Blockchain has transformed various industries by offering a secure and transparent way to handle transactions. However, as more people embrace blockchain, the risks of cyber threats also increase. This ultimate guide is here to simplify the complexities of blockchain cybersecurity and equip you with effective strategies to manage these risks. With the aid of straightforward PowerPoint slides, we'll break down the essential principles to safeguard this revolutionary technology. Imagine it as your roadmap to understanding and implementing measures that keep your blockchain interactions secure.
With this guide, you'll not only grasp the basics of blockchain security but also have practical tools and insights to navigate and protect this transformative technology confidently. Let's embark on this journey together, unraveling the world of blockchain in an accessible and easy-to-understand manner.
Understanding Blockchain Security
Before delving into preventive measures, it's essential to grasp the foundational principles of blockchain security.
Decentralization and Security:
Blockchain's strength lies in its decentralized network of nodes, creating resilience against single points of failure. In this structure, each node possesses a complete copy of the entire blockchain. Consensus mechanisms further ensure unanimous agreement on transaction validity.
The distribution of control across the network significantly enhances security through decentralization, reducing vulnerability to attacks or manipulation.
Cryptography:
At the core of blockchain security is cryptography, acting as its backbone. Public and private key pairs play a pivotal role in securing transactions and controlling access to digital assets. Robust encryption methods, exemplified by advanced algorithms like SHA-256 (utilized in Bitcoin), guarantee the integrity of data stored on the blockchain. The implementation of these sophisticated cryptographic techniques is paramount, serving as a critical defense mechanism for safeguarding sensitive information within the blockchain ecosystem against unauthorized access and potential compromise.
Now that you've gained a foundational understanding of how blockchain security operates, let's delve deeper into our blockchain ppt PowerPoint slides. These slides comprehensively cover the challenges, preventive measures, and best practices for navigating the intricacies of blockchain technology.
Security Challenges Faced by Blockchain Technology
While blockchain stands out as a secure and robust technology, it isn't impervious to cyberattacks. Here are some security challenges encountered by blockchain technology:
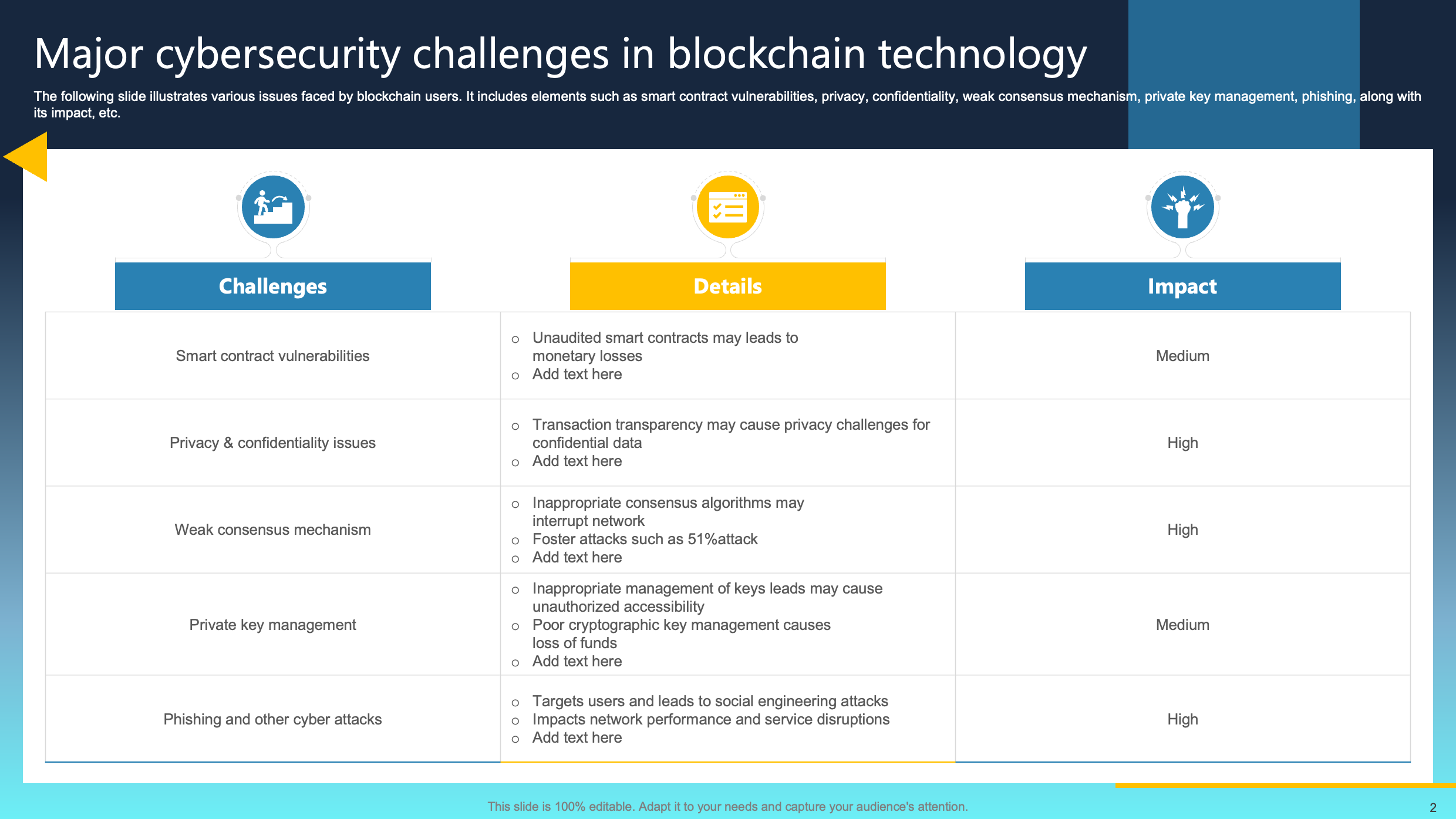
Major Cybersecurity Challenges in Blockchain Technology
This slide highlights diverse challenges confronting blockchain users, encompassing smart contract vulnerabilities, privacy and confidentiality issues, weak consensus mechanisms, and concerns about private key management and phishing attacks.
Smart contract vulnerabilities pose risks of unauthorized access and manipulation, while transparency raises privacy concerns. Fragile consensus mechanisms, like susceptibility to 51% attacks, threaten transaction integrity. Insecure private key management and phishing add layers of vulnerability. The collective impact encompasses financial losses, data breaches, and reputational harm.
Addressing these complexities demands robust security measures and collaborative efforts within the blockchain community to fortify the technology against evolving threats.
Download this PowerPoint Template Now!
