One cannot overstate the importance of thorough threat assessments in an increasingly dynamic and interconnected world.
An organized and rigorous threat assessment entails the systematic identification, in-depth investigation, and thorough evaluation of potential dangers. These gaps can negatively affect an organization's priceless assets, key personnel, or complex operations. The main goal is to understand vulnerabilities and create efficient mitigation measures that guarantee organizational security and stability.
Learn to make wise decisions to reduce risks effectively with our premium assessment process templates.
Hence, SlideTeam brings forth an array of threat assessment templates that are designed to meet the growing standards of perfection. With easily customizable slides, you can tailor each of these templates according to your own business needs.
Let's jump in!
Template 1: Cyber security Risk Analysis and Management Plan Template
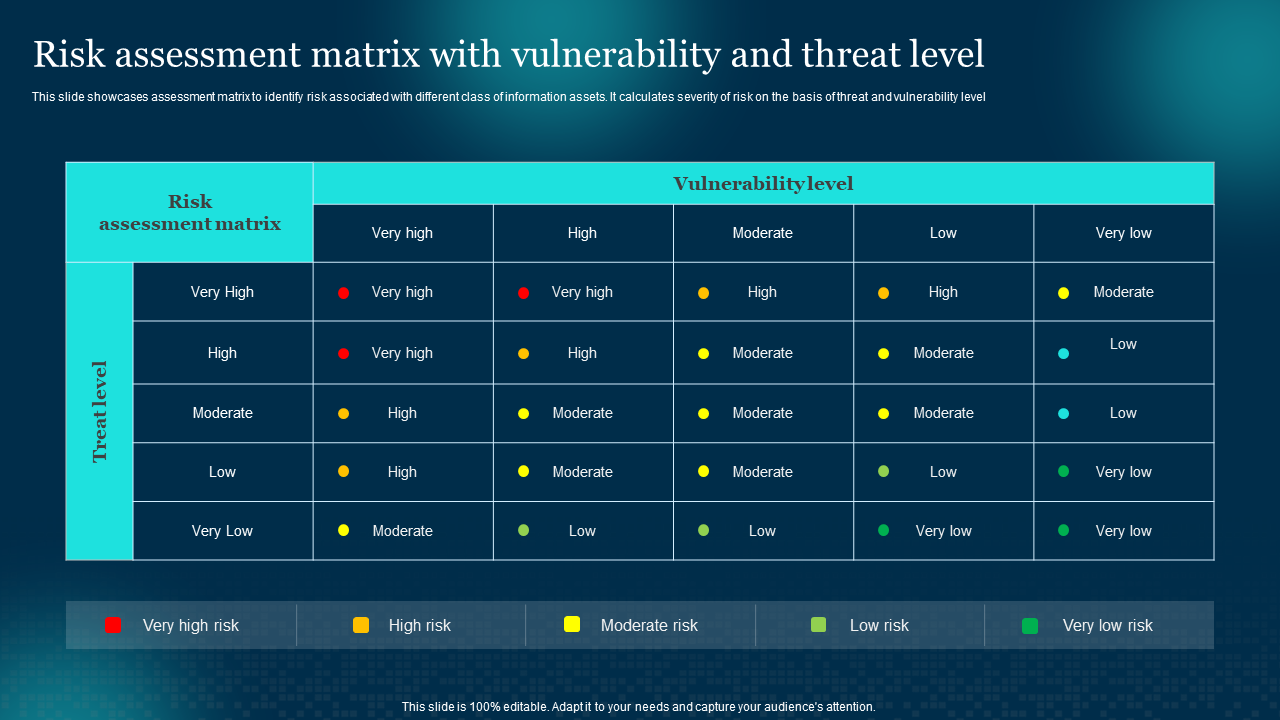
This thorough template is a road map for locating and analyzing potential cyber risks. It includes in-depth risk assessment, threat categorization, suggested countermeasures, and techniques for the smooth execution of incident response plans. You can use this template to determine the likelihood of data breaches and create elaborate policies for their prevention. It helps you demarcate the level of vulnerability in each threat and understand the risks of your business. Download now!
