Powerpoint Templates and Google slides for Cyber Threat Management
Save Your Time and attract your audience with our fully editable PPT Templates and Slides.
-
 Comprehending Cyber Threats Training Ppt
Comprehending Cyber Threats Training PptPresenting Training Deck on Comprehending Cyber Threats. This deck comprises of 90 slides. Each slide is well crafted and designed by our PowerPoint experts. This PPT presentation is thoroughly researched by the experts, and every slide consists of appropriate content. All slides are customizable. You can add or delete the content as per your need. Not just this, you can also make the required changes in the charts and graphs. Download this professionally designed business presentation, add your content, and present it with confidence.
-
 Cyber Threats In Blockchain World Best Practices BCT CD V
Cyber Threats In Blockchain World Best Practices BCT CD VDeliver this complete deck to your team members and other collaborators. Encompassed with stylized slides presenting various concepts, this Cyber Threats In Blockchain World Best Practices BCT CD V is the best tool you can utilize. Personalize its content and graphics to make it unique and thought-provoking. All the seventy seven slides are editable and modifiable, so feel free to adjust them to your business setting. The font, color, and other components also come in an editable format making this PPT design the best choice for your next presentation. So, download now.
-
 Building A Security Awareness Program To Educate Employees About Cyber Threats Complete Deck
Building A Security Awareness Program To Educate Employees About Cyber Threats Complete DeckDeliver this complete deck to your team members and other collaborators. Encompassed with stylized slides presenting various concepts, this Building A Security Awareness Program To Educate Employees About Cyber Threats Complete Deck is the best tool you can utilize. Personalize its content and graphics to make it unique and thought-provoking. All the seventy eight slides are editable and modifiable, so feel free to adjust them to your business setting. The font, color, and other components also come in an editable format making this PPT design the best choice for your next presentation. So, download now.
-
 Cyber threat management at workplace powerpoint presentation slides
Cyber threat management at workplace powerpoint presentation slidesDeliver this complete deck to your team members and other collaborators. Encompassed with stylized slides presenting various concepts, this Cyber Threat Management At Workplace Powerpoint Presentation Slides is the best tool you can utilize. Personalize its content and graphics to make it unique and thought-provoking. All the sixty eight slides are editable and modifiable, so feel free to adjust them to your business setting. The font, color, and other components also come in an editable format making this PPT design the best choice for your next presentation. So, download now.
-
 Cyber Terrorism Attacks Powerpoint Presentation Slides
Cyber Terrorism Attacks Powerpoint Presentation SlidesEnthrall your audience with this Cyber Terrorism Attacks Powerpoint Presentation Slides. Increase your presentation threshold by deploying this well-crafted template. It acts as a great communication tool due to its well-researched content. It also contains stylized icons, graphics, visuals etc, which make it an immediate attention-grabber. Comprising seventy one slides, this complete deck is all you need to get noticed. All the slides and their content can be altered to suit your unique business setting. Not only that, other components and graphics can also be modified to add personal touches to this prefabricated set.
-
 Implementing Strategies To Mitigate Cyber Security Threats Powerpoint Presentation Slides
Implementing Strategies To Mitigate Cyber Security Threats Powerpoint Presentation SlidesDeliver this complete deck to your team members and other collaborators. Encompassed with stylized slides presenting various concepts, this Implementing Strategies To Mitigate Cyber Security Threats Powerpoint Presentation Slides is the best tool you can utilize. Personalize its content and graphics to make it unique and thought-provoking. All the sixty slides are editable and modifiable, so feel free to adjust them to your business setting. The font, color, and other components also come in an editable format making this PPT design the best choice for your next presentation. So, download now.
-
 Proper data management in healthcare company to reduce cyber threats complete deck
Proper data management in healthcare company to reduce cyber threats complete deckEnthrall your audience with this Proper Data Management In Healthcare Company To Reduce Cyber Threats Complete Deck. Increase your presentation threshold by deploying this well crafted template. It acts as a great communication tool due to its well researched content. It also contains stylized icons, graphics, visuals etc, which make it an immediate attention grabber. Comprising fourty four slides, this complete deck is all you need to get noticed. All the slides and their content can be altered to suit your unique business setting. Not only that, other components and graphics can also be modified to add personal touches to this prefabricated set.
-
 Effective security monitoring plan to eliminate cyber threats and data breaches complete deck
Effective security monitoring plan to eliminate cyber threats and data breaches complete deckEnthrall your audience with this Effective Security Monitoring Plan To Eliminate Cyber Threats And Data Breaches Complete Deck. Increase your presentation threshold by deploying this well crafted template. It acts as a great communication tool due to its well researched content. It also contains stylized icons, graphics, visuals etc, which make it an immediate attention grabber. Comprising fourty four slides, this complete deck is all you need to get noticed. All the slides and their content can be altered to suit your unique business setting. Not only that, other components and graphics can also be modified to add personal touches to this prefabricated set.
-
 Types Of Cyber Threats Training Ppt
Types Of Cyber Threats Training PptPresenting Types of Cyber Threats. These slides are 100 percent made in PowerPoint and are compatible with all screen types and monitors. They also support Google Slides. Premium Customer Support available. Suitable for use by managers, employees, and organizations. These slides are easily customizable. You can edit the color, text, icon, and font size to suit your requirements.
-
 Cyber threat powerpoint ppt template bundles
Cyber threat powerpoint ppt template bundlesIf you require a professional template with great design, then this Cyber Threat Powerpoint PPT Template Bundles is an ideal fit for you. Deploy it to enthrall your audience and increase your presentation threshold with the right graphics, images, and structure. Portray your ideas and vision using twenty three slides included in this complete deck. This template is suitable for expert discussion meetings presenting your views on the topic. With a variety of slides having the same thematic representation, this template can be regarded as a complete package. It employs some of the best design practices, so everything is well-structured. Not only this, it responds to all your needs and requirements by quickly adapting itself to the changes you make. This PPT slideshow is available for immediate download in PNG, JPG, and PDF formats, further enhancing its usability. Grab it by clicking the download button.