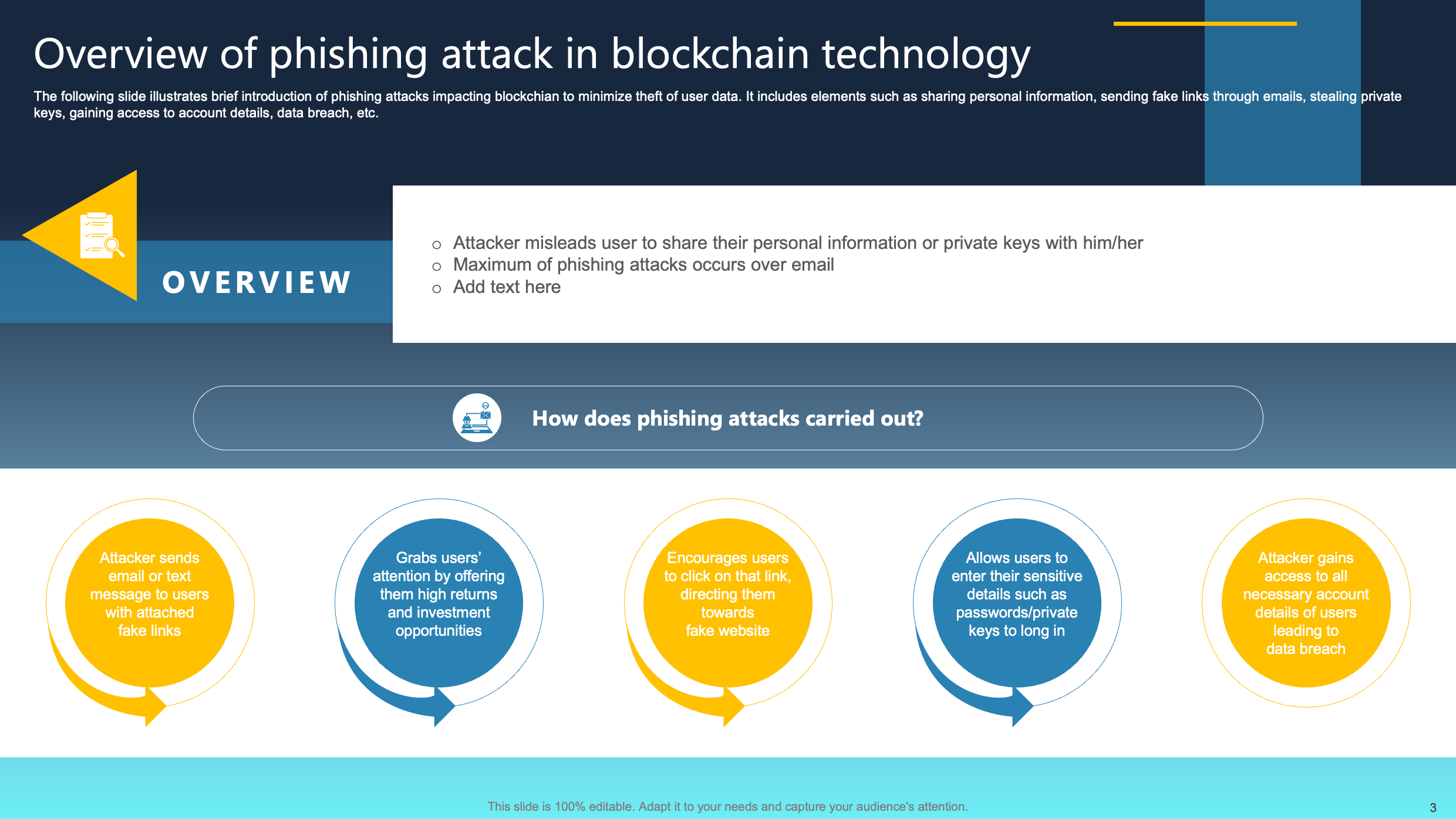
Overview of Phishing Attack in Blockchain Technology
This slide provides a concise overview of phishing attacks targeting blockchain, aiming to mitigate the theft of user data. It outlines key elements such as the sharing of personal information, dissemination of fake links via emails, unauthorized access to private keys, and compromise of account details leading to potential data breaches.
With a thorough understanding of these tactics, users can enhance their awareness and employ preventive measures, contributing to the overall resilience of the blockchain ecosystem against phishing threats and safeguarding sensitive information from unauthorized access and exploitation.
Download this PowerPoint Template Now!
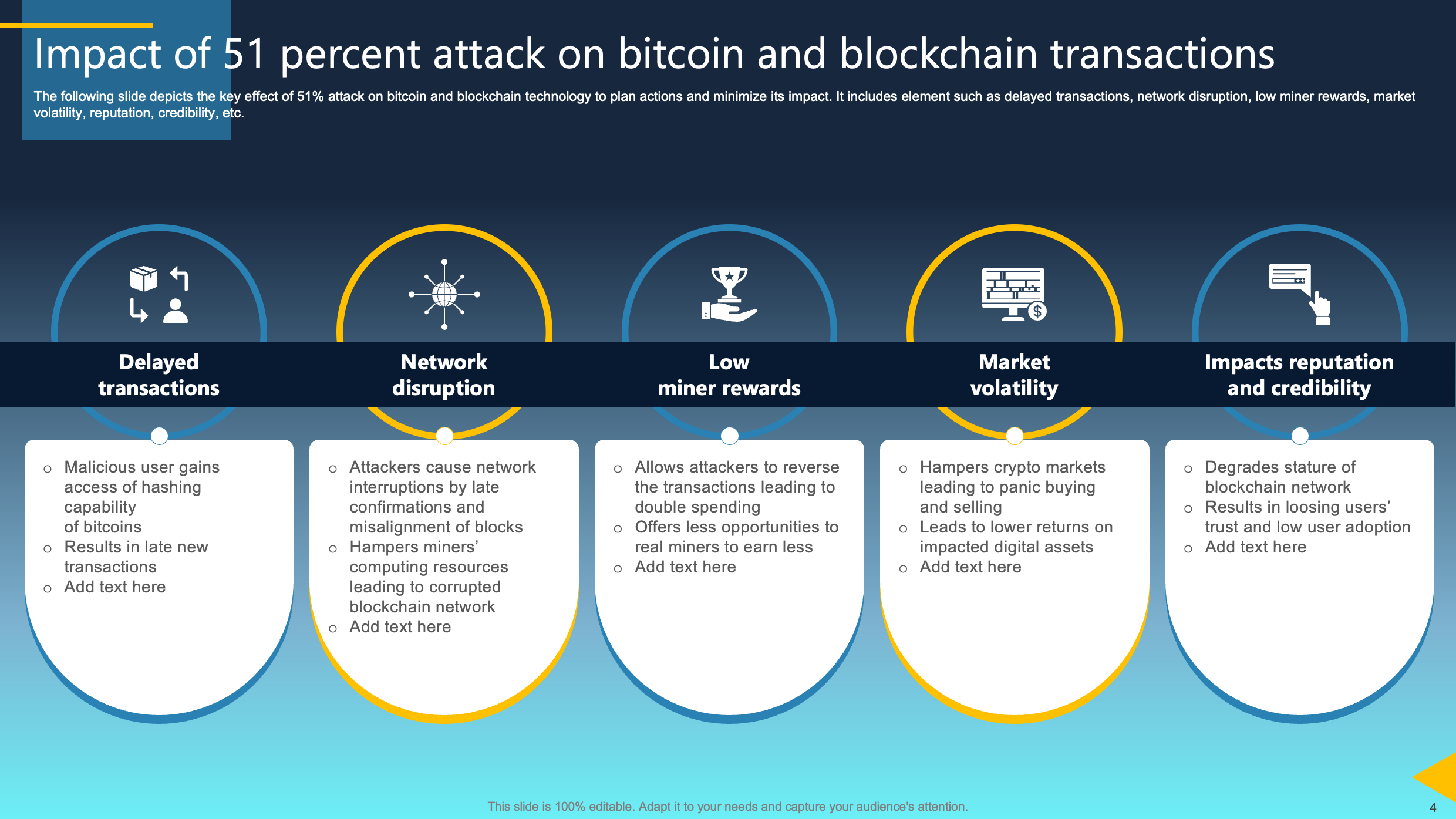
Impact of 51 Percent Attack on Bitcoin and Blockchain Transactions
This slide illustrates the profound impact of a 51% attack on Bitcoin and blockchain technology, emphasizing the need for strategic planning to mitigate its repercussions. Elements encompass delayed transactions, network disruption, diminished miner rewards, heightened market volatility, and implications for reputation and credibility.
With a recognition of these consequences, proactive measures can be devised to minimize the adverse effects, ensuring the resilience of the blockchain network. Effective planning, bolstered by a comprehensive understanding of the potential outcomes of a 51% attack, is essential for sustaining the integrity and functionality of the Bitcoin ecosystem and broader blockchain technology.
Download this PowerPoint Template Now!