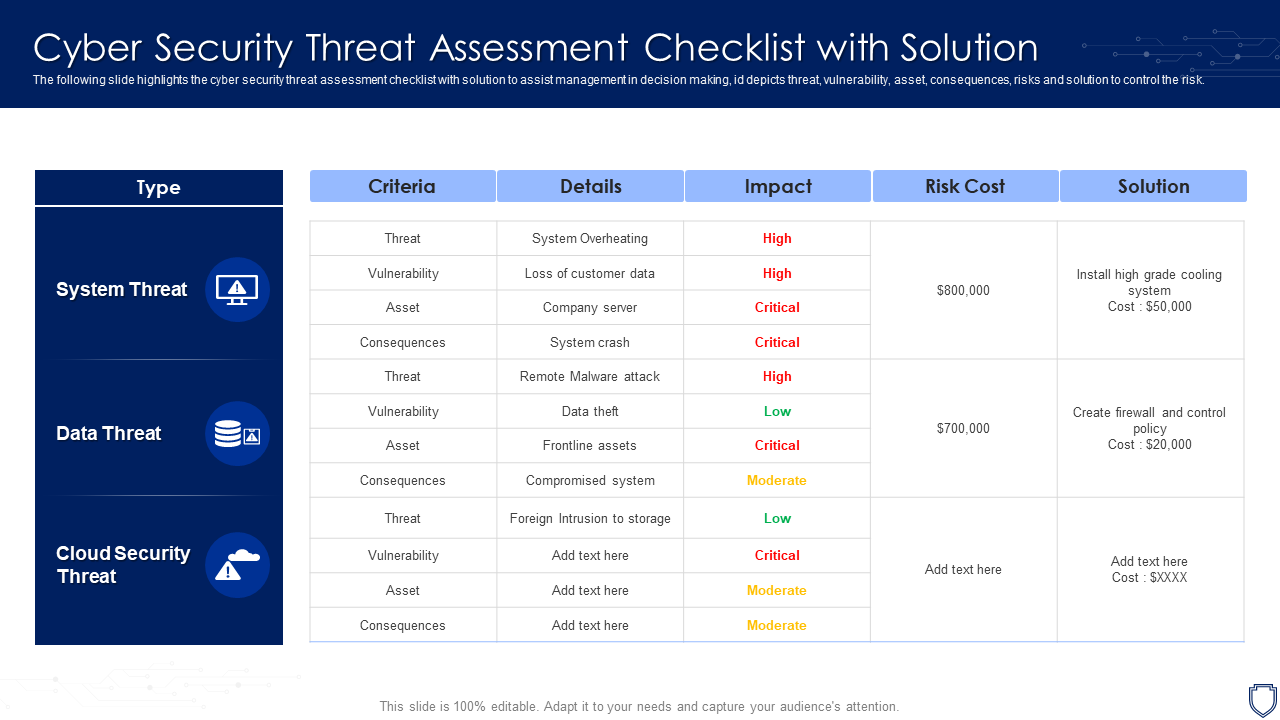
Template 2: Cyber Security Threat Assessment Checklist with Solution
This comprehensive presentation serves as a guide for identifying and evaluating potential cyber hazards. This slide can be used to understand the cybersecurity risks and develop comprehensive strategies for preventing them. This ready-made template comprises an elaborated section for listing out the various criteria’s and their details and the impact they might have on the business. It also includes the cost of dealing with the risk and the solutions for the same. Download now!
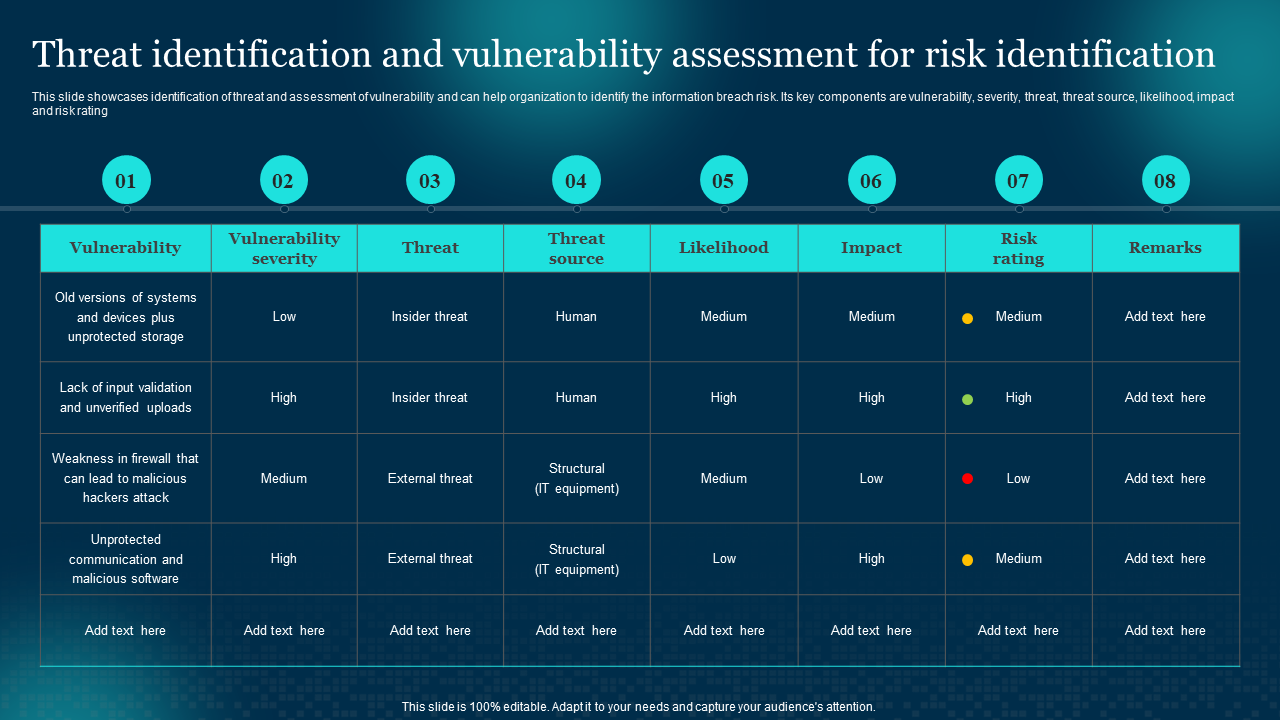
Template 3: Threat Identification and Vulnerability Assessment for Cybersecurity Template
This ready to use template provides a thorough framework for detecting vulnerabilities and evaluating their exploitability. The template includes complex methods for assessing danger, painstaking prioritization, the creation of efficient defenses and other slides. It includes