-
 Cyber Bullying Powerpoint Ppt Template Bundles
Cyber Bullying Powerpoint Ppt Template BundlesDeliver a credible and compelling presentation by deploying this Cyber Bullying Powerpoint Ppt Template Bundles. Intensify your message with the right graphics, images, icons, etc. presented in this complete deck. This PPT template is a great starting point to convey your messages and build a good collaboration. The twenty two slides added to this PowerPoint slideshow helps you present a thorough explanation of the topic. You can use it to study and present various kinds of information in the form of stats, figures, data charts, and many more. This Cyber Bullying Powerpoint Ppt Template Bundles PPT slideshow is available for use in standard and widescreen aspects ratios. So, you can use it as per your convenience. Apart from this, it can be downloaded in PNG, JPG, and PDF formats, all completely editable and modifiable. The most profound feature of this PPT design is that it is fully compatible with Google Slides making it suitable for every industry and business domain.
-
 Cyber Threats Management To Enable Digital Assets Security Powerpoint Ppt Template Bundles DK MD
Cyber Threats Management To Enable Digital Assets Security Powerpoint Ppt Template Bundles DK MDIf you require a professional template with great design, then this Cyber Threats Management To Enable Digital Assets Security Powerpoint Ppt Template Bundles DK MD is an ideal fit for you. Deploy it to enthrall your audience and increase your presentation threshold with the right graphics, images, and structure. Portray your ideas and vision using twenty one slides included in this complete deck. This template is suitable for expert discussion meetings presenting your views on the topic. With a variety of slides having the same thematic representation, this template can be regarded as a complete package. It employs some of the best design practices, so everything is well-structured. Not only this, it responds to all your needs and requirements by quickly adapting itself to the changes you make. This PPT slideshow is available for immediate download in PNG, JPG, and PDF formats, further enhancing its usability. Grab it by clicking the download button.
-
 Cyber Terrorism Powerpoint PPT Template Bundles
Cyber Terrorism Powerpoint PPT Template BundlesDeliver a credible and compelling presentation by deploying this Cyber Terrorism Powerpoint PPT Template Bundles. Intensify your message with the right graphics, images, icons, etc. presented in this complete deck. This PPT template is a great starting point to convey your messages and build a good collaboration. The eighteen slides added to this PowerPoint slideshow helps you present a thorough explanation of the topic. You can use it to study and present various kinds of information in the form of stats, figures, data charts, and many more. This Cyber Terrorism Powerpoint PPT Template Bundles PPT slideshow is available for use in standard and widescreen aspects ratios. So, you can use it as per your convenience. Apart from this, it can be downloaded in PNG, JPG, and PDF formats, all completely editable and modifiable. The most profound feature of this PPT design is that it is fully compatible with Google Slides making it suitable for every industry and business domain.
-
 Cyber Security Threats Powerpoint Ppt Template Bundles
Cyber Security Threats Powerpoint Ppt Template BundlesDeliver a lucid presentation by utilizing this Cyber Security Threats Powerpoint Ppt Template Bundles. Use it to present an overview of the topic with the right visuals, themes, shapes, and graphics. This is an expertly designed complete deck that reinforces positive thoughts and actions. Use it to provide visual cues to your audience and help them make informed decisions. A wide variety of discussion topics can be covered with this creative bundle such as Business Cyber Security And Attacks, Cyber Threat And Security Management, Computer Security Threats, Potential Cyber Risk. All the seventeen slides are available for immediate download and use. They can be edited and modified to add a personal touch to the presentation. This helps in creating a unique presentation every time. Not only that, with a host of editable features, this presentation can be used by any industry or business vertical depending on their needs and requirements. The compatibility with Google Slides is another feature to look out for in the PPT slideshow.
-
 Global Cyber Security Threats powerpoint presentation and google slides ICP
Global Cyber Security Threats powerpoint presentation and google slides ICPThis PowerPoint presentation provides an overview of the current global cyber security threats. It examines the types of threats, their sources, and the potential impacts of cyber attacks. It also provides an overview of the strategies and tools available to organizations to protect themselves from such threats. The presentation also looks at the implications of cyber attacks on businesses, governments, and individuals. Finally, it outlines the steps organizations can take to mitigate the risks associated with cyber attacks. This presentation is designed to provide an understanding of the current cyber security landscape and help organizations make informed decisions about how to protect themselves.
-
 Adware As A Cyber Threat In Cybersecurity Training Ppt
Adware As A Cyber Threat In Cybersecurity Training PptPresenting Adware as a Cyber Threat in Cybersecurity. This PPT presentation is thoroughly researched and each slide consists of appropriate content. Designed by PowerPoint specialists, this PPT is fully customizable alter the colors, text, icons, and font size to meet your needs. Compatible with Google Slides and backed by superior customer support. Download today to deliver your presentation confidently.
-
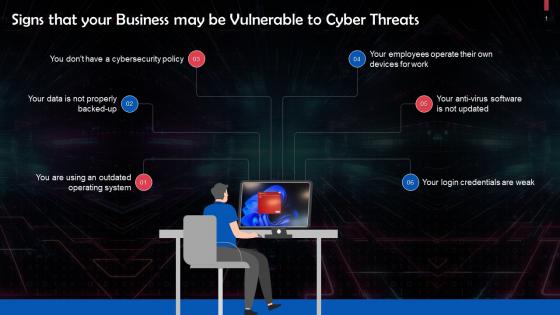 Signs That Your Business May Be Vulnerable To Cyber Threats Training Ppt
Signs That Your Business May Be Vulnerable To Cyber Threats Training PptPresenting Signs that your Business may be Vulnerable to Cyber Threats. This PPT presentation is thoroughly researched and each slide consists of appropriate content. Designed by PowerPoint specialists, this PPT is fully customizable alter the colors, text, icons, and font size to meet your needs. Compatible with Google Slides and backed by superior customer support. Download today to deliver your presentation confidently.
