Them V2 Ppt Ideas Infographic Template to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Cyber Phishing Attacks, Phishing Techniques, Working Structure, Awareness Training Program, using this template. Grab it now to reap its full benefits.
-
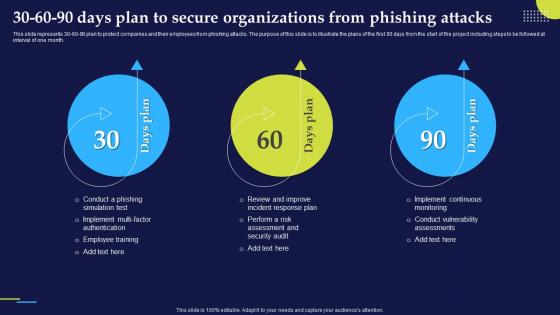 Phishing Attacks And Strategies To Mitigate Them V2 30 60 90 Days Plan To Secure Organizations
Phishing Attacks And Strategies To Mitigate Them V2 30 60 90 Days Plan To Secure OrganizationsThis slide represents 30-60-90 plan to protect companies and their employees from phishing attacks. The purpose of this slide is to illustrate the plans of the first 90 days from the start of the project including steps to be followed at interval of one month. Increase audience engagement and knowledge by dispensing information using Phishing Attacks And Strategies To Mitigate Them V2 30 60 90 Days Plan To Secure Organizations. This template helps you present information on three stages. You can also present information on Phishing Attacks, Implement Continuous Monitoring, Conduct Vulnerability Assessments using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Phishing Attacks And Strategies To Mitigate Them V2 About Angler Phishing Working And Example
Phishing Attacks And Strategies To Mitigate Them V2 About Angler Phishing Working And ExampleThis slide talks about the angler phishing attacks conducted on internet using social media platforms. The purpose of this slide is to illustrate how fraudulent tweets or texts containing malicious links and misleading information, can be used by scammers to trick individuals. Present the topic in a bit more detail with this Phishing Attacks And Strategies To Mitigate Them V2 About Angler Phishing Working And Example. Use it as a tool for discussion and navigation on Angler Phishing Attacks, Social Media Platforms, Fraudulent Tweets, Texts Containing Malicious, Misleading Information. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Phishing Attacks And Strategies To Mitigate Them V2 About Email Phishing Overview And Impact
Phishing Attacks And Strategies To Mitigate Them V2 About Email Phishing Overview And ImpactThis slide talks about the email phishing cyber scams in which attacker sends fake mails to the target. The purpose of this slide to provide few examples of cyber phishing emails containing malicious links and attachments to target different organizations. Introducing Phishing Attacks And Strategies To Mitigate Them V2 About Email Phishing Overview And Impact to increase your presentation threshold. Encompassed with seven stages, this template is a great option to educate and entice your audience. Dispence information on Legitimate Business, Generic Requests, Dangerous Websites, Login Information, using this template. Grab it now to reap its full benefits.
