In a world where our lives are intertwined with technology, sensitive information floats across digital highways, and the boundaries between the physical and virtual realms are blurred. One thing stands as an unwavering sentinel against the forces of chaos and uncertainty: the security policy.
In today's digital world, safeguarding sensitive data is crucial for organizations. Therefore, security policy templates are essential for a robust cybersecurity strategy, serving as a blueprint for protecting assets. These templates encapsulate best practices, industry standards, and regulatory requirements, creating a secure environment for data, networks, and systems. They also instil a culture of security within an organization, communicating the importance of cybersecurity to the team. A well-crafted policy template empowers employees to be vigilant custodians of the digital realm, making preparedness the greatest asset.
Let's explore!!
Template 1: Security Policy and Implementation guidance
In an ever-evolving cyber landscape, this PowerPoint Presentation is your shield, offering comprehensive strategies, best practices, and step-by-step instructions to fortify your defences and protect your organization from threats. This is a premium PPT Template consisting of six stages: client and operation structure, training and presentation, information flow, aggregation control, department size vs. operation size, access control, and network infrastructure. Grab this PowerPoint Slide to safeguard your data.
Template 2: Roadmap of Cyber Security Asset Assessment and Security Policy Development
This dynamic guide paves the way to robust protection, ensuring your digital assets remain resilient. From pinpointing vulnerabilities to crafting ironclad policies, empower your defence strategy for the digital age! The PowerPoint Slide presents a roadmap for cyber security asset assessment and security policy development, outlining six stages of the process: assessment, build, selection, deployment, awareness, and audit. It is an easy-to-edit PowerPoint Template that can be downloaded immediately to highlight information on Audit, Awareness, Assessment, Build, and Deployment.
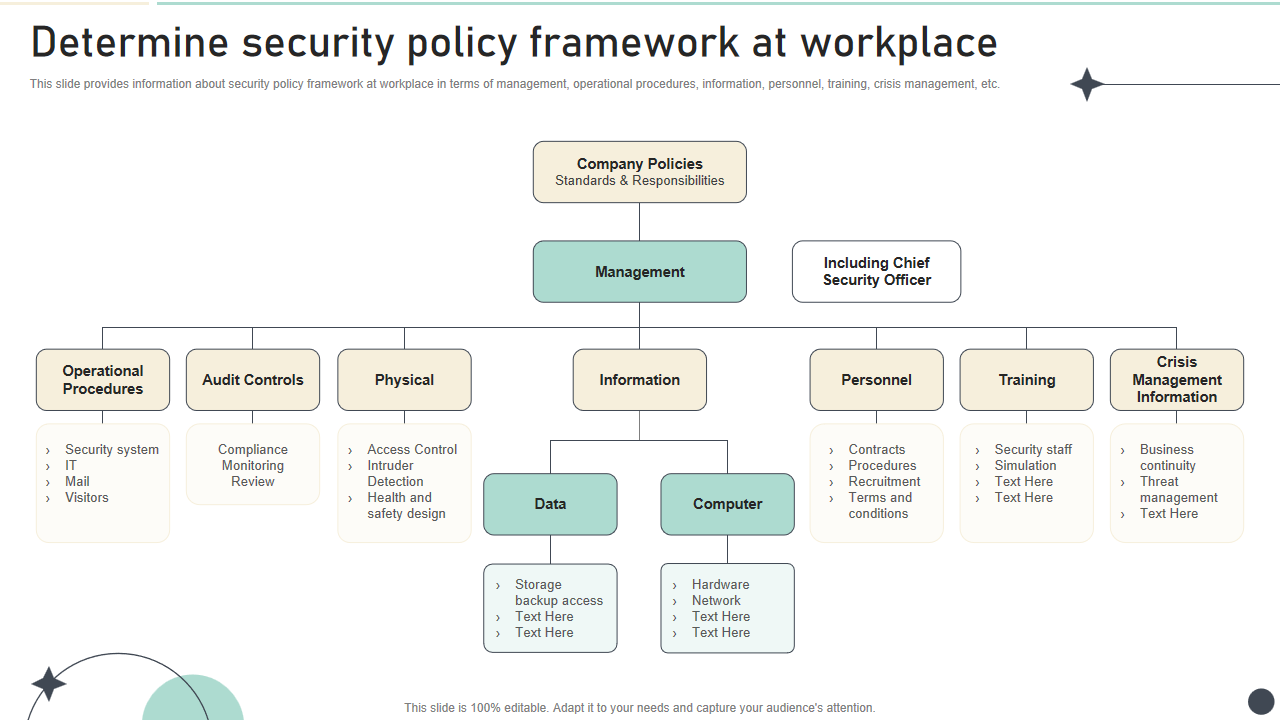
Template 3: Determine Security Policy Framework at the Workplace
Crafted for modern organizations, this toolkit is your compass in building a robust security policy framework. Safeguard your assets, empower your teams, and foster a secure work environment. This PowerPoint Presentation provides information on workplace security policy framework, including management, operational procedures, personnel, training, and crisis management. The Template can be used to deliver an outstanding presentation on company policies, management, and operational procedures.