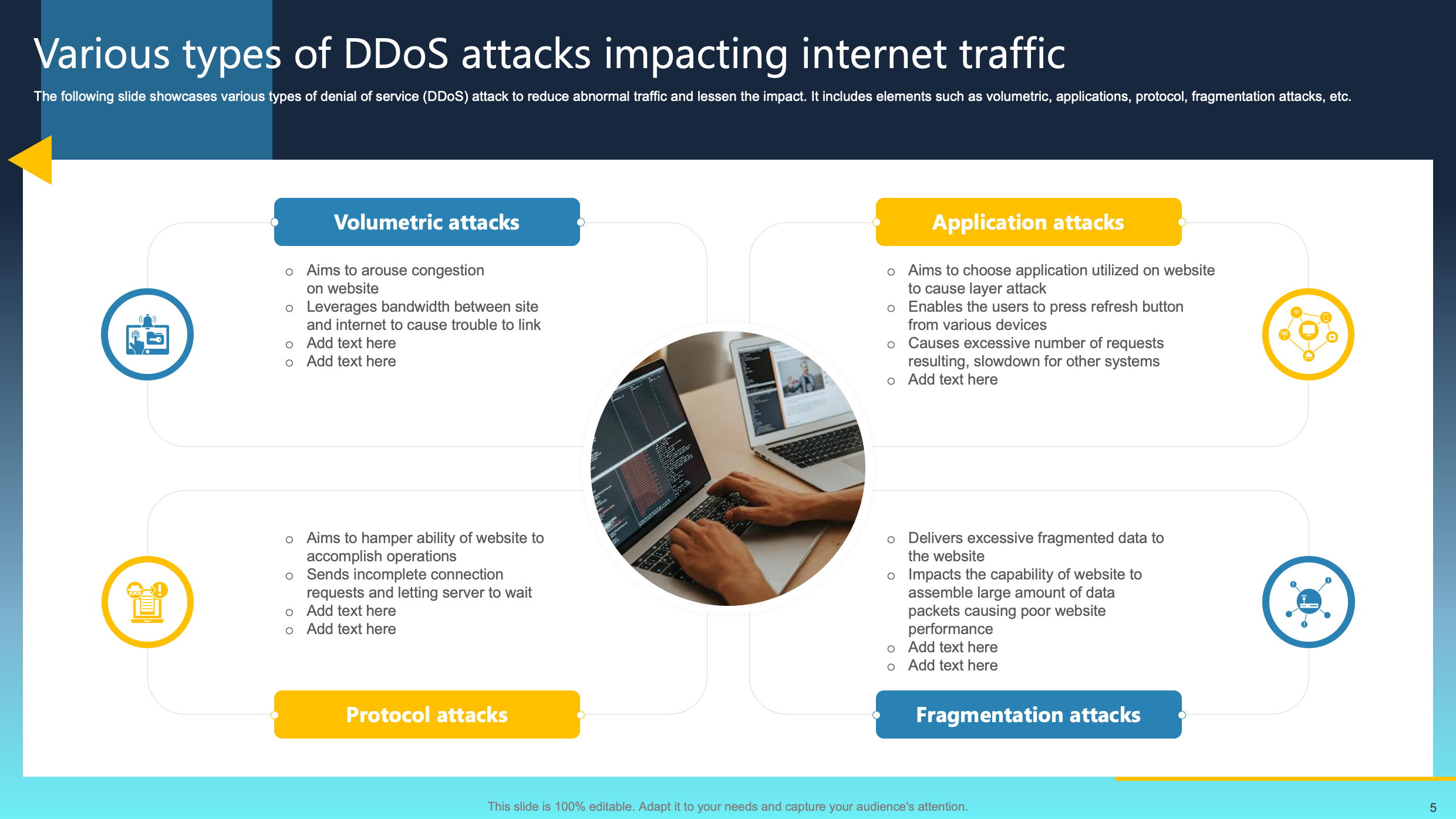
Various Types of DDoS Attacks Impacting Internet Traffic
This slide presents an array of denial-of-service (DDoS) attacks, aiming to mitigate abnormal traffic and diminish their impact. The highlighted elements encompass volumetric attacks, application-based attacks, protocol disruptions, and fragmentation attacks. Understanding these diverse attack vectors is essential for developing effective strategies to counter and reduce their impact.
Recognizing and mitigating the distinctive traits of each type, organizations can bolster their defenses against DDoS threats. This approach ensures the continued functionality and security of their systems in the midst of malicious efforts to overwhelm and disrupt regular operations.
Download this PowerPoint Template Now!
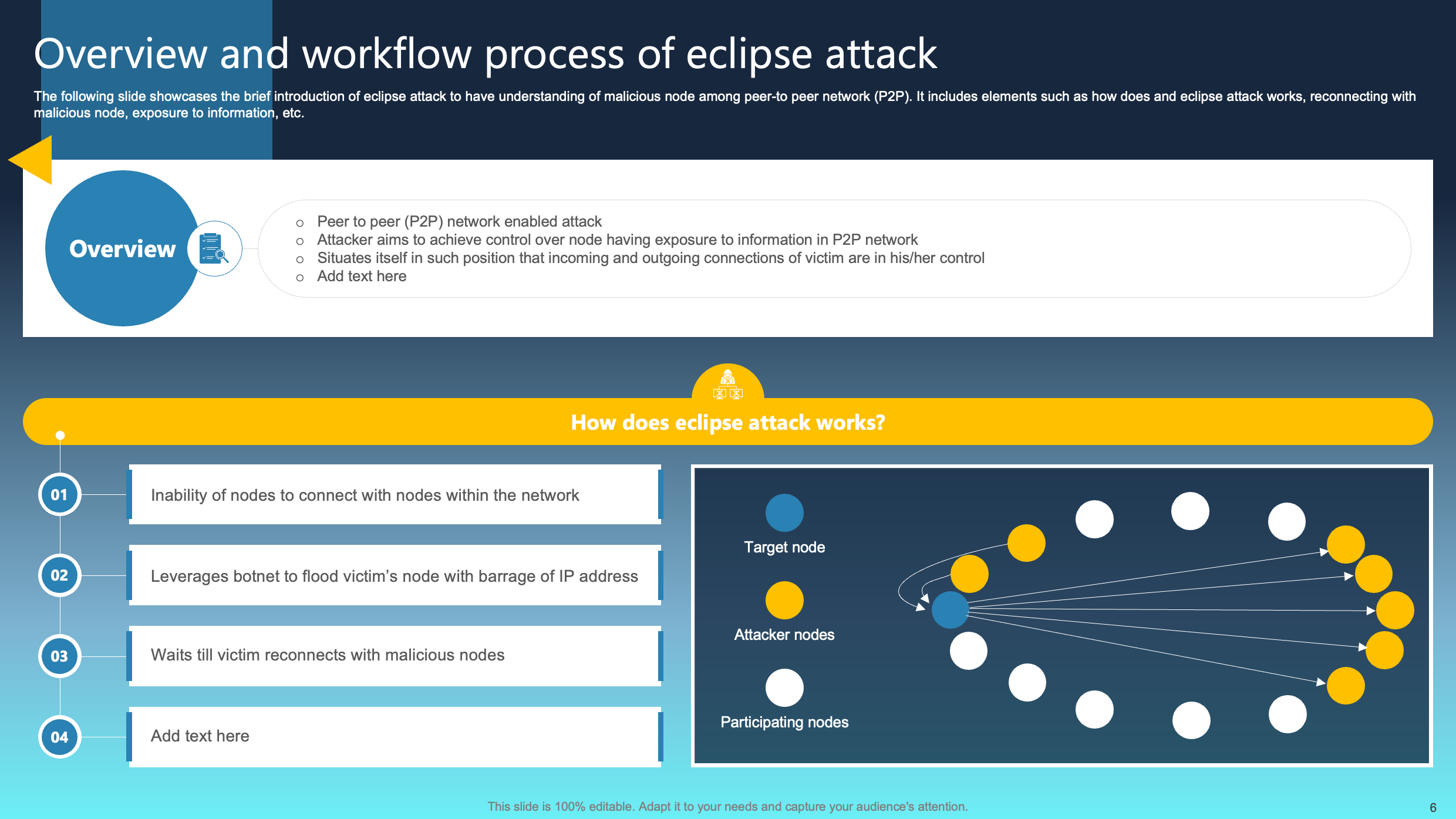
Overview and Workflow Process of Eclipse Attack
This slide offers a concise introduction to the eclipse attack, shedding light on the infiltration of a malicious node within a peer-to-peer network (P2P). It delves into the mechanics of how an eclipse attack operates, emphasizing the process of reconnecting with a malicious node and the subsequent exposure of sensitive information.
