Incorporate the use of a system security plan and protect your business from system harm waiting to take a toll on your essential data.
A system security plan is a strategy that offers the best way for you to safeguard and secure the data on your computer while demonstrating a systematic approach and techniques to prevent unauthorized users from using or abusing it, guard against worms and viruses, and protect against any incidents or events that could endanger the underlying system security.
When a company doesn't have a system security plan (SSP) or neglects to put proper system security in place, it could suffer from several drawbacks that could seriously affect its operations, reputation, and financial position. In addition to assisting with risk mitigation, it promotes compliance, establishes a security culture, and assures effective resource management. Given the constantly changing threat landscape, an SSP is crucial to contemporary corporate operations.
Introducing the IT security risk management plan. Click here to learn more.
We at SlideTeam strive to give shape and structure to the development and importance of system security as a tool to be included in the corporate working environment in order to establish the culture and adoption of system security in daily and business life. These templates were carefully crafted by our skilled team of template designers to best meet the demands of each organization. Our templates' complete editability and adaptability are our standout feature.
Uncertain about where to begin with information security? With our most recent roadmaps for improved application of security practises and policies, we have got you covered. Click here!
Protect your data and other essential information with the help of these PPT templates. Click here to learn more!
What are you waiting for? Download them, to begin with your system security plan.
Template 1 – Information system security and Risk administration plan PowerPoint presentation slides
Create an effective system security plan while appropriately managing the risk management functions with this PPT Deck. Describe the agenda regarding the information on system security, determine the current information, prioritize the information assets, all the while monitoring the risk. Device an effective administration plan for proper functioning and formulation and deliver an overview of information security. Utilize this template to learn and present on cyber-attacks faced by different departments while distinguishing based on the number and types of attacks. Recognize the gap assessment for better comprehension of the information system security-related branches. This presentation goes over several cybersecurity dangers that businesses encounter globally and how those risks are managed. An information security risk management plan, which may be used to identify assets at risk from information security hazards, is covered in some detail in the presentation. Additionally covered is the evaluation of information security threats using a matrix for risk assessment and vulnerability rating. Additionally, it displays tactics to prevent data breaches and mitigation plans that can assist organizations in quickly resolving information security problems.