Template 4: Information Technology Security Policy in Business Organization
This indispensable Presentation provides a blueprint for safeguarding your organization's digital assets. From data protection to network security, it's your roadmap to ensure the fortification of your IT infrastructure. This PowerPoint Slide outlines IT security policies that shape an organization's preparedness and response to security incidents. It includes acceptable use, access control, security training, incident response, and remote access policies. The premium set includes actionable Slides that can be used to present information on these policies.
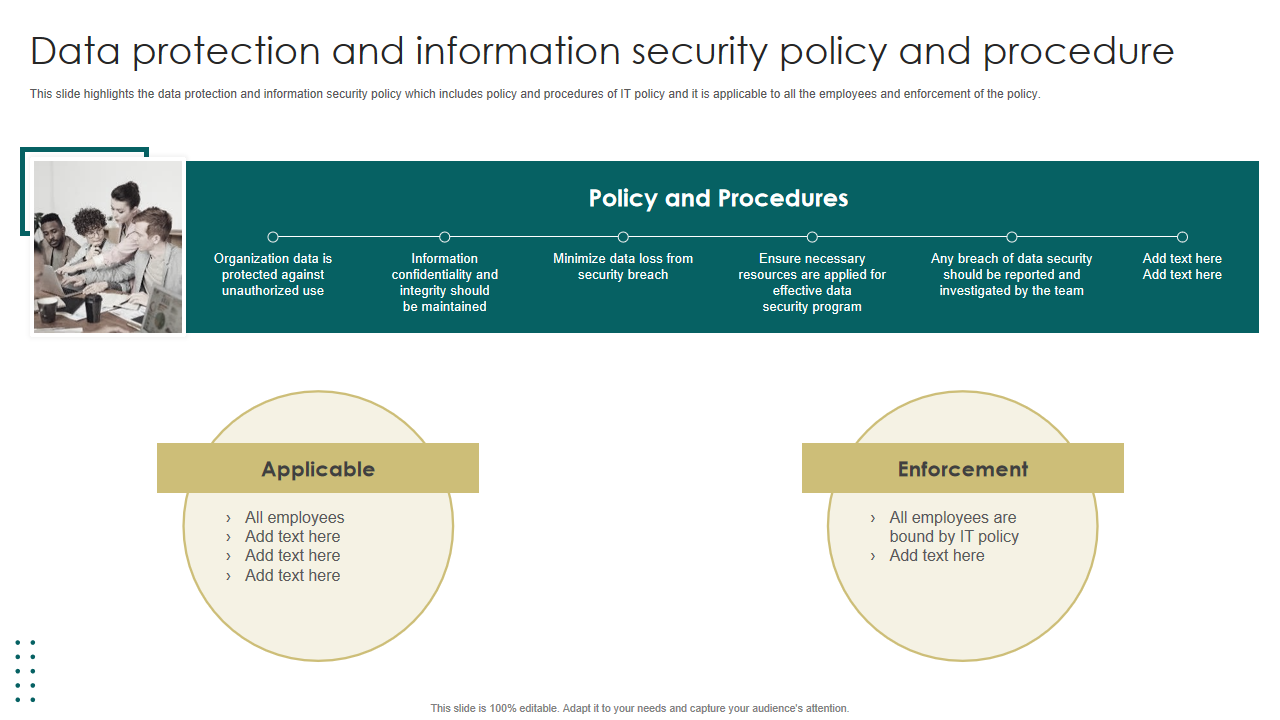
Template 5: Data Protection and Information Security Policy Template
Shielding your company's lifeblood - data - is non-negotiable. It is the cornerstone of your company's policies and procedures. This unwavering commitment to safeguarding information ensures trust, compliance, and resilience in today's data-driven world. This Template provides an overview of IT security policies that influence an organization's preparedness and response to security incidents, including acceptable use, access control, security training, incident response, and remote access policies.
Template 6: Business Security Policy and Program Implementation
In an era where data is gold, this comprehensive toolkit protects against threats. Navigate the complex world of cybersecurity confidently and ensure your business thrives in a secure environment. Grab this pre-designed PowerPoint Slide focusing on policy program, implementation, and business impact. Download now to captivate your audience and effectively implement security measures.