-
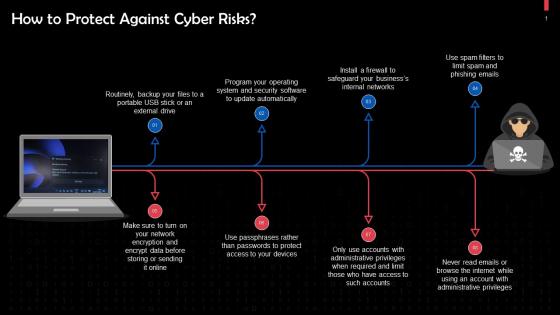 Protection Against Cyber Threats And Attacks Training Ppt
Protection Against Cyber Threats And Attacks Training PptPresenting Protection Against Cyber Threats and Attacks. This PPT presentation is meticulously researched and each slide consists of relevant content. Designed by SlideTeams PowerPoint experts, this PPT is fully customizable alter the colors, text, icons, and font size to meet your requirements. Compatible with Google Slides and backed by excellent customer support. Download to present with poise and assurance.
-
 Malware As A Type Of Cyber Threat Training Ppt
Malware As A Type Of Cyber Threat Training PptPresenting Malware as a Type of Cyber Threat. This PPT presentation is meticulously researched and each slide consists of relevant content. Designed by SlideTeams PowerPoint experts, this PPT is fully customizable alter the colors, text, icons, and font size to meet your requirements. Compatible with Google Slides and backed by excellent customer support. Download to present with poise and assurance.
-
 Cyber Security Icon Network Protection Threat Server Database Software
Cyber Security Icon Network Protection Threat Server Database SoftwareKeep your audience glued to their seats with professionally designed PPT slides. This deck comprises of total of twelve slides. It has PPT templates with creative visuals and well researched content. Not just this, our PowerPoint professionals have crafted this deck with appropriate diagrams, layouts, icons, graphs, charts and more. This content ready presentation deck is fully editable. Just click the DOWNLOAD button below. Change the colour, text and font size. You can also modify the content as per your need. Get access to this well crafted complete deck presentation and leave your audience stunned.
-
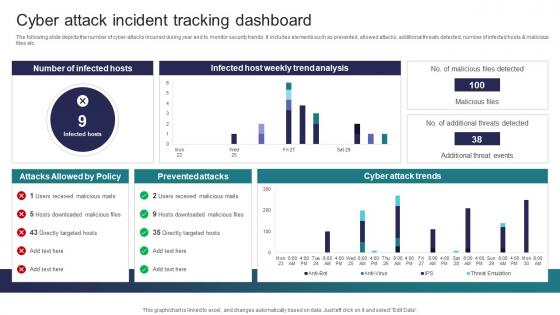 Cyber Attack Incident Tracking Dashboard Implementing Strategies To Mitigate Cyber Security Threats
Cyber Attack Incident Tracking Dashboard Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide depicts the number of cyber attacks incurred during year end to monitor security trends. It includes elements such as prevented, allowed attacks, additional threats detected, number of infected hosts and malicious files etc. Present the topic in a bit more detail with this Cyber Attack Incident Tracking Dashboard Implementing Strategies To Mitigate Cyber Security Threats Use it as a tool for discussion and navigation on Prevented Attacks, Cyber Attack Trends This template is free to edit as deemed fit for your organization. Therefore download it now.
-
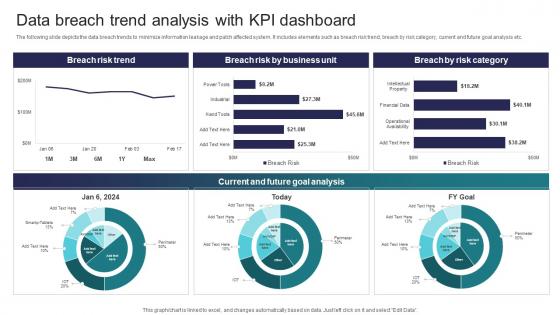 Data Breach Trend Analysis With KPI Dashboard Implementing Strategies To Mitigate Cyber Security Threats
Data Breach Trend Analysis With KPI Dashboard Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide depicts the data breach trends to minimize information leakage and patch affected system. It includes elements such as breach risk trend, breach by risk category, current and future goal analysis etc. Present the topic in a bit more detail with this Data Breach Trend Analysis With KPI Dashboard Implementing Strategies To Mitigate Cyber Security Threats Use it as a tool for discussion and navigation on Current And Future Goal Analysis, Breach Risk Trend This template is free to edit as deemed fit for your organization. Therefore download it now.
-
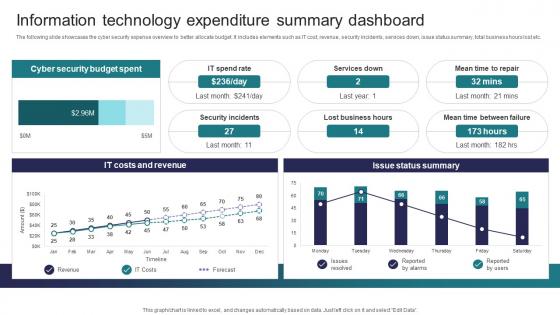 Information Technology Expenditure Summary Implementing Strategies To Mitigate Cyber Security Threats
Information Technology Expenditure Summary Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide showcases the cyber security expense overview to better allocate budget. It includes elements such as IT cost, revenue, security incidents, services down, issue status summary, total business hours lost etc. Deliver an outstanding presentation on the topic using this Information Technology Expenditure Summary Implementing Strategies To Mitigate Cyber Security Threats Dispense information and present a thorough explanation of Cyber Security Budget Spent, It Costs And Revenue, Issue Status Summary using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
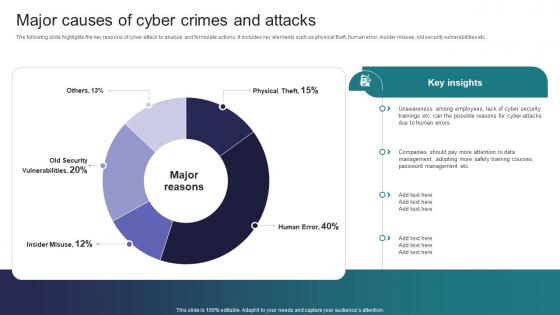 Major Causes Of Cyber Crimes And Attacks Implementing Strategies To Mitigate Cyber Security Threats
Major Causes Of Cyber Crimes And Attacks Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide highlights the key reasons of cyber attack to analyze and formulate actions. It includes key elements such as physical theft, human error, insider misuse, old security vulnerabilities etc. Deliver an outstanding presentation on the topic using this Major Causes Of Cyber Crimes And Attacks Implementing Strategies To Mitigate Cyber Security Threats Dispense information and present a thorough explanation of Employees, Management, Training Courses using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
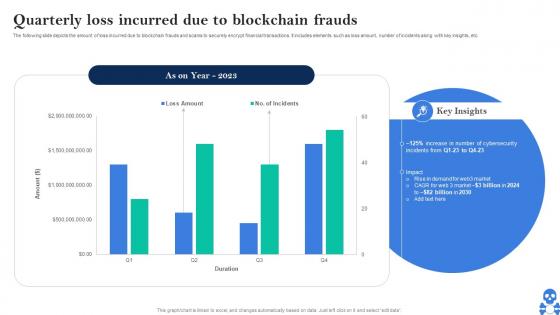 Cyber Threats In Blockchain Quarterly Loss Incurred Due To Blockchain Frauds BCT SS V
Cyber Threats In Blockchain Quarterly Loss Incurred Due To Blockchain Frauds BCT SS VThe following slide depicts the amount of loss incurred due to blockchain frauds and scams to securely encrypt financial transactions. It includes elements such as loss amount, number of incidents along with key insights, etc. Present the topic in a bit more detail with this Cyber Threats In Blockchain Quarterly Loss Incurred Due To Blockchain Frauds BCT SS V Use it as a tool for discussion and navigation on Rise In Demand, Web3 Market This template is free to edit as deemed fit for your organization. Therefore download it now.