-
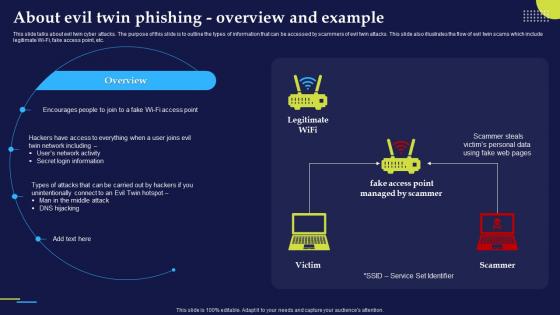 Phishing Attacks And Strategies To Mitigate Them V2 About Evil Twin Phishing Overview And Example
Phishing Attacks And Strategies To Mitigate Them V2 About Evil Twin Phishing Overview And ExampleThis slide talks about evil twin cyber attacks. The purpose of this slide is to outline the types of information that can be accessed by scammers of evil twin attacks. This slide also illustrates the flow of evil twin scams which include legitimate Wi-Fi, fake access point, etc. Deliver an outstanding presentation on the topic using this Phishing Attacks And Strategies To Mitigate Them V2 About Evil Twin Phishing Overview And Example. Dispense information and present a thorough explanation of Users Network Activity, Secret Login Information, Twin Cyber Attacks, Service Set Identifier using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Phishing Attacks And Strategies To Mitigate Them V2 About Identity Theft Overview And Techniques
Phishing Attacks And Strategies To Mitigate Them V2 About Identity Theft Overview And TechniquesThis slide talks about the major crime committed by phishers named as identity theft. The purpose of this slide is to outline the ways of stealing information such as robbery, computer fraud, social networking sites, mail theft and dumpster diving. Present the topic in a bit more detail with this Phishing Attacks And Strategies To Mitigate Them V2 About Identity Theft Overview And Techniques. Use it as a tool for discussion and navigation on Shady Internet Schemes, Private Government Records, Social Media Account, Social Security Card. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
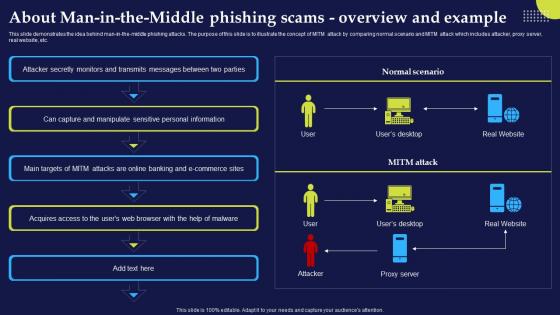 Phishing Attacks And Strategies To Mitigate Them V2 About Man In The Middle Phishing Scams Overview
Phishing Attacks And Strategies To Mitigate Them V2 About Man In The Middle Phishing Scams OverviewThis slide demonstrates the idea behind man-in-the-middle phishing attacks. The purpose of this slide is to illustrate the concept of MITM attack by comparing normal scenario and MITM attack which includes attacker, proxy server, real website, etc. Deliver an outstanding presentation on the topic using this Phishing Attacks And Strategies To Mitigate Them V2 About Man In The Middle Phishing Scams Overview. Dispense information and present a thorough explanation of Attacker Secretly Monitors, Manipulate Sensitive, Personal Information, Online Banking using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
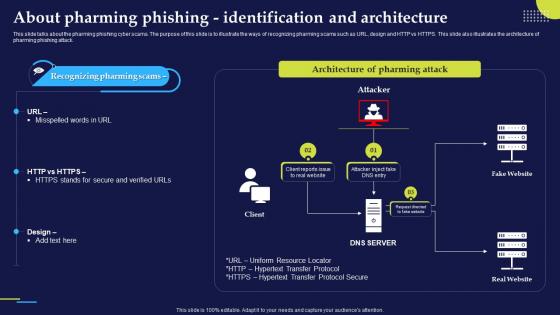 Phishing Attacks And Strategies To Mitigate Them V2 About Pharming Phishing Identification