Understanding these dynamics empowers users to heighten their awareness and proactively implement preventive measures. This, in turn, reduces the susceptibility of P2P networks to eclipse attacks, ensuring protection against unauthorized access and potential compromises to data security.
Download this PowerPoint Template Now!
Preventive Measures Against Blockchain Cyberattacks
In this section we’ll discover essential tactics for safeguarding against blockchain cyber threats. Explore preventive measures to fortify security, ensuring robust protection and integrity in the face of potential cyberattacks on the blockchain.
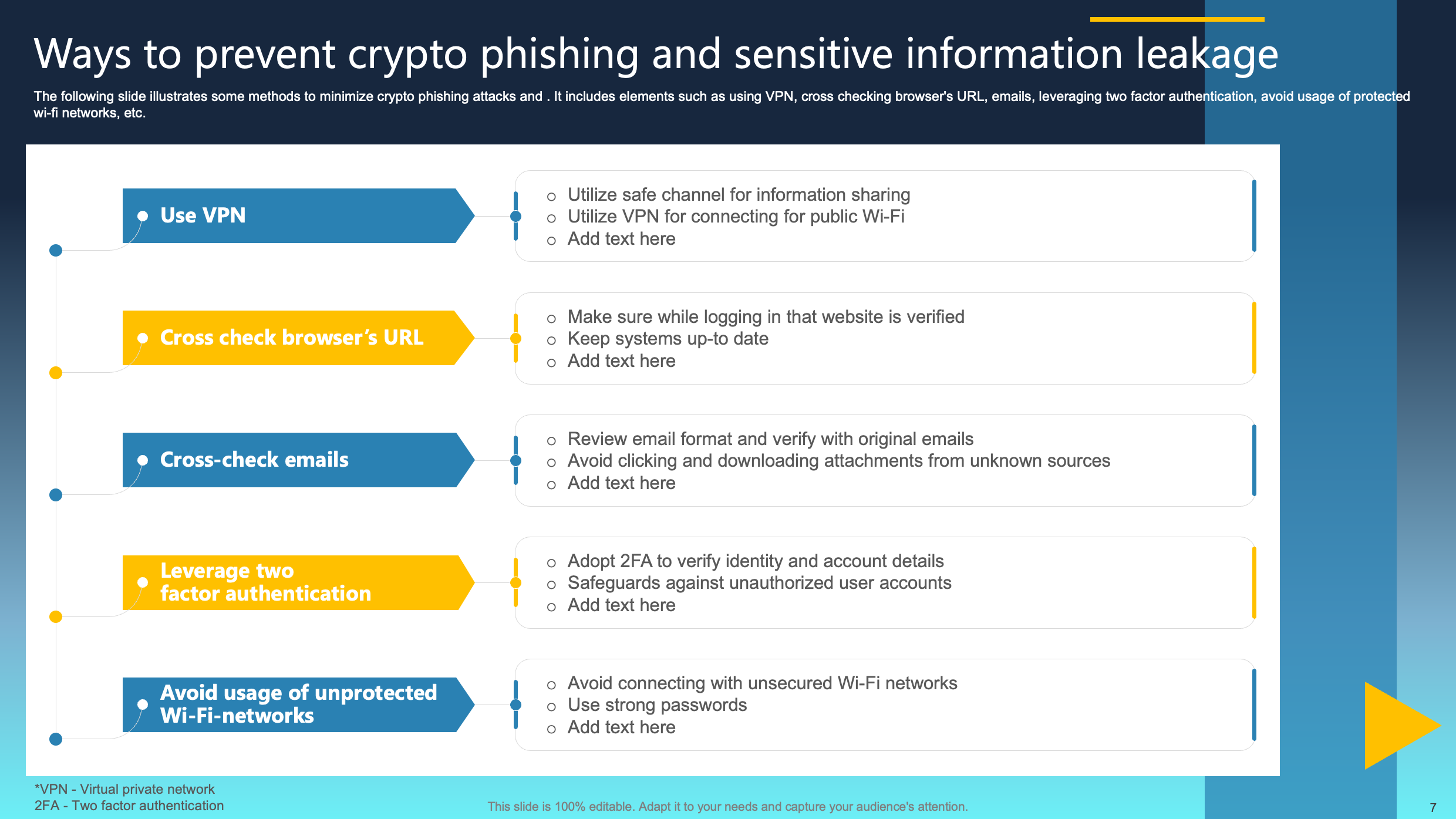
Ways to Prevent Crypto Phishing and Sensitive Information Leakage
This slide outlines effective strategies for mitigating crypto phishing attacks. It advocates the use of a Virtual Private Network (VPN), cross-verification of browser URLs and emails, implementation of two-factor authentication, and caution against utilizing unprotected Wi-Fi networks.
Incorporating these measures allows users to bolster their defenses against phishing attempts, thereby ensuring a more secure cryptocurrency experience. The focus on proactive steps, including the adoption of secure browsing practices and the utilization of additional authentication layers, contributes to a robust defense against the continually evolving landscape of crypto phishing threats. This, in turn, fosters a safer and more secure digital environment for users.
Download this PowerPoint Template Now!
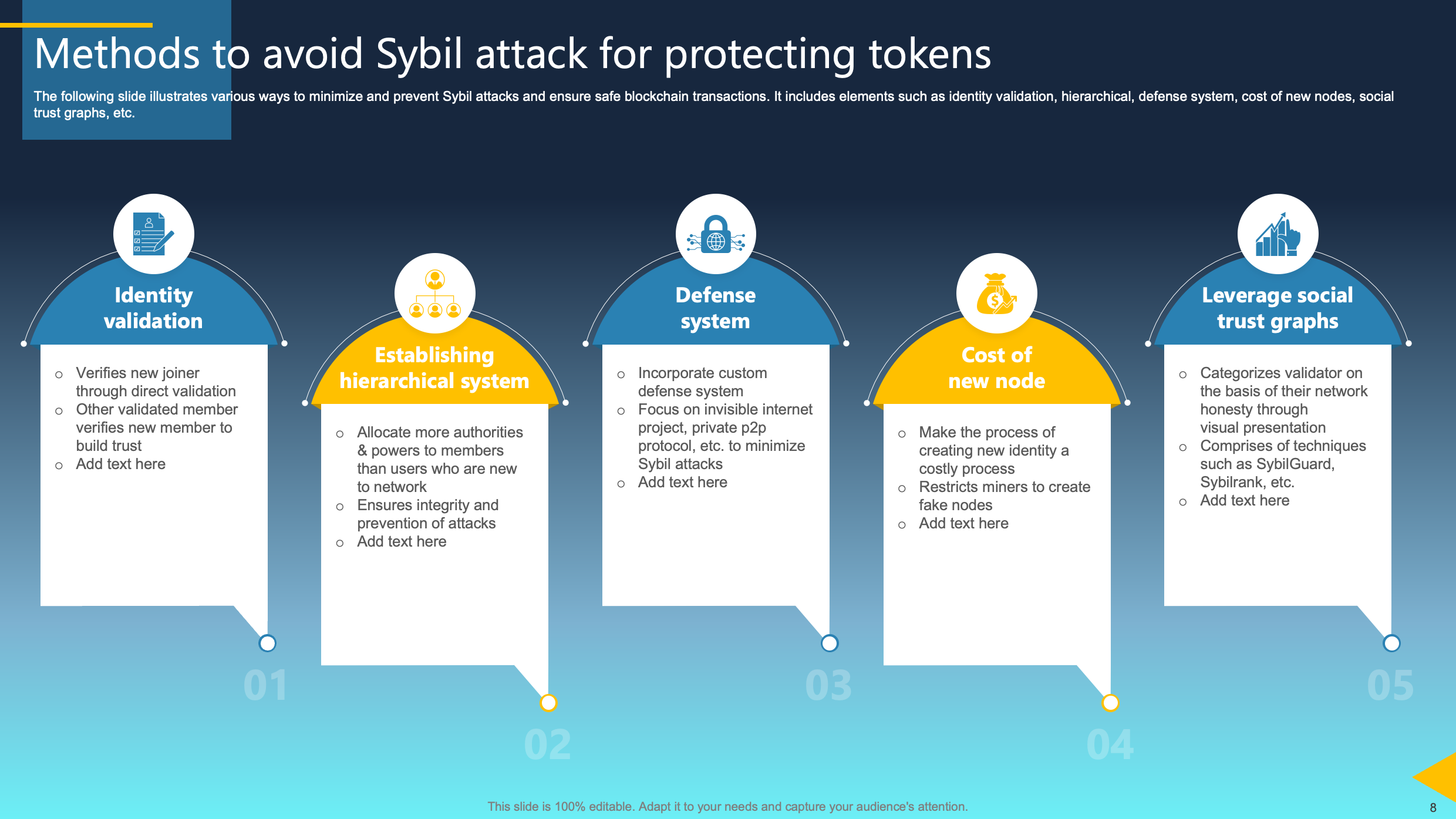
Methods to Avoid Sybil Attack for Protecting Tokens
This slide outlines diverse strategies to minimize and prevent Sybil attacks, promoting secure blockchain transactions. Key elements include the validation of identities, the implementation of hierarchical defense systems, consideration of the cost associated with introducing new nodes, and the utilization of social trust graphs.