-
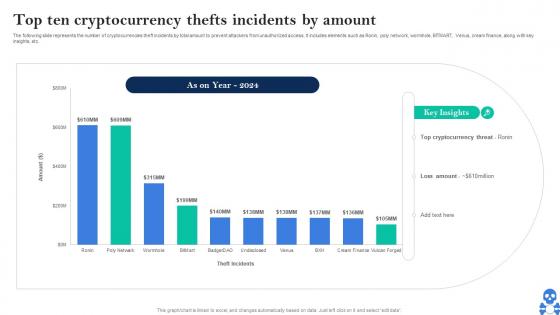 Cyber Threats In Blockchain Top Ten Cryptocurrency Thefts Incidents By Amount BCT SS V
Cyber Threats In Blockchain Top Ten Cryptocurrency Thefts Incidents By Amount BCT SS VThe following slide represents the number of cryptocurrencies theft incidents by total amount to prevent attackers from unauthorized access. It includes elements such as Ronin, poly network, wormhole, BITMART, Venus, cream finance, along with key insights, etc. Present the topic in a bit more detail with this Cyber Threats In Blockchain Top Ten Cryptocurrency Thefts Incidents By Amount BCT SS V Use it as a tool for discussion and navigation on Top Cryptocurrency Threat, Loss Amount This template is free to edit as deemed fit for your organization. Therefore download it now.
-
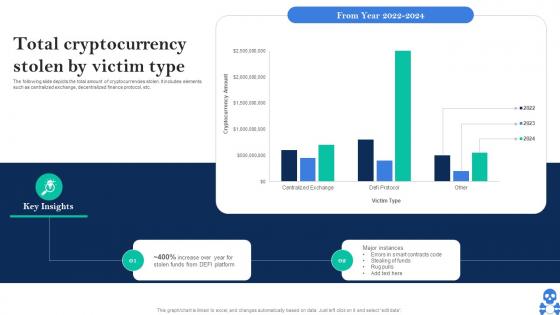 Cyber Threats In Blockchain Total Cryptocurrency Stolen By Victim Type BCT SS V
Cyber Threats In Blockchain Total Cryptocurrency Stolen By Victim Type BCT SS VThe following slide depicts the total amount of cryptocurrencies stolen. It includes elements such as centralized exchange, decentralized finance protocol, etc. Deliver an outstanding presentation on the topic using this Cyber Threats In Blockchain Total Cryptocurrency Stolen By Victim Type BCT SS V Dispense information and present a thorough explanation of Major Instances, Contracts Code using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Cyber Threats In Blockchain Various Types Of Crypto Phishing Attacks BCT SS V
Cyber Threats In Blockchain Various Types Of Crypto Phishing Attacks BCT SS VThe following slide illustrates various types of phishing attacks to analyze how cryptocurrency funds are stolen from blockchain network. It includes elements such as spear, whaling, clone, spoof emails, accessibility to personal details, replacing original link with fake one, etc. Increase audience engagement and knowledge by dispensing information using Cyber Threats In Blockchain Various Types Of Crypto Phishing Attacks BCT SS V This template helps you present information on Three stages. You can also present information on Spear Phishing, Whaling Phishing, Clone Phishing using this PPT design. This layout is completely editable so personaize it now
-
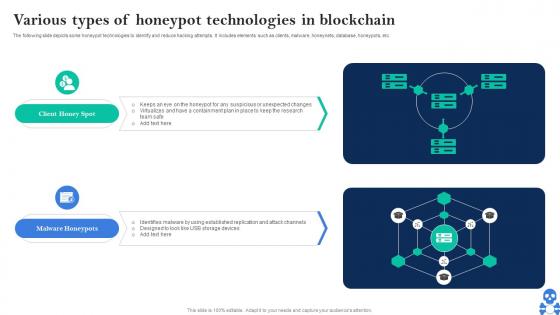 Cyber Threats In Blockchain Various Types Of Honeypot Technologies In Blockchain BCT SS V
Cyber Threats In Blockchain Various Types Of Honeypot Technologies In Blockchain BCT SS VThe following slide depicts some honeypot technologies to identify and reduce hacking attempts. It includes elements such as clients, malware, honeynets, database, honeypots, etc. Increase audience engagement and knowledge by dispensing information using Cyber Threats In Blockchain Various Types Of Honeypot Technologies In Blockchain BCT SS V This template helps you present information on Two stages. You can also present information on Client Honey Spot, Malware Honeypots using this PPT design. This layout is completely editable so personaize it now
-
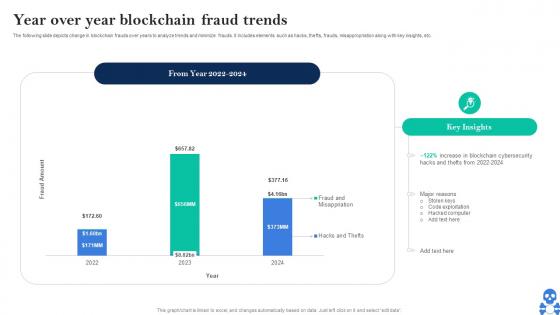 Cyber Threats In Blockchain Year Over Year Blockchain Fraud Trends BCT SS V
Cyber Threats In Blockchain Year Over Year Blockchain Fraud Trends BCT SS VThe following slide depicts change in blockchain frauds over years to analyze trends and minimize frauds. It includes elements such as hacks, thefts, frauds, misappropriation along with key insights, etc. Deliver an outstanding presentation on the topic using this Cyber Threats In Blockchain Year Over Year Blockchain Fraud Trends BCT SS V Dispense information and present a thorough explanation of Major Reasons, Hacked Computer, Blockchain Cybersecurity using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
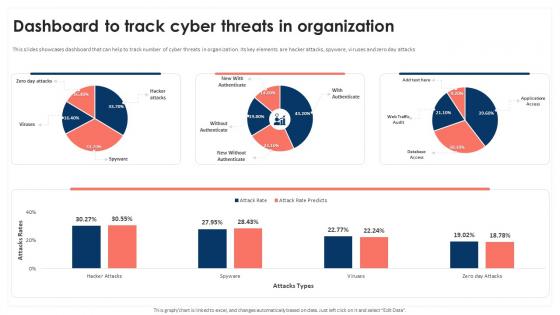 Dashboard To Track Cyber Threats In Organization Mobile Device Security Cybersecurity SS
Dashboard To Track Cyber Threats In Organization Mobile Device Security Cybersecurity SSThis slides showcases dashboard that can help to track number of cyber threats in organization. Its key elements are hacker attacks, spyware, viruses and zero day attacks Present the topic in a bit more detail with this Dashboard To Track Cyber Threats In Organization Mobile Device Security Cybersecurity SS Use it as a tool for discussion and navigation on Track Cyber Threats, Attacks Types This template is free to edit as deemed fit for your organization. Therefore download it now.