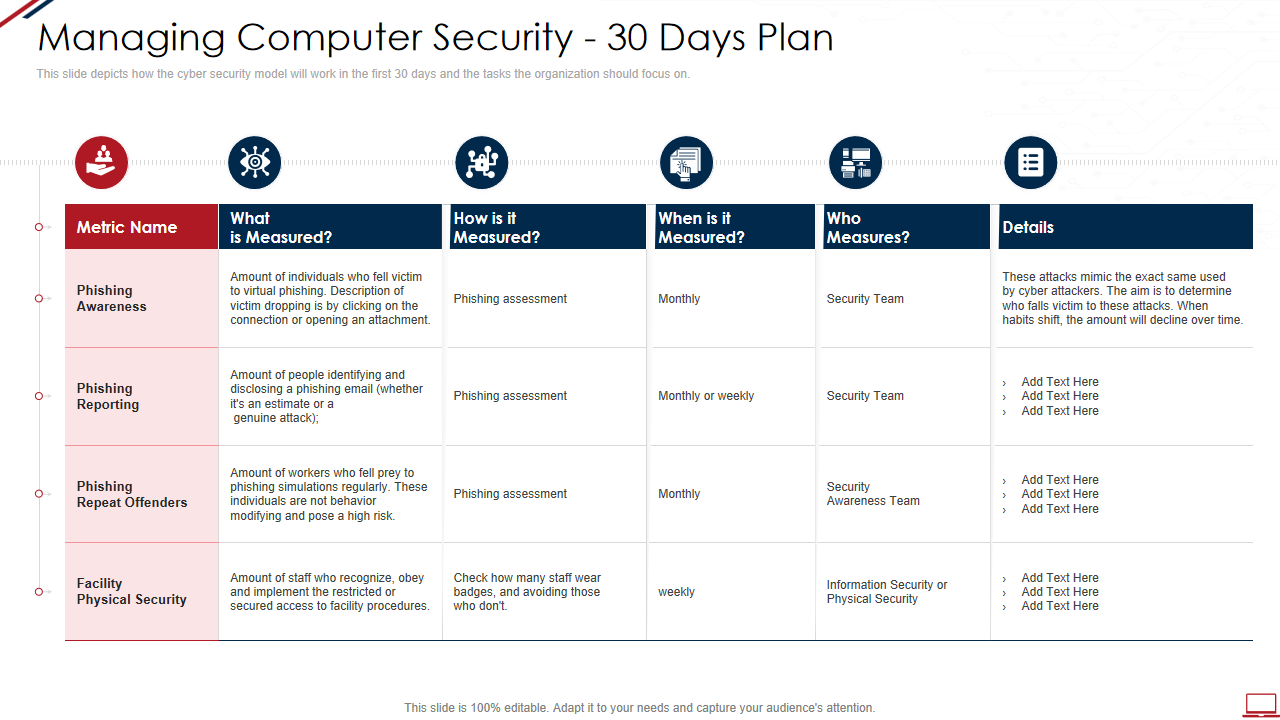
Template 2 – Managing Computer Security 30 Days Plan Computer System Security
Most modern organizations depend on computers, yet this necessity also carries risks. Computer security is a top concern for any organization because protecting corporate data is crucial. Since sensitive data is frequently valuable, thieves and hackers target computer systems. Protect your computer with this well-designed computer security plan template that enables you to shield your important computer data from getting involved in security breach activities. Furthermore, to effectively gauge the security plan, this template calls for phishing reporting where you cram about phishing awareness and phishing reporting while undertaking the details. With the help of this template, you can discover, evaluate, and manage potential risks in a step-by-step fashion. It has parts that define threat, vulnerability, repercussions, risks, remedies, and the categories—high, moderate, low, and critical—in which they fit.
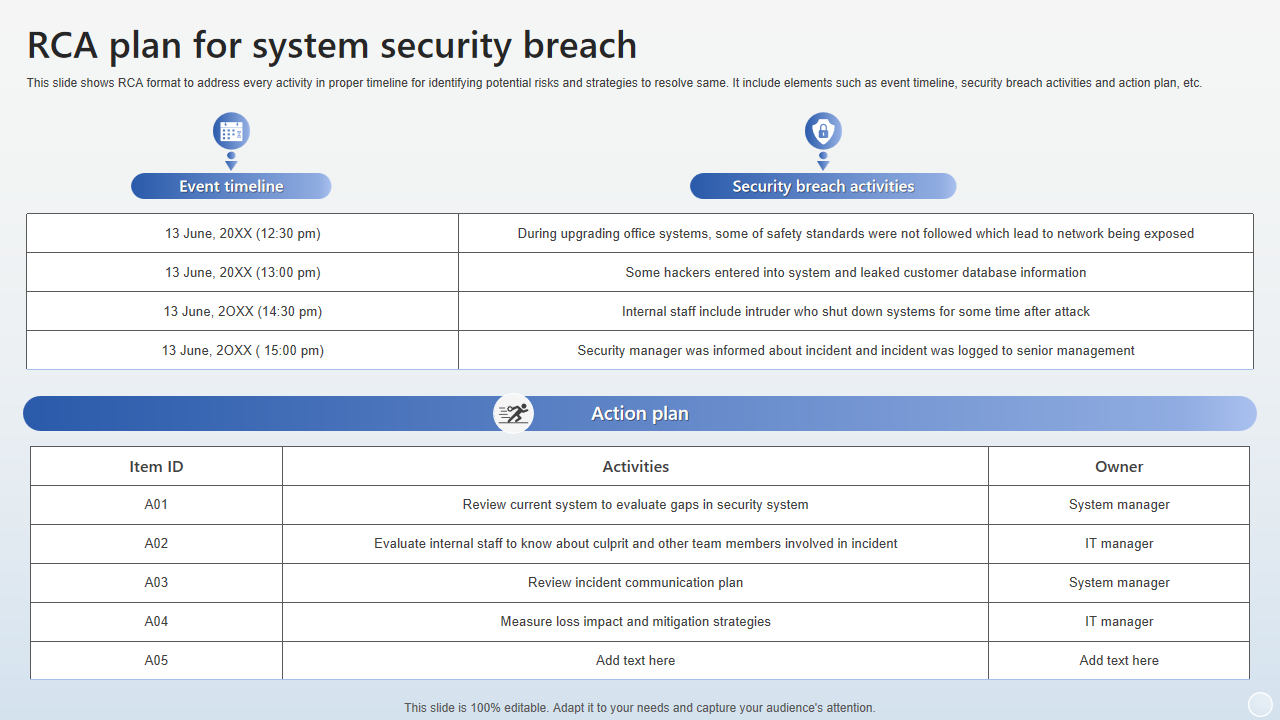
Template 3 – RCA Plan for System Security Breach
Deliver a rapid cybersecurity plan to identify potential risks and develop appropriate strategies for the same in a most remarkable manner. This template has been extensively designed to evaluate situations to stop the breach, look into what caused it, and fix the problem. This template lets you Inform the pertinent stakeholders and the Incident Response Team (IRT) immediately. Keep a record of the initial incident's specifics, such as the date, time, and type of breach. Examine the incident response procedure and make any needed adjustments. To stop future breaches, offer employees education and awareness programs. Continually improve security protocols in light of acquired lessons. Recall that a quick response is crucial in the event of a security breach. The RCA plan should be thoroughly documented, tested frequently, and updated to consider new risks and technological advancements. Ensure that you address every activity in the proper timeline for identifying and resolving risks the fastest.
System security – a route to threat and risk-free data operations with SlideTeam.
A robust system security plan is essential in today's connected and digital corporate environment to defend against the many dangers posed by cybercriminals. Investing in appropriate system security plans increases the company's survival and success rate in the modern world while keeping it safe and sturdy in data operations as it goes beyond simple compliance. Download the system security templates from SlideTeam to manage and safeguard your data at the same time. With the right techniques, you can lower possible risks and grow your firm.