Phishing Attacks And Strategies To Mitigate Them V2 About Pharming Phishing IdentificationThis slide talks about the pharming phishing cyber scams. The purpose of this slide is to illustrate the ways of recognizing pharming scams such as URL, design and HTTP vs HTTPS. This slide also illustrates the architecture of pharming phishing attack. Present the topic in a bit more detail with this Phishing Attacks And Strategies To Mitigate Them V2 About Pharming Phishing Identification. Use it as a tool for discussion and navigation on Uniform Resource Locator, Hypertext Transfer Protocol, Hypertext Transfer Protocol Secure. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
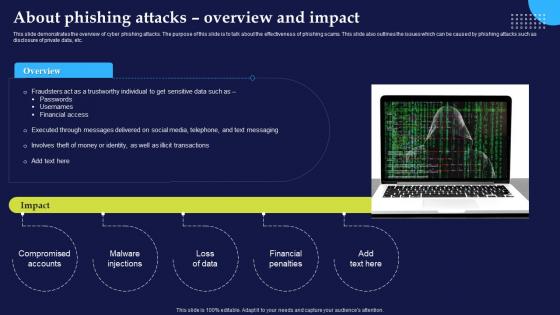 Phishing Attacks And Strategies To Mitigate Them V2 About Phishing Attacks Overview And Impact
Phishing Attacks And Strategies To Mitigate Them V2 About Phishing Attacks Overview And ImpactThis slide demonstrates the overview of cyber phishing attacks. The purpose of this slide is to talk about the effectiveness of phishing scams. This slide also outlines the issues which can be caused by phishing attacks such as disclosure of private data, etc. Increase audience engagement and knowledge by dispensing information using Phishing Attacks And Strategies To Mitigate Them V2 About Phishing Attacks Overview And Impact. This template helps you present information on five stages. You can also present information on Malware Injections, Compromised Accounts, Financial Penalties, Illicit Transactions using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
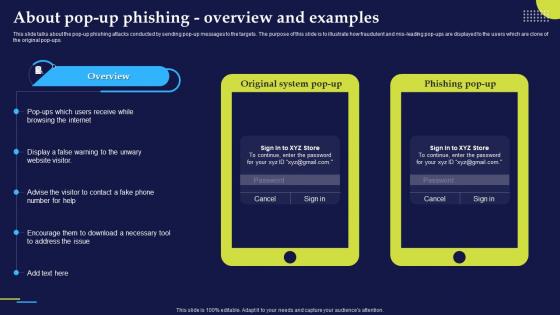 Phishing Attacks And Strategies To Mitigate Them V2 About Pop Up Phishing Overview And Examples
Phishing Attacks And Strategies To Mitigate Them V2 About Pop Up Phishing Overview And ExamplesThis slide talks about the pop-up phishing attacks conducted by sending pop-up messages to the targets. The purpose of this slide is to illustrate how fraudulent and mis-leading pop-ups are displayed to the users which are clone of the original pop-ups. Deliver an outstanding presentation on the topic using this Phishing Attacks And Strategies To Mitigate Them V2 About Pop Up Phishing Overview And Examples. Dispense information and present a thorough explanation of Original System Pop Up, Phishing Pop Up, Fraudulent, Mis Leading Pop Ups using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Phishing Attacks And Strategies To Mitigate Them V2 About Search Engine Phishing Overview
Phishing Attacks And Strategies To Mitigate Them V2 About Search Engine Phishing OverviewThis slide talks about search engine phishing scams. The purpose of this slide is to explain how phishers use their own-built websites to trick victims. This slide also represents examples of search engine phishing websites which are indexed by reliable browsers. Introducing Phishing Attacks And Strategies To Mitigate Them V2 About Search Engine Phishing Overview to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Commit Fraud Against User, Steal Users Identity, Harm Victims Reputation, Reliable Search Engines, using this template. Grab it now to reap its full benefits.
