"If you spend more on coffee than on IT security, you will be hacked.”
-Richard Clarke, American National Security Expert
In the ever-evolving landscape of IT security, the wisdom of Richard Clarke rings true. When it comes to cyber-security, systematic planning isn't just a good practice; it's an absolute necessity. As the digital world continues to advance, so do the threats that it faces. To safeguard your organization's sensitive information and digital assets, you need a well-defined IT security policy.
In today's interconnected world, where the flow of information transcends physical boundaries and cyber-criminals are more adept than ever, a proactive approach to IT security is paramount. Whether you're a seasoned IT professional looking to update your organization's security policies or a business leader aiming to fortify your company's digital defenses, our curated IT Security Policy Templates will serve as invaluable resources.
Also, when it comes to securing your organization's emails and enhancing cybersecurity awareness, our blog on must-have Email Security Industry Report Templates offers valuable resources.
They not only save you time and effort but also ensure that your organization is equipped with the latest best practices and compliance standards, enabling you to navigate the ever-changing cybersecurity landscape with confidence. In the sections that follow, we will delve into each of these must-have IT security policy templates, providing you with samples and examples that offer clarity on their purpose and implementation. These are all highly adaptable PowerPoint template designs, readily customizable to suit your precise needs.
Template 1: Elucidating the Agenda Cyber Security Template
In this template, we delve into the significance of IT policy, the importance of cybersecurity policy, and the checklist necessary for creating an effective IT policy. We will also explore different policies, including BYOD policy, security awareness, and managing IT assets. Additionally, we'll discuss the various policies' associated costs and the role of a training program in enhancing security awareness. Download this valuable resource to fortify your company's information technology defense.
Download Now to Fortify Your Defense!