Template 7: Network Security Policy to Secure Business Data
In an age where data is the lifeblood of business, this blueprint fortifies your defences. Guard against cyber threats, ensure data integrity and empower your business to thrive securely. This is a top-notch PowerPoint Template that you can use as a comprehensive guide on protecting organizations' data by company laws and industry standards. It covers internet access, VPN, firewall rules, wireless LAN, and remote connection.
Template 8: Systems Access Control Security Policy Template
In the age of cyber threats, a well-defined security policy is your master key. Safeguard sensitive data, streamline access, and fortify your organization's defences. Empower your team to navigate the digital world securely, one access point at a time! This is a flexible PPT Layout for a firm's computer systems and laptops, focusing on business data security. It covers policy risks, key points, and information standards. The PowerPoint presentation is customizable and available for download, allowing the audience to understand and comply with the policy.
The Fabric of the Security Posture
In the ever-evolving cybersecurity landscape, a security policy template isn't just a document; it's a guiding star that helps organizations navigate the treacherous waters of the digital age. As we conclude our journey through security policy templates, remember, they are the keys to your organization's resilience, the guardians of trust, and the architects of a secure future.
So, whether you're a startup aiming to safeguard your dreams or a corporate giant protecting your legacy, remember that security policy templates are your allies in the battle for digital survival. Embrace them, adapt them, and fortify your digital fortress, for in the ever-shifting landscape of cybersecurity, these templates are your steadfast companions on the path to victory.
Our security policy templates serve as your steadfast allies in safeguarding what matters most. You have the blueprint to protect your assets, organization, and future with them.
FAQs on Security Policy
What are the five key elements of a security policy?
A security policy is a critical document that guides an organization's approach to safeguarding its information and assets. The five critical elements of a security policy are:
- Purpose and Scope: The policy should clearly outline its objectives, coverage scope, assets, systems, and personnel and provide a rationale for its existence.
- Roles and Responsibilities: The document outlines the roles and responsibilities of security officers, administrators, and employees, outlining their duties and responsibilities.
- Security Controls: Implementing security measures such as access controls, encryption protocols, network security, and incident response procedures is crucial to ensure compliance with industry best practices and regulations.
- Risk Management: The process involves identifying, assessing, and managing risks through regular risk assessments, vulnerability assessments, and incident reporting and handling procedures.
- Compliance and Enforcement: Implement monitoring and enforcement mechanisms for policy compliance, outlining consequences for non-compliance, reporting policy violations, and outlining the consequences for security protocol failures.
These elements collectively ensure an organization's structured and comprehensive approach to information security.
Why is security policy important?
A security policy is of paramount importance for several reasons:
- Risk Mitigation: It serves as a roadmap for identifying, assessing, and mitigating security risks within an organization.
- Compliance: Security policies ensure that an organization adheres to legal and regulatory requirements, protecting it from penalties and reputational damage.
- Consistency: Consistency ensures that security measures are uniformly applied, reducing the likelihood of oversight or gaps in protection.
- Incident Response: They provide a framework for responding to security incidents and breaches, enabling a swift and organized reaction when threats occur and minimizing damage and downtime.
- Risk Communication: Security policies facilitate communication about security practices and expectations throughout the organization to create employee awareness.
- Trust and Reputation: Organizations that demonstrate a commitment to security through robust policies can earn trust from customers, partners, and investors, enhancing their reputation and competitiveness.
- Strategic Planning: Security policies align security practices with an organization's strategic goals, ensuring security measures support its mission and objectives.
What are the principles of security policy?
Several fundamental principles guide security policies:
- Confidentiality: Protect sensitive information from unauthorized access, ensuring only authorized personnel can be viewed or modified.
- Integrity: Ensure data and systems are accurate, complete, and unaltered by unauthorized entities or malware.
- Availability: Ensure that information and systems are accessible and functional when needed, minimizing downtime.
- Authentication and Authorization: Verify the identity of users and grant access based on their roles and responsibilities.
- Accountability: Establish clear responsibilities for security, ensuring individuals and teams are accountable for safeguarding assets.
- Least Privilege: Limit access to the minimum necessary for tasks, reducing the potential for misuse.
- Auditing and Monitoring: Monitor systems and activities to detect and respond to security incidents.
- Compliance: Align security practices with relevant laws, regulations, and industry standards.
- Education and Training: Educate employees about security risks and best practices to promote a security-aware culture.
- Incident Response: Develop procedures to address security incidents promptly and effectively, minimizing damage and recovery time.





 Customer Reviews
Customer Reviews