Implementing these measures establishes a strong defense against Sybil attacks, safeguarding the integrity and safety of blockchain transactions. The focus on validating identities, employing hierarchical defenses, considering costs, and utilizing social trust graphs collectively strengthens the blockchain ecosystem. This, in turn, mitigates the risk of Sybil attacks and improves the overall security of the transactional environment.
Download this PowerPoint Template Now!
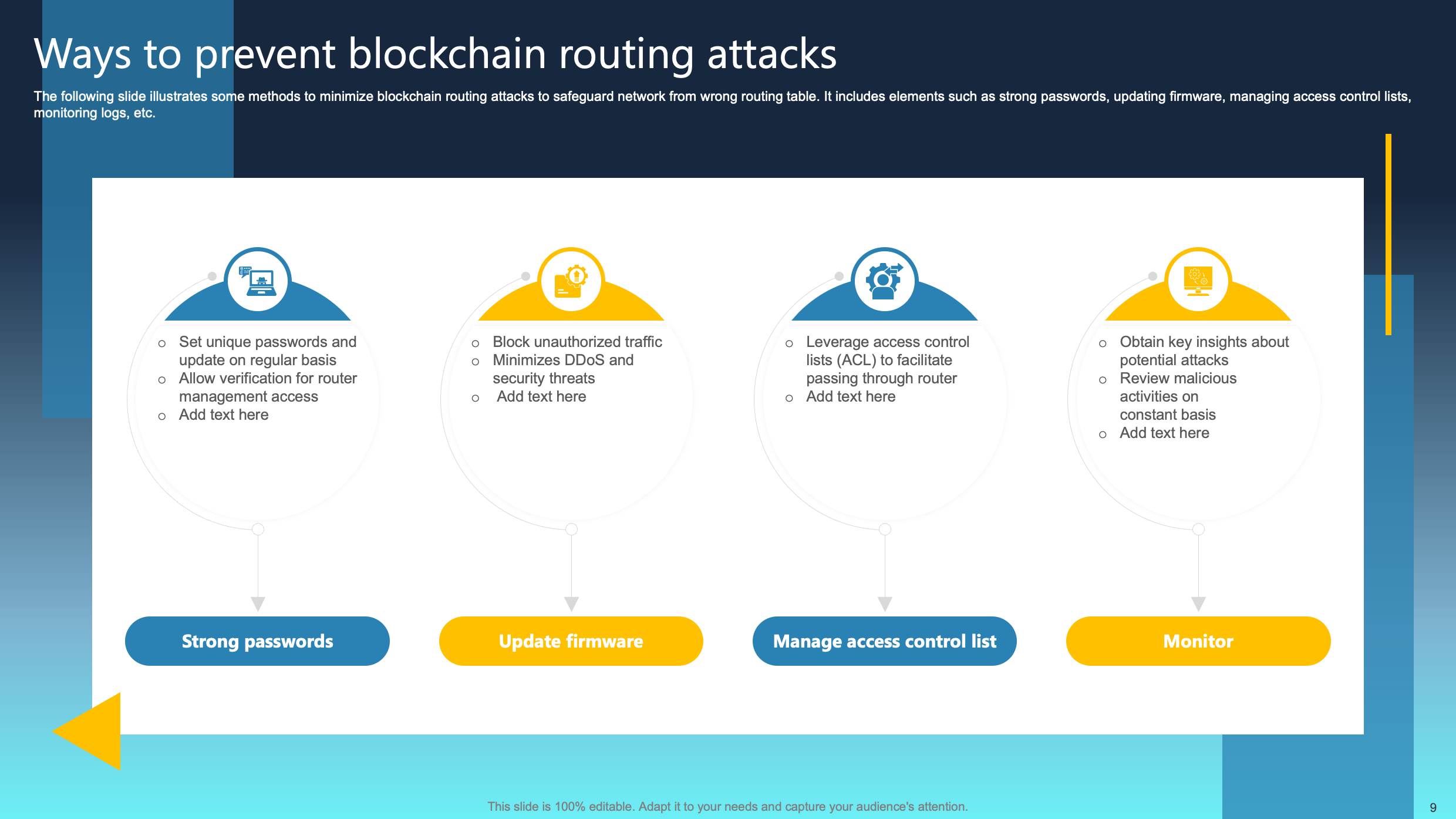
Ways to Prevent Blockchain Routing Attacks
This slide highlights effective methods for mitigating blockchain routing attacks and securing networks against incorrect routing table manipulation. Key elements involve the use of robust passwords, regular firmware updates, meticulous management of access control lists, and vigilant monitoring of system logs.
Implementing these measures empowers users to enhance their defenses, thereby minimizing the risk of unauthorized alterations to the routing table. Prioritizing strong passwords, regular firmware updates, meticulous access control, and continuous monitoring collectively strengthens the network infrastructure. This not only reduces vulnerability to routing attacks but also ensures the integrity and reliability of the blockchain system.
Download this PowerPoint Template Now!