Template 2: Exploring the Cyber Security Policy Template
This presentation provides an overview of various policies, including remote access policies for employees, password creation and management policies, data retention policies, acceptable use of equipment policy, information system change management policy, and incident response policy. We will emphasize the importance of IT policies and procedures and discuss the consequences that may arise in the absence of well-defined policies.
Get Informed and Secure Your Organization!
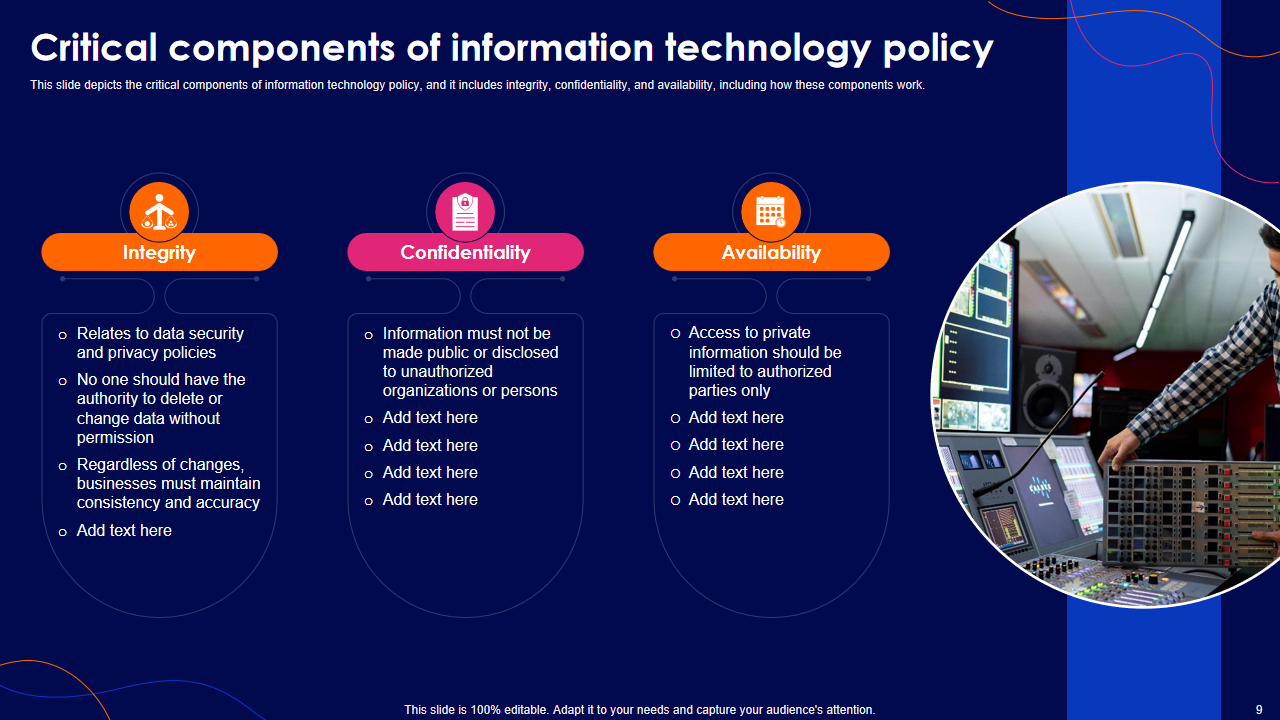
Template 3: Getting Into the Critical Components of Information Technology Policy Template
Dive into this PPT Template that focuses on the essential components of information technology policy, including integrity, confidentiality, and availability. Learn how these components are crucial for data security and privacy policies. We will stress the importance of controlling data alterations and limiting access to authorized personnel. Download now to gain insights into ensuring the security of your IT assets.
Enhance Your Security Knowledge! Download Now!
Template 4: Understanding the Checklist for writing an effective IT policy Template
This illustration describes the checklist for crafting a robust information technology policy. It includes best practices such as conducting a security risk assessment, identifying essential assets, defining policy coverage, documenting policies for clarity, and educating employees about policy compliance. Download and discover how these steps contribute to the creation of clear and effective IT policies.
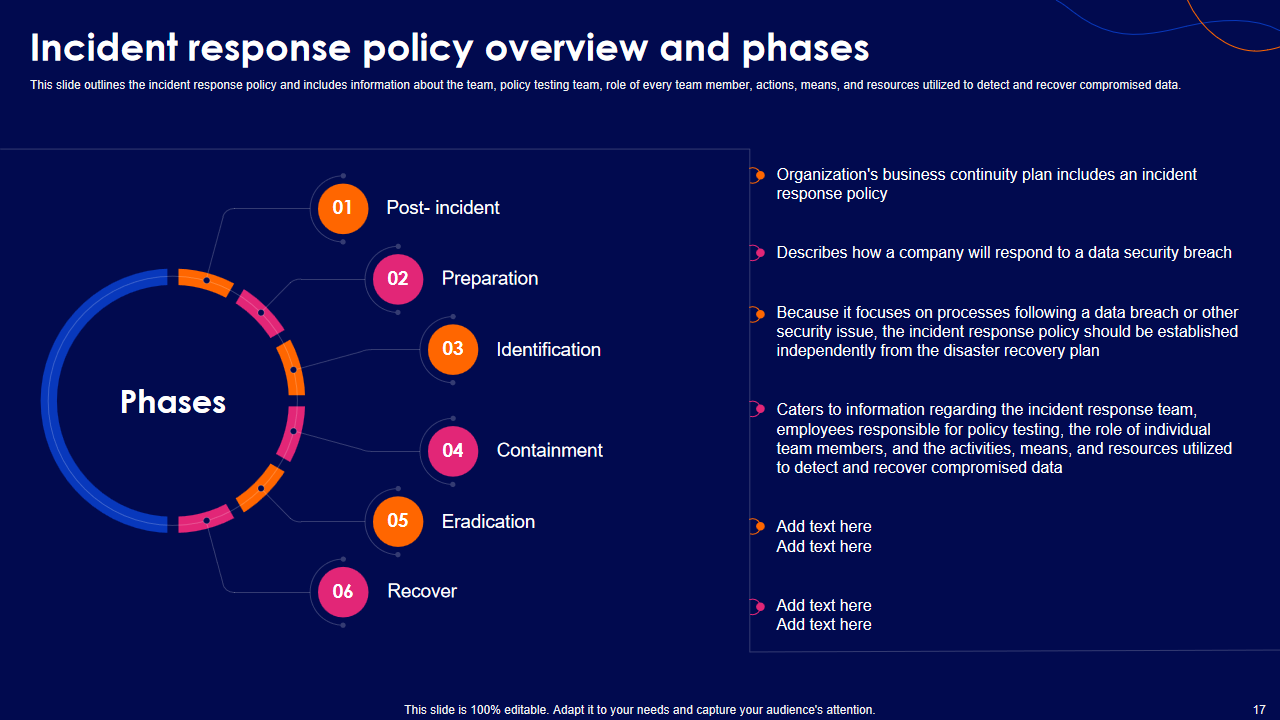
Template 5: Presenting the Incident Response Policy Overview Template
This slide outlines the incident response policy, including information about the incident response team, policy testing procedures, and the roles of team members. Gain an understanding of the actions, means, and resources utilized to detect and recover compromised data. Learn why it's essential to have an incident response policy separate from the disaster recovery plan. Dive into the phases of incident response, including post-incident, preparation, identification, containment, eradication, and recovery.