-
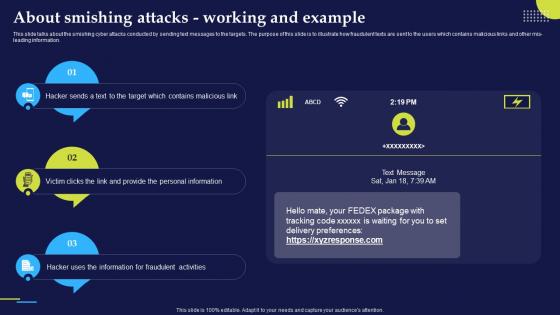 Phishing Attacks And Strategies To Mitigate Them V2 About Smishing Attacks Working And Example
Phishing Attacks And Strategies To Mitigate Them V2 About Smishing Attacks Working And ExampleThis slide talks about the smishing cyber attacks conducted by sending text messages to the targets. The purpose of this slide is to illustrate how fraudulent texts are sent to the users which contains malicious links and other mis-leading information. Increase audience engagement and knowledge by dispensing information using Phishing Attacks And Strategies To Mitigate Them V2 About Smishing Attacks Working And Example. This template helps you present information on three stages. You can also present information on Personal Information, Contains Malicious Link, Fraudulent Activities, Smishing Attacks using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
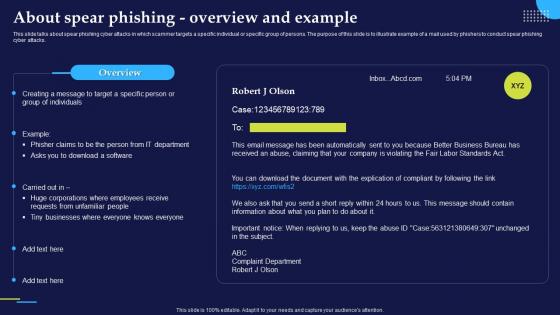 Phishing Attacks And Strategies To Mitigate Them V2 About Spear Phishing Overview And Example
Phishing Attacks And Strategies To Mitigate Them V2 About Spear Phishing Overview And ExampleThis slide talks about spear phishing cyber attacks in which scammer targets a specific individual or specific group of persons. The purpose of this slide is to illustrate example of a mail used by phishers to conduct spear phishing cyber attacks. Present the topic in a bit more detail with this Phishing Attacks And Strategies To Mitigate Them V2 About Spear Phishing Overview And Example. Use it as a tool for discussion and navigation on Huge Corporations, Employees Receive Requests, Unfamiliar People, Spear Phishing. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Phishing Attacks And Strategies To Mitigate Them V2 About Vishing Attacks Overview And Identification
Phishing Attacks And Strategies To Mitigate Them V2 About Vishing Attacks Overview And IdentificationThis slide talks about the vishing cyber attacks. The purpose of this slide is to explain the vishing technique used by phishers to scam victims. This slide also outlines the signs of vishing attack such as call from unknown number, act as an authority, etc. Deliver an outstanding presentation on the topic using this Phishing Attacks And Strategies To Mitigate Them V2 About Vishing Attacks Overview And Identification. Dispense information and present a thorough explanation of Personal Information, Fraudsters Fake, Internal Revenue Service, Signs Of Vishing Attack using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
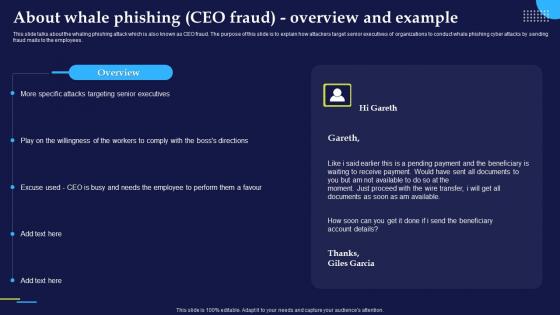 Phishing Attacks And Strategies To Mitigate Them V2 About Whale Phishing CEO Fraud Overview
Phishing Attacks And Strategies To Mitigate Them V2 About Whale Phishing CEO Fraud OverviewThis slide talks about the whaling phishing attack which is also known as CEO fraud. The purpose of this slide is to explain how attackers target senior executives of organizations to conduct whale phishing cyber attacks by sending fraud mails to the employees. Present the topic in a bit more detail with this Phishing Attacks And Strategies To Mitigate Them V2 About Whale Phishing CEO Fraud Overview. Use it as a tool for discussion and navigation on Attacks Targeting Senior Executives, Fraud Mails, Phishing Cyber Attacks. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Benefits Of Comprehensive Training Programs
Phishing Attacks And Strategies To Mitigate Them V2 Benefits Of Comprehensive Training ProgramsThis slide outlines the benefits of comprehensive training programs in organizations. These include align with company database, instructional library, auto-enrolment service, inform about real risks, track and evaluate and plan a year ahead. Introducing Phishing Attacks And Strategies To Mitigate Them V2 Benefits Of Comprehensive Training Programs to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Instructional Library, Track And Evaluate, Automatically Manage Phishing Trainees, Cyber Security Microlessons, using this template. Grab it now to reap its full benefits.