columns for vulnerability, the various threats and their source and the impact they can have in the business. It also has specific assigned columns for the likelihood and impact of the risks and finally, the remarks of the company in the very end. Download now!
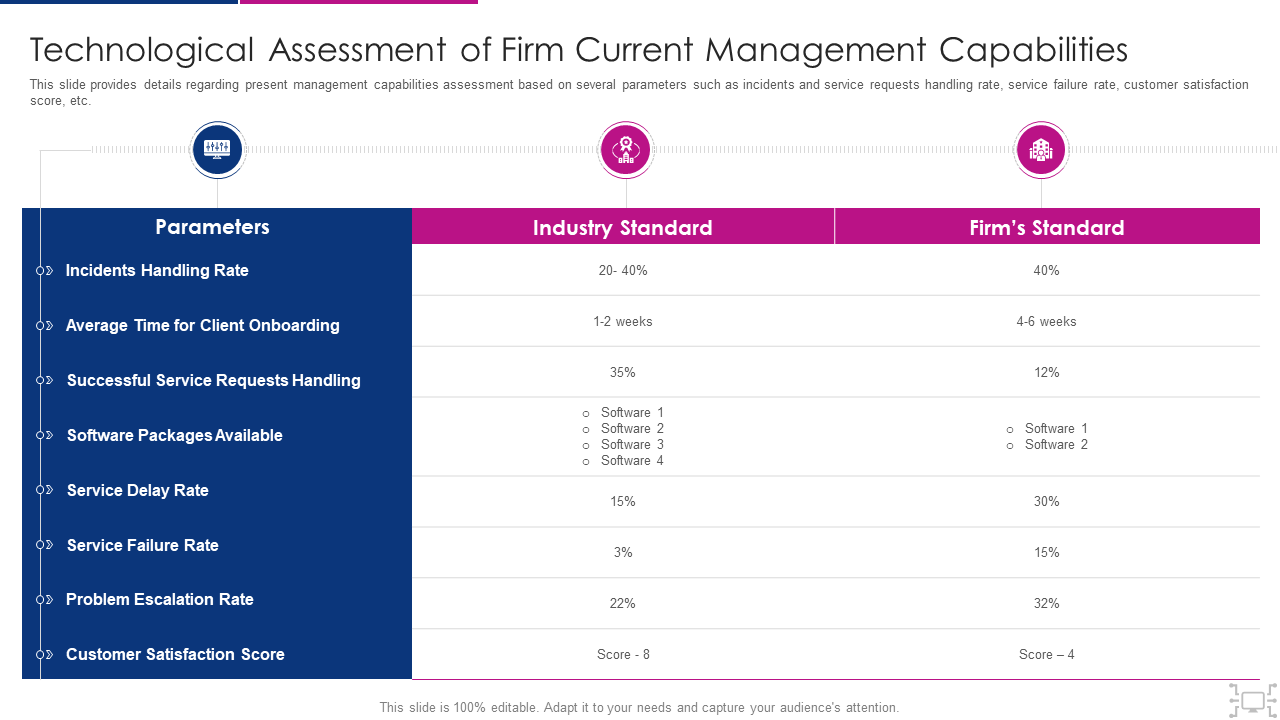
Template 4: Cyber Threat Management Workplace Technological Assessment Firm Current Template
This template is made specifically for the threats from technology integration in the workplace. It addresses many issues, including dangers related to remote work environments, difficulties created by BYOD rules, and vulnerabilities linked with IoT devices. Assessing the dangers associated with illegal device access and putting multi-factor authentication mechanisms in place to increase security could be a helpful application. The template includes designated areas for listing out the various parameters where risk assessment is necessary like onboarding time and the rate of service failure. Download now!