-
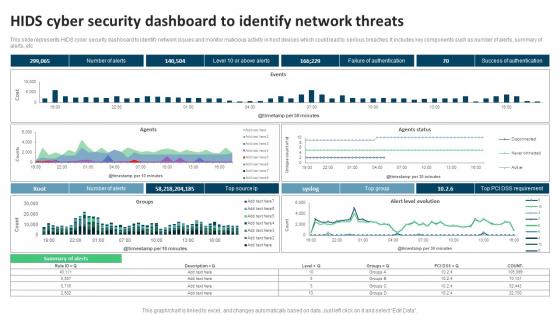 Hids Cyber Security Dashboard To Identify Network Threats
Hids Cyber Security Dashboard To Identify Network ThreatsThis slide represents HIDS cyber security dashboard to identify network issues and monitor malicious activity in host devices which could lead to serious breaches. It includes key components such as number of alerts, summary of alerts, etc Introducing our Hids Cyber Security Dashboard To Identify Network Threats set of slides. The topics discussed in these slides are Security, Dashboard, Network Threats. This is an immediately available PowerPoint presentation that can be conveniently customized. Download it and convince your audience.
-
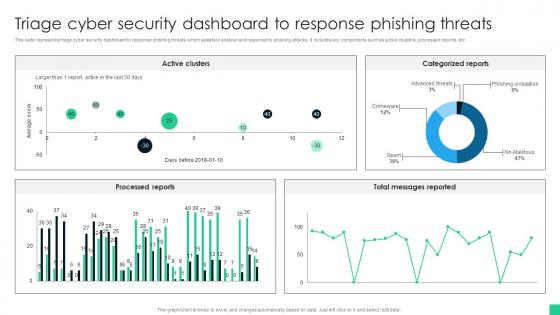 Triage Cyber Security Dashboard To Response Phishing Threats
Triage Cyber Security Dashboard To Response Phishing ThreatsThis slide represents triage cyber security dashboard to response phishing threats which assists to analyse and response to phishing attacks. It includes key components such as active clusters, processed reports, etc Presenting our well structured Triage Cyber Security Dashboard To Response Phishing Threats The topics discussed in this slide are Active Clusters, Categorized Reports. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
 Computer system security cyber threat landscape in computer security
Computer system security cyber threat landscape in computer securityThis slide depicts the cyber threat landscape based on cybercriminal roles or actors and the impacts of successful cyberattacks on business. Present the topic in a bit more detail with this Computer System Security Cyber Threat Landscape In Computer Security. Use it as a tool for discussion and navigation on Financial, Business, Tenant Damage, Organized Criminals, Competitors. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
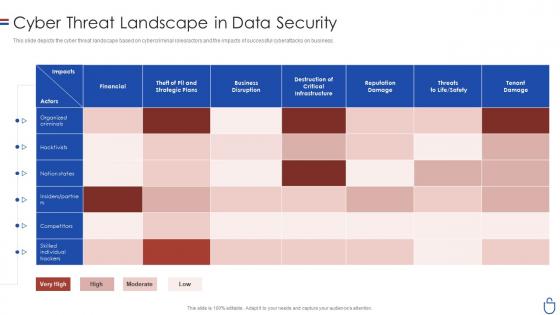 Data security it cyber threat landscape in data security
Data security it cyber threat landscape in data securityThis slide depicts the cyber threat landscape based on cybercriminal roles or actors and the impacts of successful cyberattacks on business. Present the topic in a bit more detail with this Data Security IT Cyber Threat Landscape In Data Security. Use it as a tool for discussion and navigation on Financial, Business Disruption, Reputation Damage, Tenant Damage. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Corporate cyber harassment ppt powerpoint presentation file designs download cpb
Corporate cyber harassment ppt powerpoint presentation file designs download cpbPresenting our Corporate Cyber Harassment Ppt Powerpoint Presentation File Designs Download Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Corporate Cyber Harassment This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Cyber Threat In Powerpoint And Google Slides Cpb
Cyber Threat In Powerpoint And Google Slides CpbPresenting Cyber Threat In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Cyber Threat. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Protect Against Internal Cyber Threats In Powerpoint And Google Slides Cpb
Protect Against Internal Cyber Threats In Powerpoint And Google Slides CpbPresenting our Protect Against Internal Cyber Threats In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases five stages. It is useful to share insightful information on Protect Against Internal Cyber Threats This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
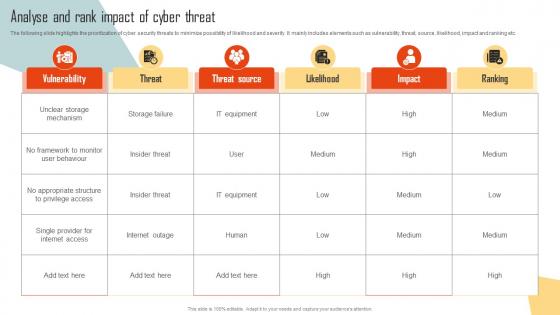 Analyse And Rank Impact Of Cyber Threat Improving Cyber Security Risks Management
Analyse And Rank Impact Of Cyber Threat Improving Cyber Security Risks ManagementThe following slide highlights the prioritization of cyber security threats to minimize possibility of likelihood and severity. It mainly includes elements such as vulnerability, threat, source, likelihood, impact and ranking etc. Present the topic in a bit more detail with this Analyse And Rank Impact Of Cyber Threat Improving Cyber Security Risks Management. Use it as a tool for discussion and navigation on Vulnerability, Threat Source, Appropriate Structure, Privilege Access. This template is free to edit as deemed fit for your organization. Therefore download it now.