Prepare for Incident Response! Download Here!
Template 6: Explaining the Software Usage Policy Objective and General Guidelines Template
Here, we provide a detailed look at the usage policy. Learn about the policy's objectives and general guidelines, including compliance requirements. We cover both paid and free software, emphasizing the purpose of proper installation, use, and maintenance on company-owned computers. Understand preloaded software, IT department authorization, and the strict prohibition of pirated software. Discover the importance of adhering to software licensing agreements with a download.
Secure Your Software Usage! Download Now!
Template 7: Unraveling the Termination of Employment and Violation of BYOD policy Template
This illustration emphasizes the procedures concerning employee termination and violations of our BYOD policy. We outline the actions to be taken when an employee leaves the company or breaches the BYOD policy. Understand the requirement for employees to present personal devices for inspection upon termination, with a focus on the deletion of business data. We also emphasize the need for written authorization for BYOD usage and potential disciplinary actions for non-compliance with corporate policies.
Stay Compliant and Download Now!
Template 8: Detailing the Internet Usage Policy Objective and General Guidelines Template
In this template, discover the criteria for authorized use of the organization's internet network to enhance productivity while ensuring data security and employee safety. Learn about employee login guidelines and tools available for tracking and recording internet activity, ensuring a secure internet network.
Enhance Internet Usage Security! Download Now!
Template 9: Delving into the Internet Usage Policy - Password Guidelines Template
This slide covers three categories: selecting a strong password, keeping passwords secure, and implementing other security measures. Understand the importance of choosing passwords without easily recognizable terms, safeguarding passwords, and employing security measures to protect against unauthorized access. Dive into best practices for maintaining password integrity while accessing the internet.
Boost Password Security! Download Now!
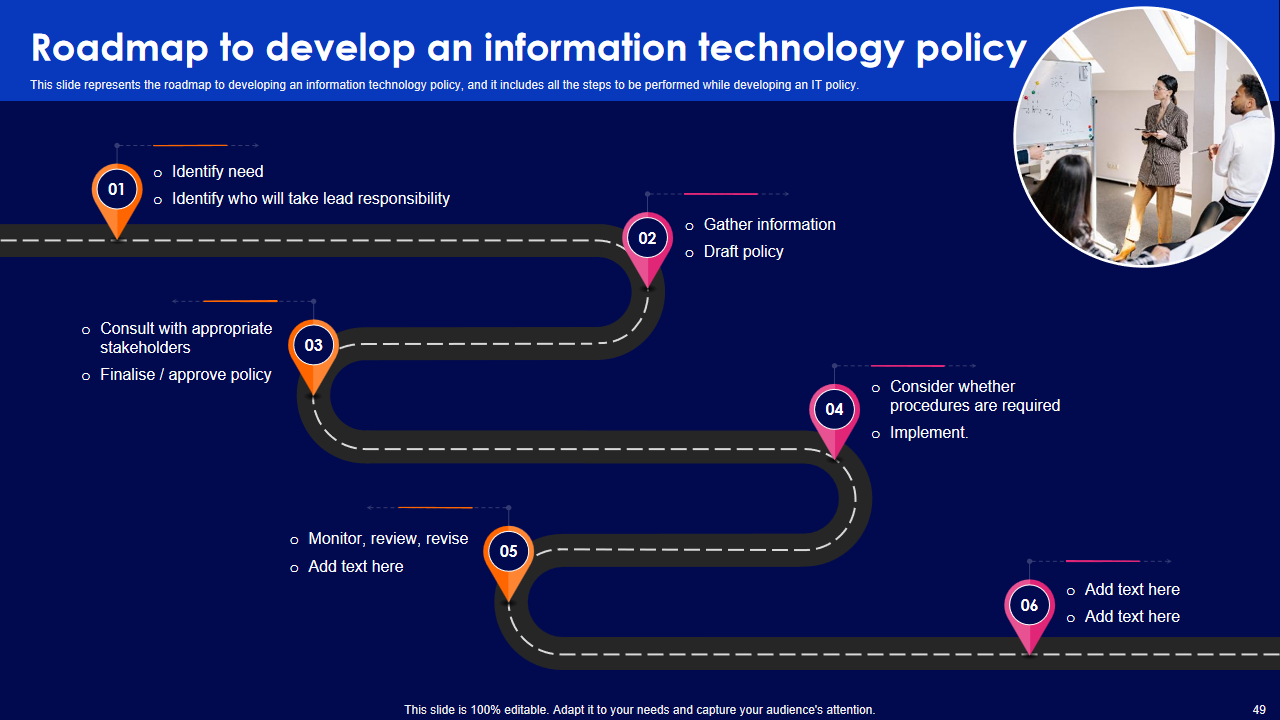
Template 10: Presenting the Roadmap to Develop an Information Technology Policy Template
In this slide, we outline all the necessary steps, including identifying needs, designating responsibility, gathering information, drafting policies, consulting stakeholders, finalizing and approving policies, and considering the need for accompanying procedures. Understand the importance of implementing, monitoring, reviewing, and revising policies to ensure ongoing effectiveness in safeguarding your organization's IT assets.
Start Your Policy Development Journey! Download Now!