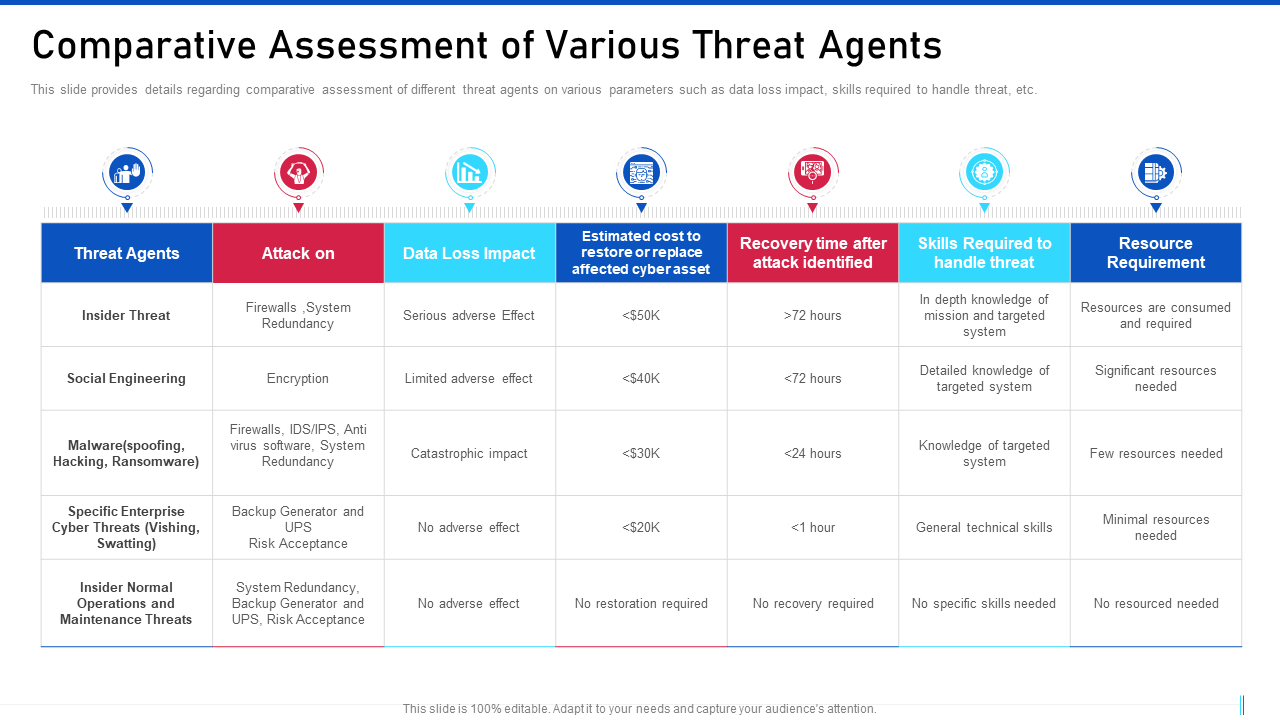
Template 5: Threat Management for Organization Critical Comparative Assessment Template
This premium template provides a broad canvas for the assessment of threats across various departments or divisions and is tailored to varied enterprises. It allows for a thorough comparison of threats and their numerous repercussions across different organizational levels. It provides specific columns for the various threat agents and their areas of attack. It allows the company to list out the impact of the risks on the business and the estimated cost of the threat removal. The template also has a table for listing the estimated recovery time and allows the company to assemble the various skills required for dealing with the risk. Download now!