-
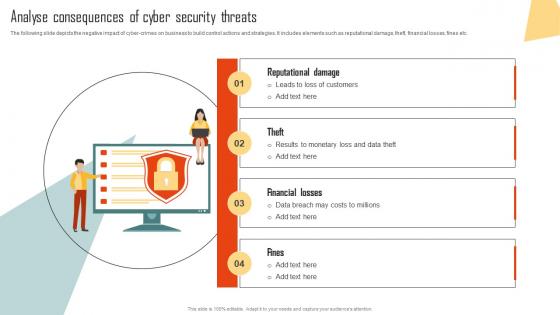 Analyse Consequences Of Cyber Security Threats Improving Cyber Security Risks Management
Analyse Consequences Of Cyber Security Threats Improving Cyber Security Risks ManagementThe following slide depicts the negative impact of cyber-crimes on business to build control actions and strategies. It includes elements such as reputational damage, theft, financial losses, fines etc. Introducing Analyse Consequences Of Cyber Security Threats Improving Cyber Security Risks Management to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Reputational Damage, Financial Losses, Security Threats, using this template. Grab it now to reap its full benefits.
-
 Security Threats Cyber Security In Powerpoint And Google Slides Cpb
Security Threats Cyber Security In Powerpoint And Google Slides CpbPresenting Security Threats Cyber Security In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase Three stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Security Threats Cyber Security. This well-structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
 Cyber Security Threats Organizations In Powerpoint And Google Slides Cpb
Cyber Security Threats Organizations In Powerpoint And Google Slides CpbPresenting our Cyber Security Threats Organizations In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases five stages. It is useful to share insightful information on Cyber Security Threats Organizations. This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Financial Cyber Threat Mitigation AI Image PowerPoint Presentation PPT ECS
Financial Cyber Threat Mitigation AI Image PowerPoint Presentation PPT ECSIntroducing a Visual PPT on Financial Cyber Threat Mitigation. Each PowerPoint Slide has been thoughtfully designed by our team of Presentation Specialists. Adjusting the content is simple, whether you want to add or eliminate details. Plus, this PPT Template can be used on any screen size and is even Google Slides friendly. Grab the PPT, customize to your preference, and present with self assurance.
-
 Cyber Security Threat Malware In Powerpoint And Google Slides Cpb
Cyber Security Threat Malware In Powerpoint And Google Slides CpbPresenting our Cyber Security Threat Malware In Powerpoint And Google Slides Cpb PowerPoint template design. This PowerPoint slide showcases four stages. It is useful to share insightful information on Cyber Security Threat Malware This PPT slide can be easily accessed in standard screen and widescreen aspect ratios. It is also available in various formats like PDF, PNG, and JPG. Not only this, the PowerPoint slideshow is completely editable and you can effortlessly modify the font size, font type, and shapes according to your wish. Our PPT layout is compatible with Google Slides as well, so download and edit it as per your knowledge.
-
 Cyber Security Threat Analytics Icon
Cyber Security Threat Analytics IconPresenting our set of slides with Cyber Security Threat Analytics Icon. This exhibits information on three stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Threat, Security, Analytics.
-
 Internal Cyber Security Threats In Powerpoint And Google Slides Cpb
Internal Cyber Security Threats In Powerpoint And Google Slides CpbPresenting Internal Cyber Security Threats In Powerpoint And Google Slides Cpb slide which is completely adaptable. The graphics in this PowerPoint slide showcase four stages that will help you succinctly convey the information. In addition, you can alternate the color, font size, font type, and shapes of this PPT layout according to your content. This PPT presentation can be accessed with Google Slides and is available in both standard screen and widescreen aspect ratios. It is also a useful set to elucidate topics like Internal Cyber Security Threats. This well structured design can be downloaded in different formats like PDF, JPG, and PNG. So, without any delay, click on the download button now.