FAQs on System Security Plans
1. How do I create a system security plan?
The goal of a system security plan is to highlight the system's security requirements, as well as the controls currently in place or planned, as well as the roles and expected conduct of every user of the system.
- Define the ambit of the program - Define the SSP's goal in detail. Include the systems it covers, system boundaries, and any dependencies in your description of the SSP's scope.
- Key stakeholders to identify - Identify stakeholders in the system's security, such as the system's owners, administrators, users, and auditors.
- Collect information – Keep a list of all the relevant information regarding the documentation assets, inventories, and previous or latest security assignments.
- Compliance and Regulatory Requirements: - Identify whether your system needs to comply with regulations or standards.
- Risk evaluation - Perform a risk assessment to find potential threats, weaknesses, and dangers related to the system. Based on this, security restrictions are chosen.
- Security guidelines and practices - Explain the security guidelines and practices that have been put in place or will soon be implemented to enforce the chosen measures.
- Response to Incident Plan - Include a plan for responding to security incidents and breaches that explains how the organization will handle them.
- Access Management - Describe the user authentication and authorization processes used to control access to the system and its resources.
- Evaluating and approving – Ensure that management and security professionals, among others, evaluate and approve the System Security Plan.
Update the System Security Plan frequently for system modifications, security threats, and legal obligations. Access Control and Distribution while defining the SSP's distribution and storage methods and who has access to it. Check to see if the security controls included in the SSP are being appropriately used and performing as intended. Create a procedure for continual system security monitoring, evaluation, and improvement.
2. Who needs a system security plan?
Organizations and entities that operate information systems and handle sensitive or regulated data frequently need a System Security Plan (SSP).
3. What are the benefits of a system security plan?
Business owners need a system security plan to protect their company from dangers or potential attacks. By implementing a system security plan, you can protect your company from cyberattacks, data breaches, and other security risks. The System Security plan offers a thorough and detailed review of the company's cybersecurity policies and practices, ensuring that all teams and employees are on the same page and aware of their respective roles in maintaining security.





 Customer Reviews
Customer Reviews