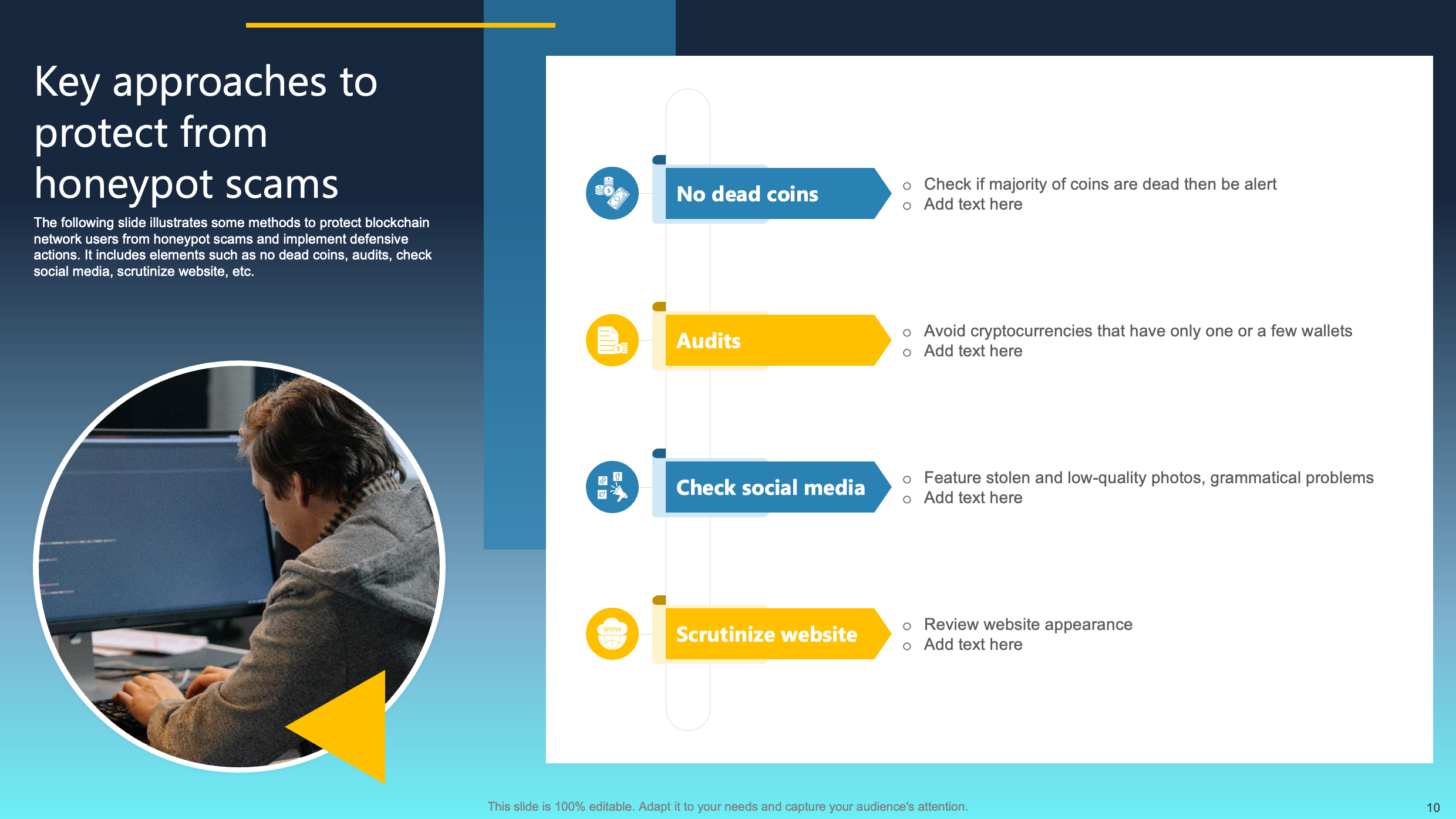
Key Approaches to Protect from Honeypot Scams
This slide outlines effective strategies to shield blockchain network users from honeypot scams, emphasizing proactive defensive actions. Key elements encompass avoiding dead coins, conducting audits, scrutinizing social media channels, and thorough examination of websites.
Incorporating these measures enables users to boost their protection against deceptive schemes. The focus on avoiding inactive or "dead" coins, conducting thorough audits, vigilantly scrutinizing social media platforms, and meticulously examining websites collectively strengthens defenses against honeypot scams. This fortification creates a more secure environment for users within the blockchain network, effectively mitigating the risks associated with fraudulent activities and enhancing overall resilience against potential threats.
Download this PowerPoint Template Now!
Best Practices for Protection Against Cyberattacks
In this section we’ll explore a few generic yet optimal approaches for defending against cyber threats. Uncover best practices to mitigate the risks involved in the ever-evolving landscape of cybersecurity.
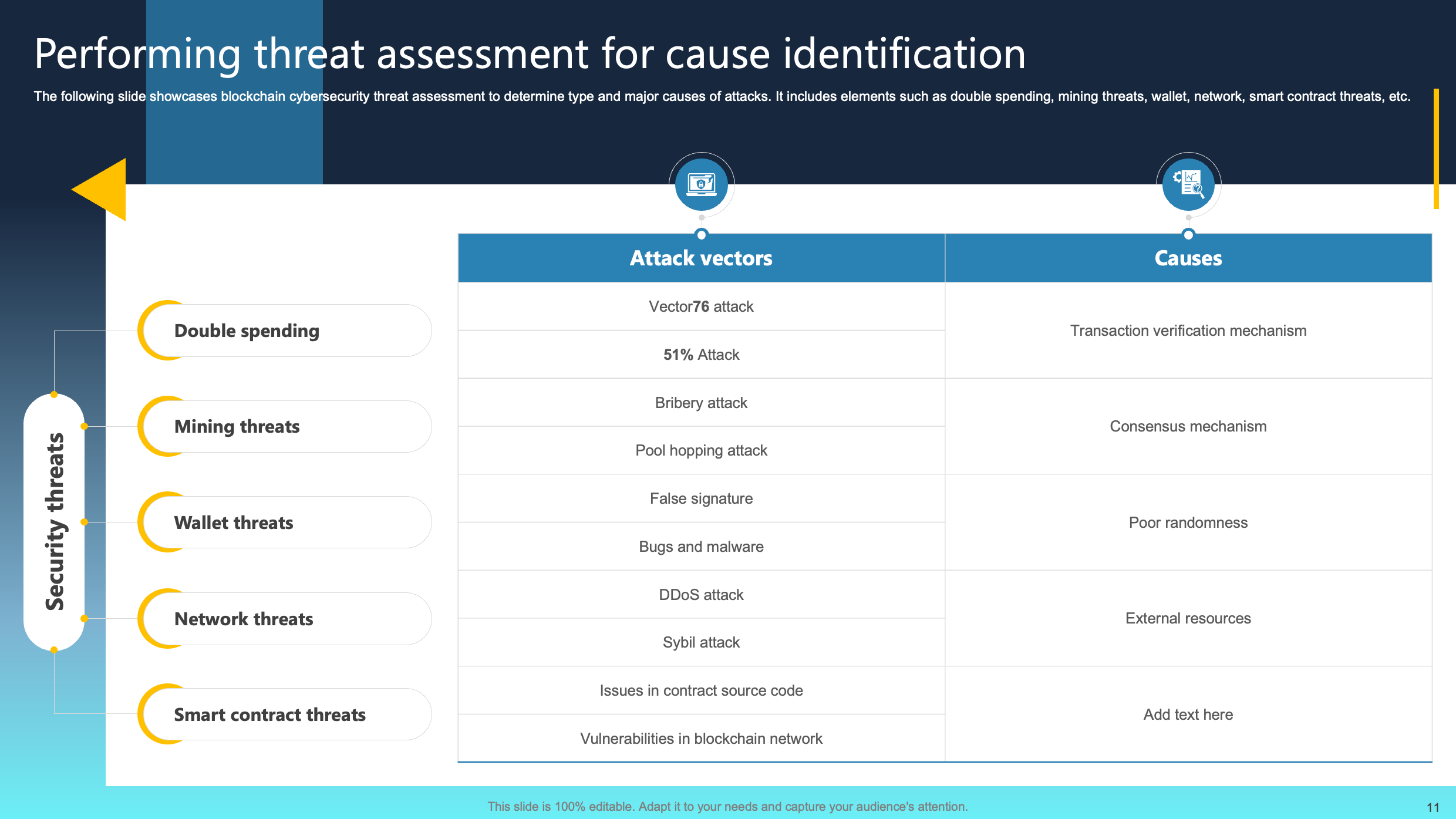
Performing Threat Assessment for Cause Identification
This slide presents a blockchain cybersecurity threat assessment aimed at identifying the types and primary causes of attacks. Key elements include evaluating risks associated with double spending, mining threats, wallet vulnerabilities, network compromises, and smart contract vulnerabilities.
