Watching magicians do cool tricks is fantastic. Imagine, however, if these magicians were sneaky and their tricks turned out to be like a hidden threat (like a wolf in sheep's clothing). The fun would become stressful. These tricky cyber criminals never miss a chance to cause trouble, even during the chaos of the coronavirus pandemic. For instance, some launched a deceptive Mobile Coronavirus Tracking App, creating confusion and messing up with people's heads and pockets.
That's why it's imperative to become a cyber sentinel or have someone vigilant, like a cat on a hot tin roof, especially when dealing with crafty cybercriminals. Now, let's shine a light on the backstage heroes – the cybersecurity experts. They have a secret weapon called the Malware Process Flowchart Template. It's not like a magic wand, but it's pretty close – a roadmap helping figure out the sneaky plans of online tricksters.
Click here to explore SlideTeam's collection of Threat Assessment Templates designed to meet high standards.
Let's look at how these templates can help to build your digital security.
- Early Detection: Visual representation aids in early detection, empowering cybersecurity pros to address threats.
- Incident Response: Guides incident response, helping teams understand malware progression for effective containment.
- Vulnerability Identification: Pinpoints system vulnerabilities, allowing experts to reinforce defenses in critical areas.
- Communication and Collaboration: Acts as a common language, fostering efficient communication within teams and collaboration with external entities.
- Training and Education: Valuable for training, offering a clear visual understanding of malware operations for new and experienced professionals.
- Continuous Improvement: Evolves with cyber threats, ensuring regular updates based on new intelligence to maintain effective defenses.
- Strategic Planning: Assists in developing strategic cybersecurity plans by understanding malware patterns, enabling proactive measures against emerging threats.
Malware analysis is not always straightforward, and developing a flow chart from scratch is even more complex.
CRM is essential for business success. Without it, customer relationships suffer, leading to chaos. Use our CRM Process Flowchart Templates to integrate CRM flowcharts for stability in marketing, sales, and customer support.
However, the 100% editable and customizable templates offered in this post should help you understand what is necessary for malware analysis without being an eyesore.
Look at these SlideTeam Malware Process Flow Chart Templates, which can be applied to scenarios.
Identify the cunning schemes of these internet scammers.
Template 1: Dynamic Malware Analysis Flow Chart