-
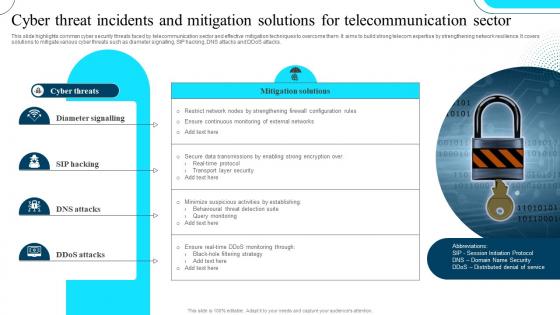 Cyber Threat Incidents And Mitigation Solutions For Telecommunication Sector
Cyber Threat Incidents And Mitigation Solutions For Telecommunication SectorThis slide highlights common cyber security threats faced by telecommunication sector and effective mitigation techniques to overcome them. It aims to build strong telecom expertise by strengthening network resilience. It covers solutions to mitigate various cyber threats such as diameter signalling, SIP hacking, DNS attacks and DDoS attacks. Presenting our set of slides with Cyber Threat Incidents And Mitigation Solutions For Telecommunication Sector This exhibits information on Four stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Diameter Signalling, SIP Hacking, DNS Attacks
-
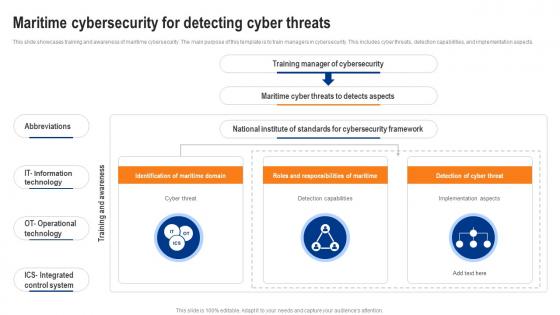 Maritime Cybersecurity For Detecting Cyber Threats
Maritime Cybersecurity For Detecting Cyber ThreatsThis slide showcases training and awareness of maritime cybersecurity. The main purpose of this template is to train managers in cybersecurity. This includes cyber threats, detection capabilities, and implementation aspects. Presenting our well structured Maritime Cybersecurity For Detecting Cyber Threats. The topics discussed in this slide are Detection Capabilities, Implementation Aspects, Operational Technology. This is an instantly available PowerPoint presentation that can be edited conveniently. Download it right away and captivate your audience.
-
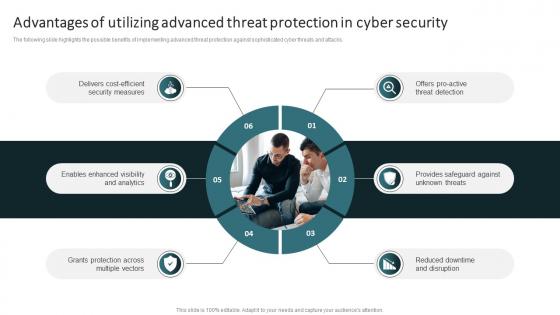 Advantages Of Utilizing Advanced Threat Protection In Cyber Security
Advantages Of Utilizing Advanced Threat Protection In Cyber SecurityThe following slide highlights the possible benefits of implementing advanced threat protection against sophisticated cyber threats and attacks. Presenting our set of slides with Advantages Of Utilizing Advanced Threat Protection In Cyber Security. This exhibits information on six stages of the process. This is an easy to edit and innovatively designed PowerPoint template. So download immediately and highlight information on Security, Analytics, Protection.
-
 IoT Cyber Security Technologies For Advanced Threat Protection
IoT Cyber Security Technologies For Advanced Threat ProtectionThe purpose of this slide is to showcase various types of Internet of Things IoT security technologies that assists in safeguarding cyber threats. Introducing our premium set of slides with IoT Cyber Security Technologies For Advanced Threat Protection. Ellicudate the four stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Architecture, Security, Computing. So download instantly and tailor it with your information.
-
 Saas Cyber Security Icon For Threat Mitigation
Saas Cyber Security Icon For Threat MitigationIntroducing our premium set of slides with Saas Cyber Security Icon For Threat Mitigation Ellicudate the Three stages and present information using this PPT slide. This is a completely adaptable PowerPoint template design that can be used to interpret topics like Saas Cyber Security Icon, Threat Mitigation. So download instantly and tailor it with your information.
-
 Agenda Implementing Strategies To Mitigate Cyber Security Threats
Agenda Implementing Strategies To Mitigate Cyber Security ThreatsIntroducing Agenda Implementing Strategies To Mitigate Cyber Security Threats to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Security Awareness, Risk Management Process, Cyber Risk using this template. Grab it now to reap its full benefits.
-
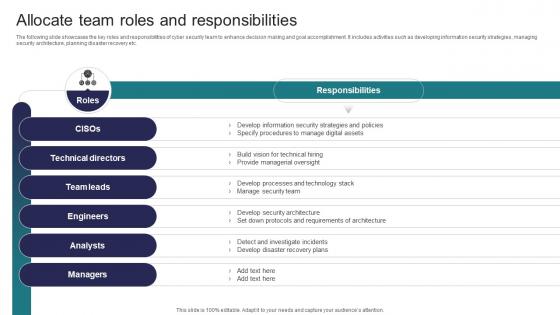 Allocate Team Roles And Responsibilities Implementing Strategies To Mitigate Cyber Security Threats
Allocate Team Roles And Responsibilities Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide showcases the key roles and responsibilities of cyber security team to enhance decision making and goal accomplishment. It includes activities such as developing information security strategies, managing security architecture, planning disaster recovery etc. Deliver an outstanding presentation on the topic using this Allocate Team Roles And Responsibilities Implementing Strategies To Mitigate Cyber Security Threats Dispense information and present a thorough explanation of Technical Directors, Team Leads, Engineers using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
 Analyse And Rank Impact Of Cyber Threat Implementing Strategies To Mitigate Cyber Security Threats
Analyse And Rank Impact Of Cyber Threat Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide highlights the prioritization of cyber security threats to minimize possibility of likelihood and severity. It mainly includes elements such as vulnerability, threat, source, likelihood, impact and ranking etc. Present the topic in a bit more detail with this Analyse And Rank Impact Of Cyber Threat Implementing Strategies To Mitigate Cyber Security Threats Use it as a tool for discussion and navigation on Vulnerability, Threat, Threat Source This template is free to edit as deemed fit for your organization. Therefore download it now.