-
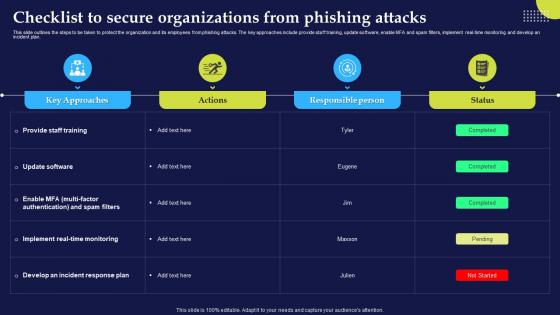 Phishing Attacks And Strategies To Mitigate Them V2 Checklist To Secure Organizations From Phishing
Phishing Attacks And Strategies To Mitigate Them V2 Checklist To Secure Organizations From PhishingThis slide outlines the steps to be taken to protect the organization and its employees from phishing attacks. The key approaches include provide staff training, update software, enable MFA and spam filters, implement real-time monitoring and develop an incident plan. Present the topic in a bit more detail with this Phishing Attacks And Strategies To Mitigate Them V2 Checklist To Secure Organizations From Phishing. Use it as a tool for discussion and navigation on Phishing Attacks, Real Time Monitoring, Spam Filters, Multi Factor Authentication. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Clone Phishing Attacks Preventive Measures
Phishing Attacks And Strategies To Mitigate Them V2 Clone Phishing Attacks Preventive MeasuresThis slide talks about the various steps that can be taken to prevent clone phishing attacks. These include review senders address, preview links before opening them, use a password manager, investigate spoofed replies, double check URL addresses, etc. Increase audience engagement and knowledge by dispensing information using Phishing Attacks And Strategies To Mitigate Them V2 Clone Phishing Attacks Preventive Measures. This template helps you present information on eight stages. You can also present information on Investigate Spoofed Replies, Clone Phishing Attacks Preventive, Resemble Authentic Email Addresses using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Different Types Of Smishing Cyber Scams
Phishing Attacks And Strategies To Mitigate Them V2 Different Types Of Smishing Cyber ScamsThis slide talks about the various types of smishing cyber attacks. The purpose of this slide is to briefly explain different techniques of smishing scams used by the attackers to scam users. These are covid-19 smishing, financial services smishing, etc. Introducing Phishing Attacks And Strategies To Mitigate Them V2 Different Types Of Smishing Cyber Scams to increase your presentation threshold. Encompassed with five stages, this template is a great option to educate and entice your audience. Dispence information on Smishing Scams, Financial Services Smishing, Gift Smishing, Customer Support Smishing, using this template. Grab it now to reap its full benefits.