Through this assessment, organizations can acquire insights into potential cybersecurity challenges within the blockchain ecosystem. It is crucial to focus on comprehending and categorizing threats associated with double spending, mining, wallets, networks, and smart contracts. This understanding is vital for implementing precise security measures and strengthening the resilience of blockchain technology against a variety of potential risks and attacks.
Download this PowerPoint Template Now!
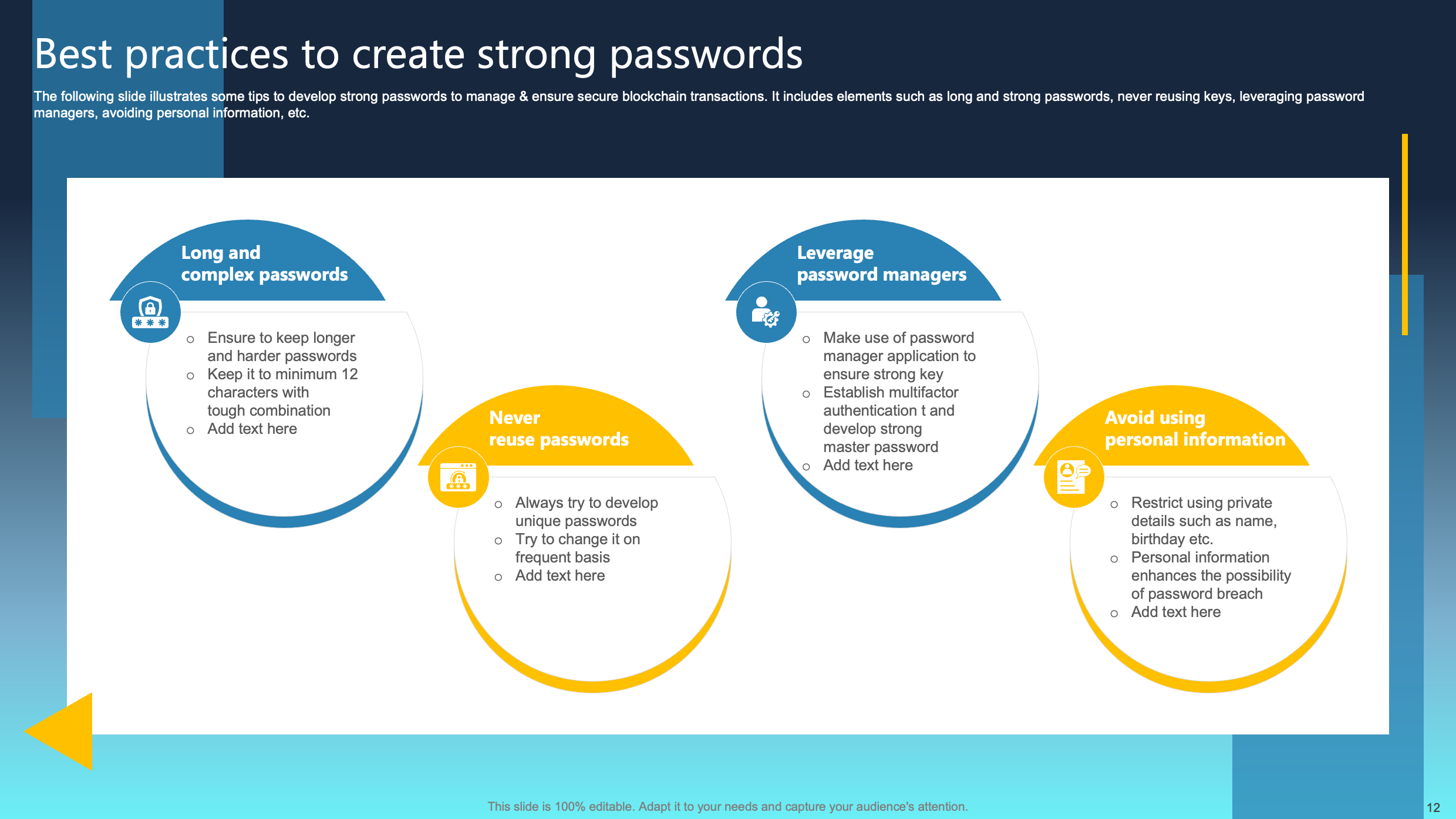
Best Practices to Create Strong Passwords
This slide outlines valuable tips for creating robust passwords to enhance the security of blockchain transactions. Key elements include the recommendation for crafting long and sturdy passwords, emphasizing the avoidance of key reuse, promoting the use of password management tools, and discouraging the inclusion of personal information.
Implementing these measures empowers users to strengthen their passwords, thereby diminishing the risk of unauthorized access to blockchain accounts. Prioritizing the use of long, unique passwords, abstaining from reuse, and employing password managers collectively contributes to creating a more secure transactional environment. This approach safeguards sensitive blockchain data from potential security threats, enhancing the overall protection of user accounts.
Download this PowerPoint Template Now!
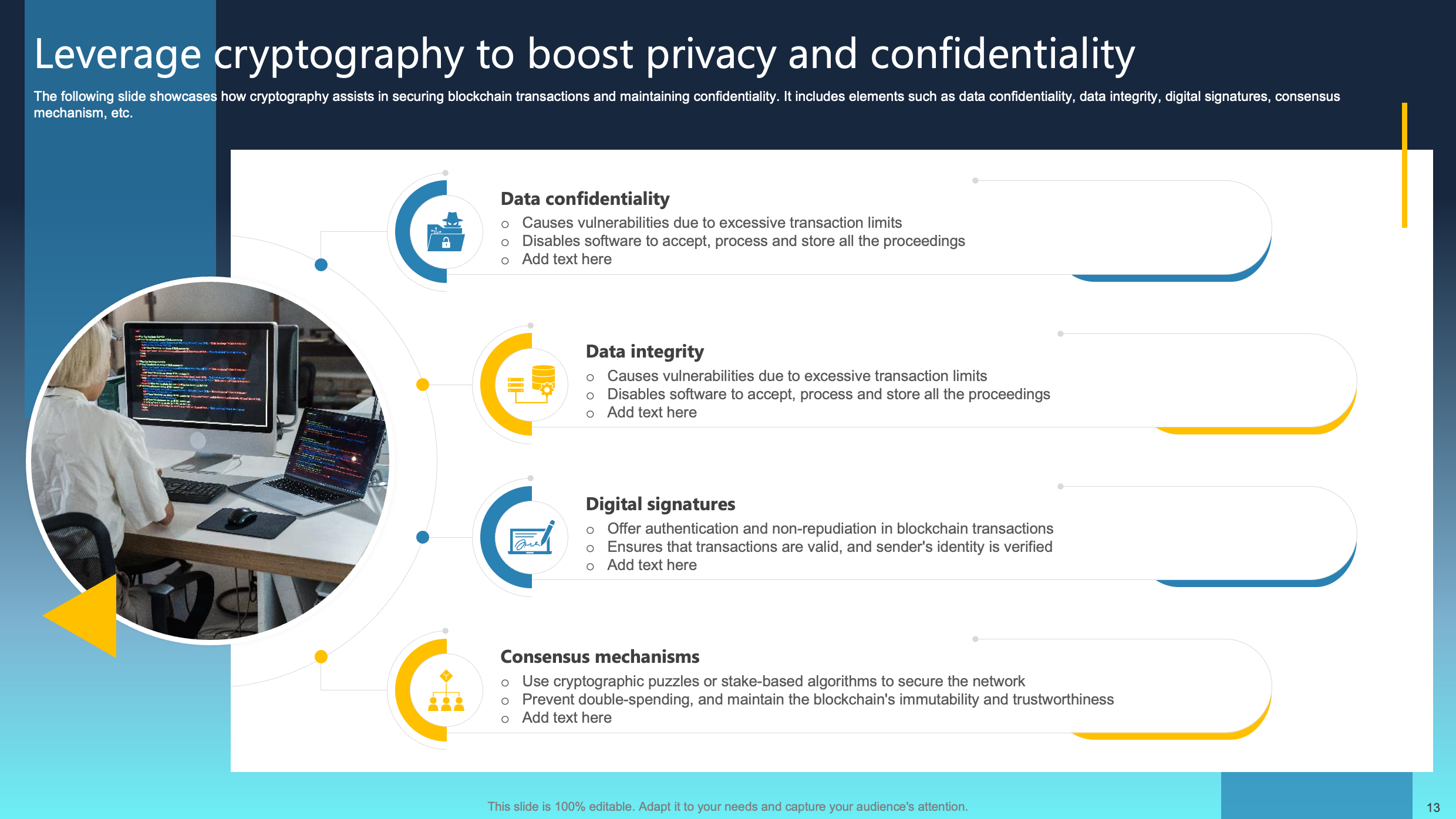
Leverage Cryptography to Boost Privacy and Confidentiality
This slide highlights the pivotal role of cryptography in securing and upholding the confidentiality of blockchain transactions. Key elements include ensuring data confidentiality, maintaining data integrity, employing digital signatures, and leveraging consensus mechanisms. Cryptography serves as the linchpin in safeguarding the blockchain ecosystem by securing sensitive information, validating the authenticity of transactions through digital signatures, and ensuring the consensus mechanism's reliability.