-
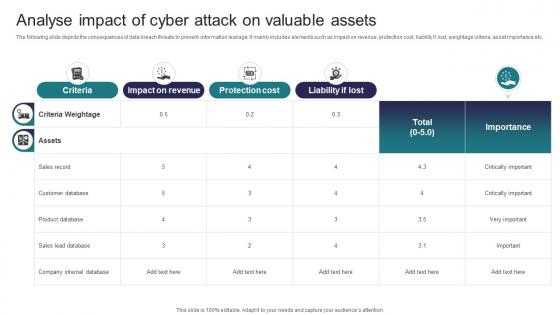 Analyse Impact Of Cyber Attack On Valuable Implementing Strategies To Mitigate Cyber Security Threats
Analyse Impact Of Cyber Attack On Valuable Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide depicts the consequences of data breach threats to prevent information leakage. It mainly includes elements such as impact on revenue, protection cost, liability if lost, weightage criteria, asset importance etc. Deliver an outstanding presentation on the topic using this Analyse Impact Of Cyber Attack On Valuable Implementing Strategies To Mitigate Cyber Security Threats Dispense information and present a thorough explanation of Criteria, Impact On Revenue, Protection Cost using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
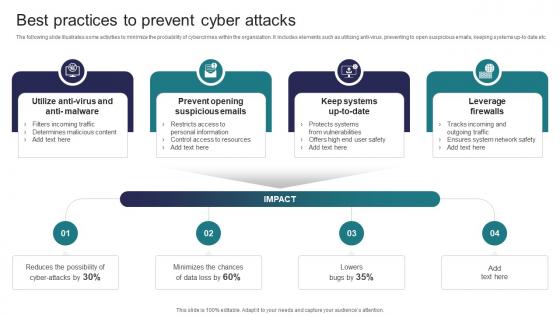 Best Practices To Prevent Cyber Attacks Implementing Strategies To Mitigate Cyber Security Threats
Best Practices To Prevent Cyber Attacks Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide illustrates some activities to minimize the probability of cybercrimes within the organization. It includes elements such as utilizing anti virus, preventing to open suspicious emails, keeping systems up to date etc. Introducing Best Practices To Prevent Cyber Attacks Implementing Strategies To Mitigate Cyber Security Threats to increase your presentation threshold. Encompassed with four stages, this template is a great option to educate and entice your audience. Dispence information on Leverage Firewalls, Prevent Opening Suspicious Emails using this template. Grab it now to reap its full benefits.
-
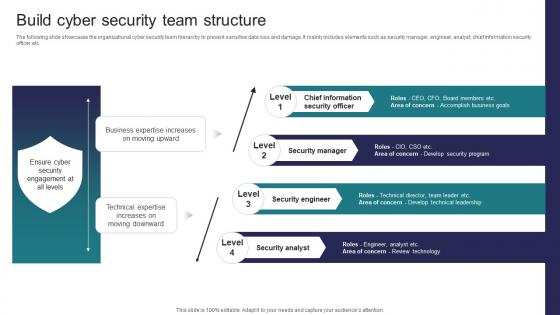 Build Cyber Security Team Structure Implementing Strategies To Mitigate Cyber Security Threats
Build Cyber Security Team Structure Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide showcases the organizational cyber security team hierarchy to prevent sensitive data loss and damage. It mainly includes elements such as security manager, engineer, analyst, chief information security officer etc Increase audience engagement and knowledge by dispensing information using Build Cyber Security Team Structure Implementing Strategies To Mitigate Cyber Security Threats This template helps you present information on four stages. You can also present information on Security Manager, Security Engineer, Security Analyst using this PPT design. This layout is completely editable so personaize it now to meet your audiences expectations.
-
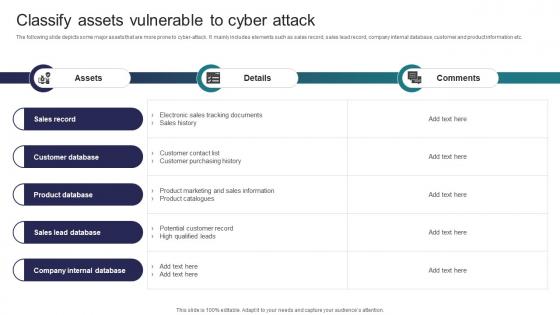 Classify Assets Vulnerable To Cyber Attack Implementing Strategies To Mitigate Cyber Security Threats
Classify Assets Vulnerable To Cyber Attack Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide depicts some major assets that are more prone to cyber attack. It mainly includes elements such as sales record, sales lead record, company internal database, customer and product information etc. Present the topic in a bit more detail with this Classify Assets Vulnerable To Cyber Attack Implementing Strategies To Mitigate Cyber Security Threats Use it as a tool for discussion and navigation on Sales Record, Customer Database, Product Database This template is free to edit as deemed fit for your organization. Therefore download it now.
-
 Conduct Third Party Risk Assessment Implementing Strategies To Mitigate Cyber Security Threats
Conduct Third Party Risk Assessment Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide illustrates checklist to evaluate third party risk assessment to eliminate unnecessary threats. It includes elements such as cyber security policies, patch management process, physical security guidelines, information safety etc. Deliver an outstanding presentation on the topic using this Conduct Third Party Risk Assessment Implementing Strategies To Mitigate Cyber Security Threats Dispense information and present a thorough explanation of Parameters, Response, Status using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.
-
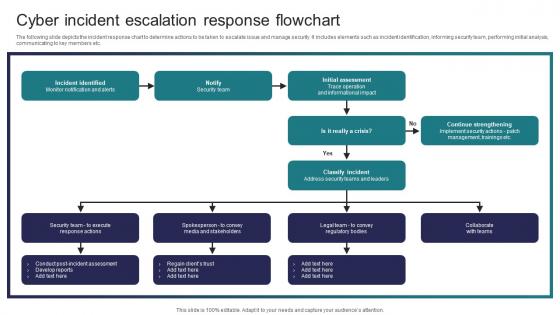 Cyber Incident Escalation Response Flowchart Implementing Strategies To Mitigate Cyber Security Threats
Cyber Incident Escalation Response Flowchart Implementing Strategies To Mitigate Cyber Security ThreatsThe following slide depicts the incident response chart to determine actions to be taken to escalate issue and manage security. It includes elements such as incident identification, informing security team, performing initial analysis, communicating to key members etc. Deliver an outstanding presentation on the topic using this Cyber Incident Escalation Response Flowchart Implementing Strategies To Mitigate Cyber Security Threats Dispense information and present a thorough explanation of Incident Identified, Initial Assessment, Classify Incident using the slides given. This template can be altered and personalized to fit your needs. It is also available for immediate download. So grab it now.