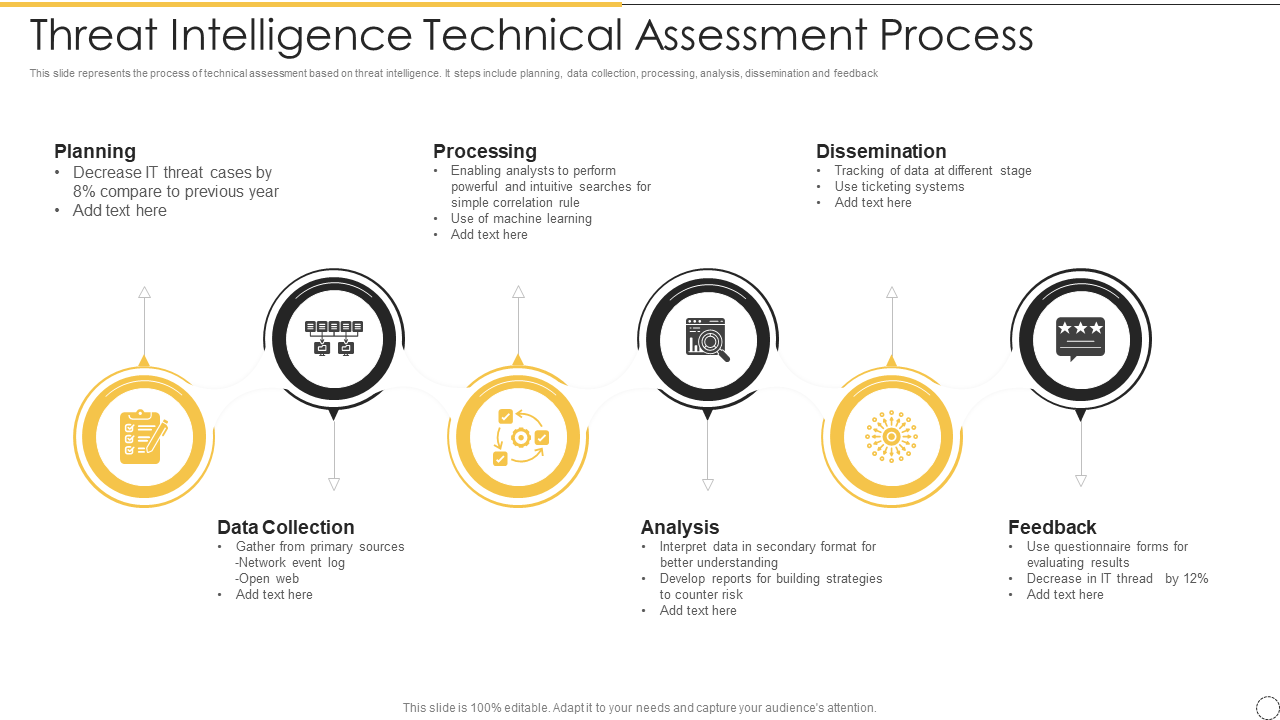
Template 6: Threat Intelligence Technical Assessment Process
This template focuses on using threat intelligence to speed up thorough assessment processes. It describes a systematic procedure for gathering, examining, and operationalizing threat data. You can include real-time threat feeds in an exemplary solution to spot new patterns in malware behavior and create proactive defenses. This template is made in a flowchart pattern that helps point out the three major aspects of risk management, namely, planning, processing and dissemination. It also allows areas for jotting down the data collection strategy, analysis of risks and the final feedbacks of the company. Download now!
Conclusion
Threat assessment is a fundamental component of strategic decision-making in the uncertainty that defines our environment. The presented templates go beyond theoretical ideas, providing practical frameworks for various hypothetical threat scenarios. By adapting and using these templates, organizations can improve their level of readiness and strengthen their capacity to deal with potential obstacles, demonstrating resilience in the face of adversity.
FAQs on Threat Assessment
What are the three primary objectives of a threat assessment?
Identifying potential risks, evaluating those risks' potential effects, and developing adaptable methods to manage or reduce those risks effectively are the three key goals of a thorough threat assessment.
Why is threat assessment a critical aspect of organizational planning?
Threat assessment is paramount since it helps organizations foresee, comprehend, and proactively manage potential hazards. This proactive strategy guarantees operational continuity, effective resource allocation, and the protection of people and priceless assets.
What is the systematic approach to conducting a comprehensive threat assessment?
To conduct a thorough threat assessment, you must identify prospective threats methodically, consider their likelihood and potential effects carefully, and develop mitigation or response measures. Structured templates can offer a strong framework for this rigorous procedure when used as recommendations.





 Customer Reviews
Customer Reviews