-
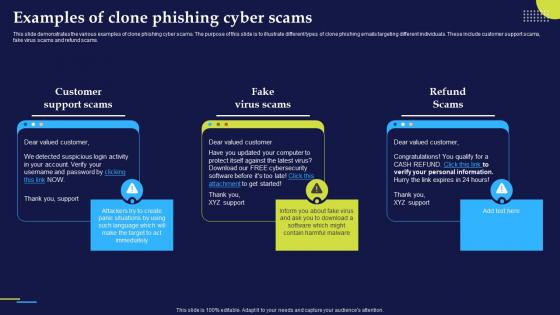 Phishing Attacks And Strategies To Mitigate Them V2 Examples Of Clone Phishing Cyber Scams
Phishing Attacks And Strategies To Mitigate Them V2 Examples Of Clone Phishing Cyber ScamsThis slide demonstrates the various examples of clone phishing cyber scams. The purpose of this slide is to illustrate different types of clone phishing emails targeting different individuals. These include customer support scams, fake virus scams and refund scams. Increase audience engagement and knowledge by dispensing information using Phishing Attacks And Strategies To Mitigate Them V2 Examples Of Clone Phishing Cyber Scams. This template helps you present information on three stages. You can also present information on Customer Support Scams, Fake Virus Scams, Refund Scams, Clone Phishing Cyber Scams using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
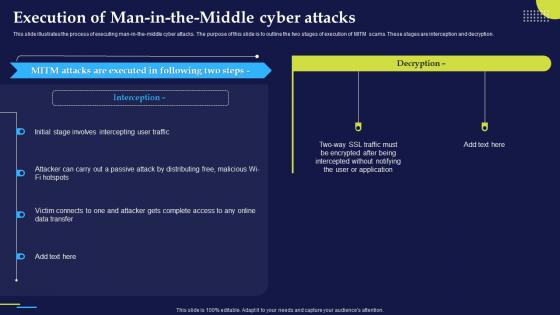 Phishing Attacks And Strategies To Mitigate Them V2 Execution Of Man In The Middle Cyber Attacks
Phishing Attacks And Strategies To Mitigate Them V2 Execution Of Man In The Middle Cyber AttacksThis slide illustrates the process of executing man-in-the-middle cyber attacks. The purpose of this slide is to outline the two stages of execution of MITM scams. These stages are interception and decryption. Present the topic in a bit more detail with this Phishing Attacks And Strategies To Mitigate Them V2 Execution Of Man In The Middle Cyber Attacks. Use it as a tool for discussion and navigation on Cyber Attacks, Interception And Decryption, Online Data Transfer, Intercepting User Traffic. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Phishing Attacks And Strategies To Mitigate Them V2 For Table Of Contents
Phishing Attacks And Strategies To Mitigate Them V2 For Table Of ContentsIntroducing Phishing Attacks And Strategies To Mitigate Them V2 For Table Of Contents to increase your presentation threshold. Encompassed with one stages, this template is a great option to educate and entice your audience. Dispence information on Overview And Identification, Working, Vishing Cyber Scams In Businesses, Preventive Measures, using this template. Grab it now to reap its full benefits.
-
 Phishing Attacks And Strategies To Mitigate Them V2 Guidelines To Stay Safe From Phishing Scams
Phishing Attacks And Strategies To Mitigate Them V2 Guidelines To Stay Safe From Phishing ScamsThis slide outlines the various preventive measures to stay safe from phishing attacks. These include know how to spot phishing scams, avoid clicking that link, install free anti-phishing extensions, change passwords regularly, install firewalls, never miss updates, etc. Increase audience engagement and knowledge by dispensing information using Phishing Attacks And Strategies To Mitigate Them V2 Guidelines To Stay Safe From Phishing Scams. This template helps you present information on five stages. You can also present information on Reveal Sensitive Information, Change Passwords Regularly, Information To Unsafe Websites, Avoid Clicking That Link using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
 Phishing Attacks And Strategies To Mitigate Them V2 How Does A Phishing Attack Work
Phishing Attacks And Strategies To Mitigate Them V2 How Does A Phishing Attack WorkThis slide demonstrates the working flow of a phishing attack. The purpose of this slide is to outline the various phases of phishing scams such as campaign crafted, payloads, impersonation, execution, ransomware and encrypts on target. Introducing Phishing Attacks And Strategies To Mitigate Them V2 How Does A Phishing Attack Work to increase your presentation threshold. Encompassed with six stages, this template is a great option to educate and entice your audience. Dispence information on Campaign Crafted, Payloads, Impersonation, Execution, Encrypts On Target, using this template. Grab it now to reap its full benefits.