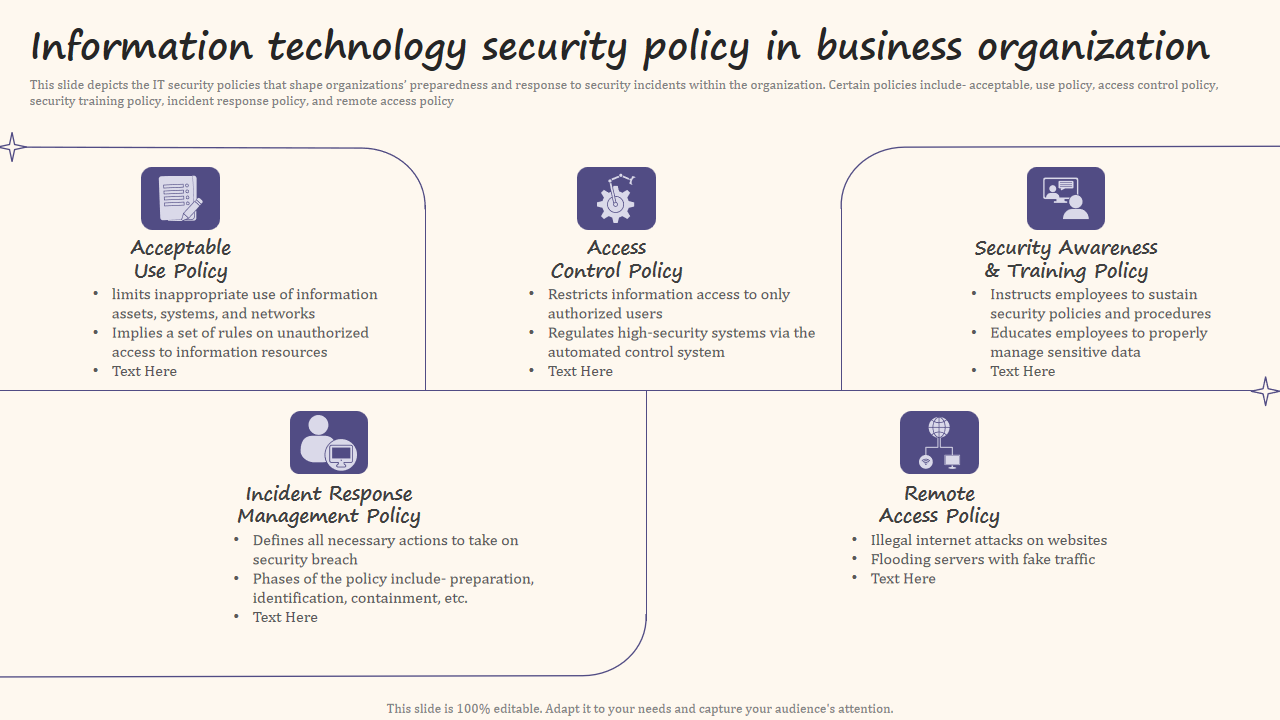
Template 11: Revealing the Information Technology Security Policy in Business Organization Presentation
This PPT Slide visually encapsulates the IT security policies that demonstrate an organization's readiness and response to security incidents. Notable policies encompass the acceptable use policy, access control policy, security awareness training policy, incident response policy, and remote access policy. Our premium slide set offers a versatile platform to elucidate these policies and their pivotal roles. This is an efficient PowerPoint template design that can be used to interpret topics like Acceptable Use Policy, Access Control Policy, Remote Access Policy, and more. So, download instantly and level up with these slides.
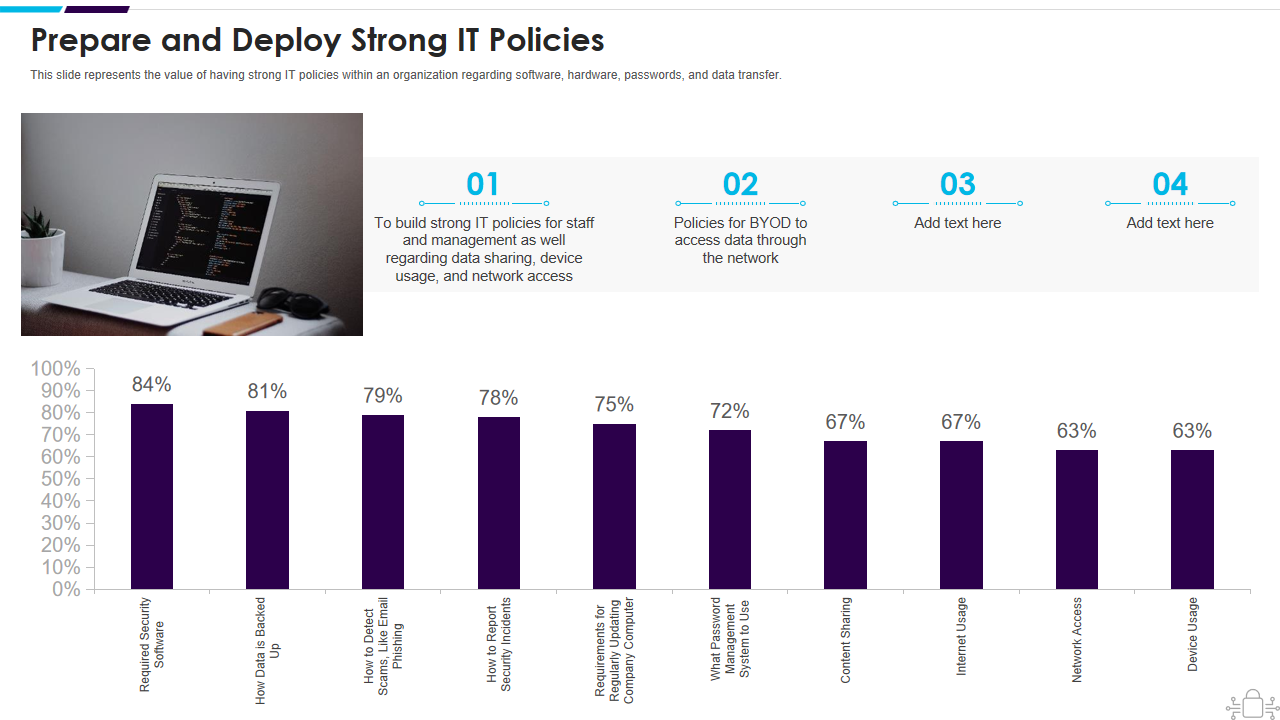
Template 12: Presenting the Information Technology Security Prepare and Deploy Strong IT Policies Deck
This PPT Deck underscores the importance of robust IT policies within an organization, encompassing software, hardware, password management, and data transfer. Employ our Presentation to deliver a compelling discourse on the subject. This template empowers you to dispense information comprehensively, providing a detailed explanation of preparing and deploying strong IT policies. Instant download is available, so grab it now to safeguard your organization's IT assets and promote security awareness.