Prioritizing data confidentiality, integrity, and the utilization of cryptographic tools elevates the security of blockchain transactions. This approach establishes trust in the system and strengthens the foundations of confidentiality within the dynamic landscape of blockchain technology.
Download this PowerPoint Template Now!
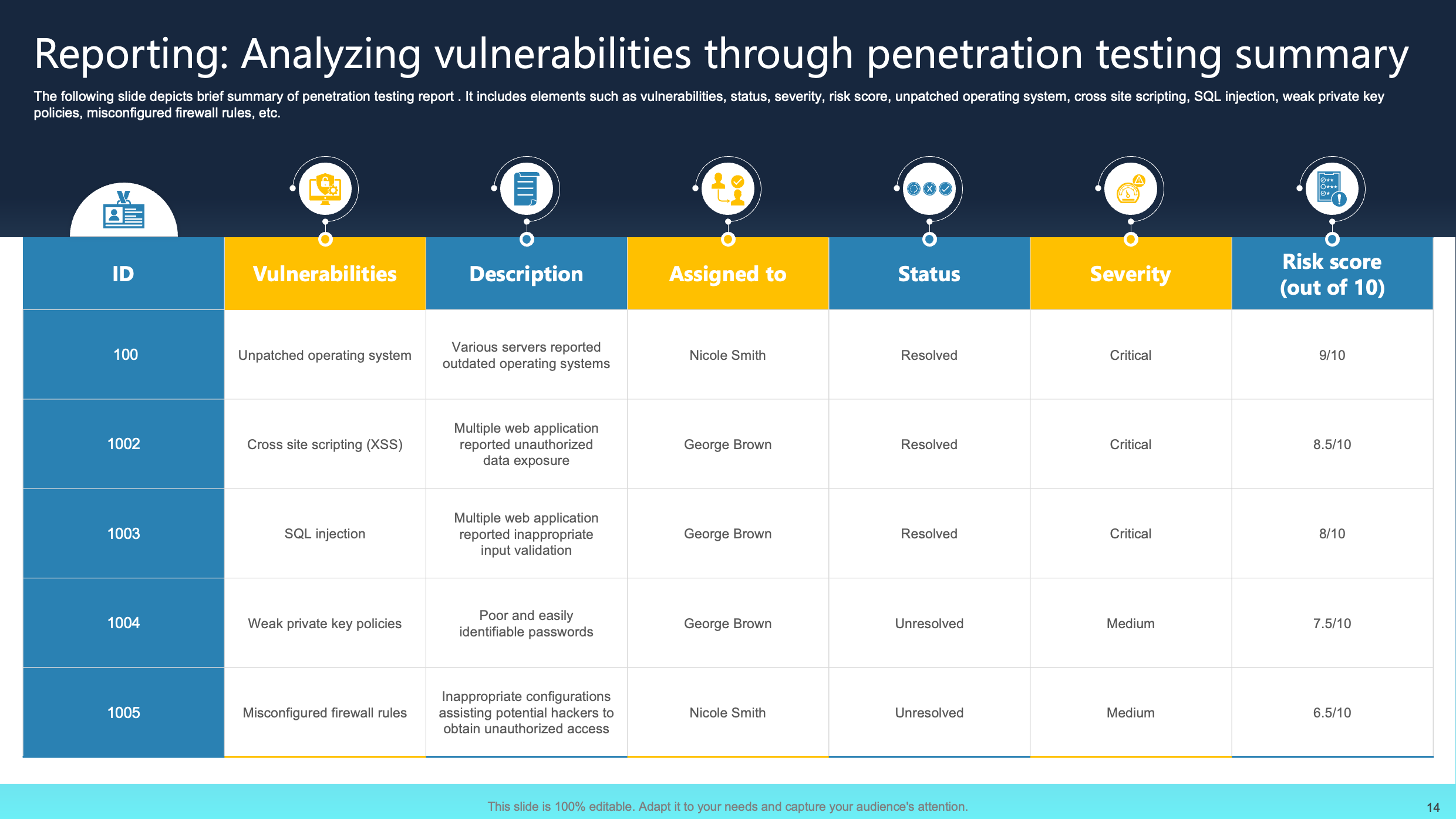
Reporting: Analyzing Vulnerabilities Through Penetration Testing Summary
This slide offers a concise overview of a penetration testing report, summarizing key aspects such as identified vulnerabilities, their current status, severity levels, risk scores, and specific issues like unpatched operating systems, cross-site scripting, SQL injection, and weak private key policies. The report sheds light on potential security gaps, emphasizing areas of concern such as misconfigured firewall rules.
Encapsulating these critical elements, the summary provides stakeholders with a comprehensive snapshot of the security posture. This allows a clear understanding of testing outcomes, enabling the prioritization of actions to fortify the system against various cyber threats and vulnerabilities.
Download this PowerPoint Template Now!
Conclusion
Navigating the transformative realm of blockchain requires a robust understanding of its cybersecurity landscape and adept risk management. This ultimate guide has illuminated key principles, emphasizing decentralization, consensus mechanisms, and the indispensable role of cryptography. As the adoption of blockchain technology surges, so too do the cybersecurity threats, underscoring the importance of proactive measures.
To further fortify your knowledge and empower your blockchain journey, we invite you to download the accompanying presentation. Dive deeper into the nuances of blockchain cybersecurity, explore effective risk management strategies, and equip yourself with the tools needed to safeguard this groundbreaking technology.
Don't miss out on the opportunity to secure your blockchain transactions and enhance your resilience against evolving threats. Click here to download the full presentation and embark on a journey towards a safer and more secure blockchain experience.
FAQs
Q1: What makes blockchain resilient against single points of failure?
A: Blockchain's decentralization, where each node in the network has a copy of the entire blockchain, minimizes the risk of single points of failure, enhancing its security.
Q2: How does cryptography contribute to blockchain security?
A: Cryptography, using public and private key pairs and advanced algorithms like SHA-256, secures transactions and ensures the integrity of data stored on the blockchain.
Q3: What preventive measures can users take to enhance protection against phishing attempts?
A: Users can strengthen their defense by using long and unique passwords, avoiding key reuse, and implementing two-factor authentication. These practices contribute to a more secure cryptocurrency experience.
Q4: How does blockchain technology mitigate the risk of Sybil attacks?
A: Blockchain mitigates Sybil attacks through measures like identity validation, hierarchical defenses, cost considerations, and utilizing social trust graphs, collectively fortifying the transactional environment.
Q5: What is the significance of continuous monitoring in blockchain routing security?
A: Continuous monitoring is crucial for maintaining the integrity and reliability of the blockchain system by reducing vulnerability to routing attacks and ensuring the effectiveness of security measures over time.
Related Products





 Customer Reviews
Customer Reviews