-
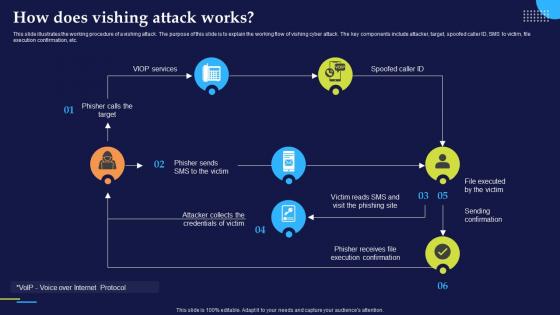 Phishing Attacks And Strategies To Mitigate Them V2 How Does Vishing Attack Works
Phishing Attacks And Strategies To Mitigate Them V2 How Does Vishing Attack WorksThis slide illustrates the working procedure of a vishing attack. The purpose of this slide is to explain the working flow of vishing cyber attack. The key components include attacker, target, spoofed caller ID, SMS to victim, file execution confirmation, etc. Present the topic in a bit more detail with this Phishing Attacks And Strategies To Mitigate Them V2 How Does Vishing Attack Works. Use it as a tool for discussion and navigation on Execution Confirmation, Sending Confirmation, Vishing Attack Works. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
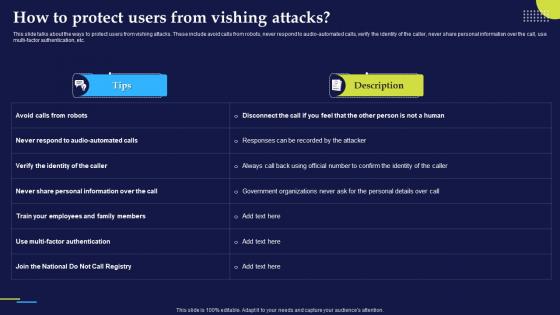 Phishing Attacks And Strategies To Mitigate Them V2 How To Protect Users From Vishing Attacks
Phishing Attacks And Strategies To Mitigate Them V2 How To Protect Users From Vishing AttacksThis slide talks about the ways to protect users from vishing attacks. These include avoid calls from robots, never respond to audio-automated calls, verify the identity of the caller, never share personal information over the call, use multi-factor authentication, etc. Deliver an outstanding presentation on the topic using this Phishing Attacks And Strategies To Mitigate Them V2 How To Protect Users From Vishing Attacks. Dispense information and present a thorough explanation of Vishing Attacks, Audio Automated Calls, Personal Information, Multi Factor Authentication using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
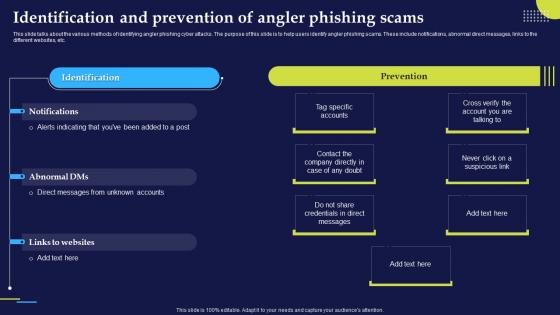 Phishing Attacks And Strategies To Mitigate Them V2 Identification And Prevention Of Angler Phishing
Phishing Attacks And Strategies To Mitigate Them V2 Identification And Prevention Of Angler PhishingThis slide talks about the various methods of identifying angler phishing cyber attacks. The purpose of this slide is to help users identify angler phishing scams. These include notifications, abnormal direct messages, links to the different websites, etc. Present the topic in a bit more detail with this Phishing Attacks And Strategies To Mitigate Them V2 Identification And Prevention Of Angler Phishing. Use it as a tool for discussion and navigation on Identification And Prevention, Angler Phishing Scams, Abnormal Direct Messages, Credentials In Direct Messages. This template is free to edit as deemed fit for your organization. Therefore download it now.