Transform Your IT Policies Today
Conclusion:
In the world of IT security, it's crucial to emphasize the significance of well-structured and current policies. As Richard Clarke astutely reminds us, overlooking IT security can lead to severe consequences. In today's digitally interconnected environment, where cyber threats continuously evolve, a clear IT security policy is not just helpful but an absolute necessity.
In this era of heightened cybercriminal sophistication, proactive IT security is essential. These templates not only save time but also ensure your organization adheres to current best practices and compliance standards, enabling you to navigate the ever-changing cybersecurity landscape confidently.
These policies cover various critical areas, from password management and Bring Your Own Device (BYOD) guidelines to data protection and cybersecurity education. Make the most of these resources to safeguard your IT assets, enhance security awareness, and remain resilient in the face of evolving digital challenges.
For an in-depth understanding of IT Policy and Cyber Security Policy, you can explore our informative blog on must-have Information Security Scorecard Templates.
To develop a comprehensive strategy for safeguarding your IT assets, consider exploring our blog on the top 10 Information Security Roadmap Templates.
FAQs on IT Security Policy
1) What should be included in IT security policy?
In an IT security policy, several crucial components should be incorporated to ensure comprehensive protection of an organization's IT assets and promote security awareness. These components typically encompass guidelines for the establishment and management of strong passwords, rules for accessing and using cybersecurity resources, procedures for safeguarding sensitive information, and protocols for addressing security incidents. Additionally, the policy should outline the organization's stance on BYOD policy, emphasizing acceptable usage and security measures, and provide a clear framework for adhering to cybersecurity awareness training programs.
2) What are the three types of security policies?
The three primary types of security policies that organizations commonly implement are:
a) IT Policy: This encompasses the overarching set of rules and guidelines that govern the use of information technology within an organization. It covers various aspects, including IT security, BYOD policy, and more.
b) Cyber Security Policy: This policy focuses specifically on safeguarding an organization's digital assets and information from cyber threats. It includes measures for cybersecurity awareness, password management, network security, and data protection.
c) BYOD Policy (Bring Your Own Device Policy): This policy addresses the use of personal devices, such as smartphones and laptops, within the workplace. It outlines rules for securing these devices, accessing company resources, and protecting sensitive data.
3) What are the 3 key concepts of IT security?
Three fundamental concepts underpin IT security:
a) Confidentiality: This concept pertains to the protection of sensitive information from unauthorized access or disclosure. Ensuring that only authorized individuals can access confidential data is crucial for IT security.
b) Integrity: Integrity involves maintaining the accuracy and reliability of data. It ensures that data is not tampered with or altered by unauthorized individuals or malicious software.
c) Availability: Availability focuses on ensuring that IT systems and resources are accessible and operational when needed. Downtime or unavailability can disrupt operations and lead to security vulnerabilities.
4) What are the 5 aspects of IT security?
Five key aspects of IT security include:
a) Cybersecurity Awareness: Educating employees about cybersecurity risks and best practices is essential for preventing security breaches.
b) IT Policy: Having comprehensive IT policies in place, including cybersecurity policy and BYOD policy, to guide and regulate the use of technology resources.
c) Cyber Security Policy: A dedicated policy that outlines security measures and protocols to protect digital assets and information.
d) BYOD Policy (Bring Your Own Device Policy): A policy addressing the use of personal devices in the workplace, including rules for securing them and accessing company resources.
e) Protection of IT Assets: Implementing measures to safeguard IT assets, including hardware, software, and data, from unauthorized access, damage, or theft.




 Customer Reviews
Customer Reviews