Consider this slide your handy tool for dealing with potential computer threats. It's like a step-by-step guide that ensures you look at how the lousy software behaves. Using this guide ensures you follow a straightforward process, making it easier to catch any problems and understand what's going on. Not only does this slide help you work more efficiently, but it also acts like a note-taking tool. It captures steps and observations during your investigation, so you have a record to refer back to in the future. This is useful for your learning and sharing knowledge among your team.
The slide also makes explaining complicated information about your investigation to other cybersecurity teams easier. It's like a visual map that shows what you're doing and how you're doing it.
Get it now, stay ahead of potential cyber threats, and know how to handle types of attacks.
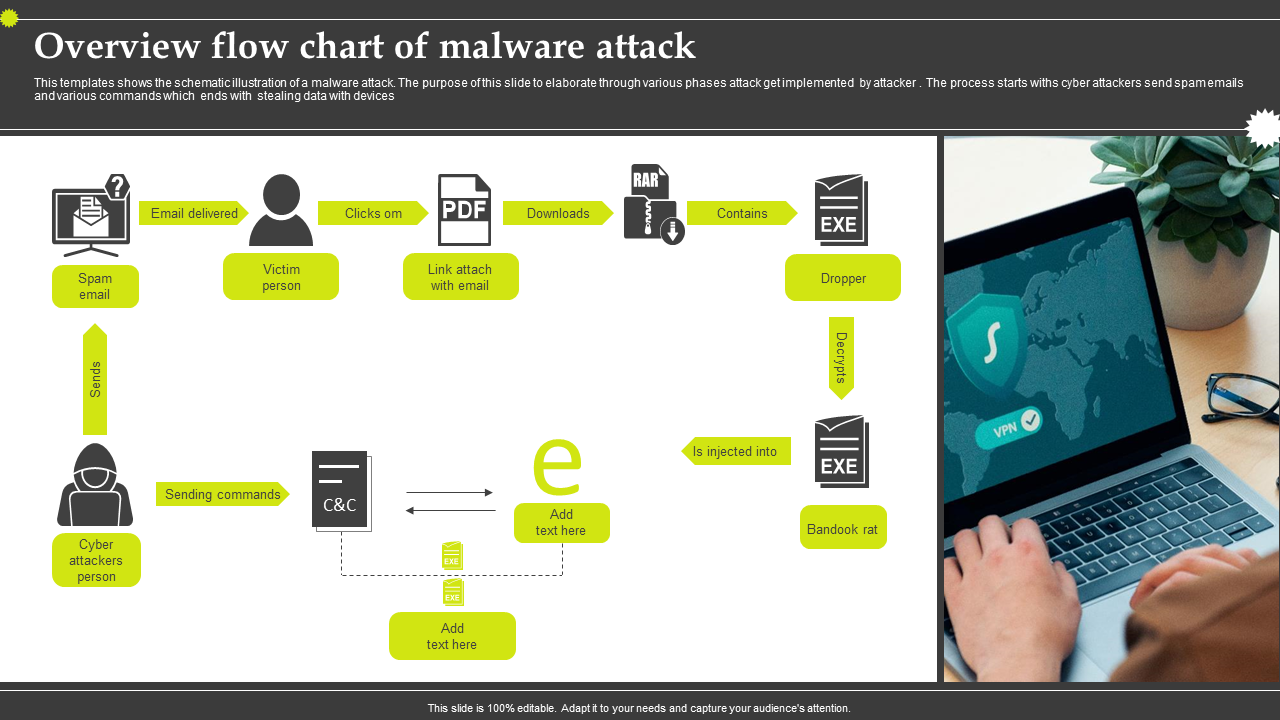
Template 2:Overview Flow Chart Of Malware Attack
The template is an effective tool, offering a visual representation of the malware attack process. This clarity benefits a broad audience, even those without extensive expertise, facilitating a comprehensive grasp of the attack's flow and progression. Beyond its visual appeal, the template provides a structured and organized framework, fostering a systematic examination of the diverse stages of a malware attack. This structured approach enhances the analytical process, allowing for a more in-depth understanding. In addition to dissecting individual stages, the template facilitates a holistic view. This comprehensive perspective empowers analysts to comprehend the broader picture, recognizing how individual components and tactics interconnect to form the overarching threat. Moreover, the template promotes collaboration and knowledge sharing among cybersecurity professionals. Its adaptability allows for seamless sharing across teams and organizations, contributing to a collective improvement in understanding and addressing evolving attack strategies.
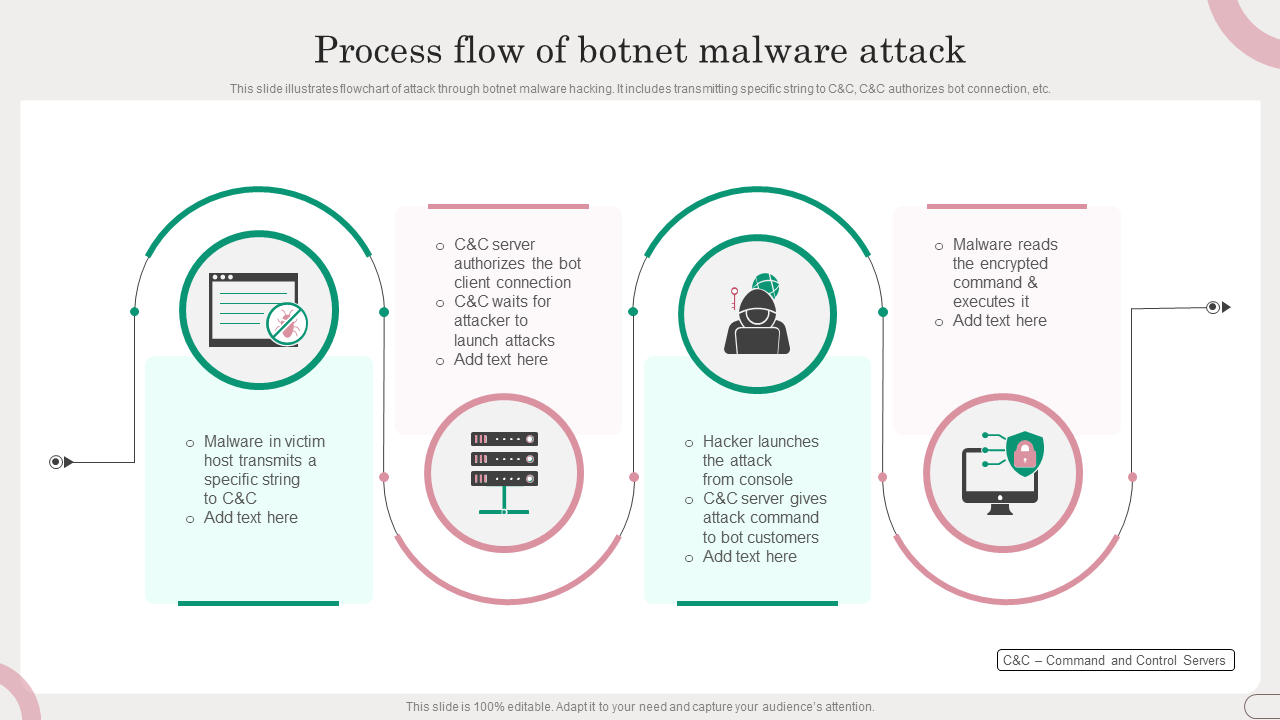
Template 3: Process Flow Of Botnet Malware Attack
Use this template to obtain a clear visual representation of how a botnet malware attack unfolds, simplifying complex information for better accessibility and understanding. It helps break down stages of a botnet malware attack into step-by-step components, offering analysts a structured and organized overview. Outlining potential attack scenarios aids in proactive threat mitigation, empowering organizations to implement preventive measures and strengthen their overall security posture.
Decoding Threats To Safeguard Digital Existence
An effective defensive plan is a must in the digital era due to the increasing sophistication of cyber attacks. These SlideTeam Malware process flow chart templates arm cybersecurity professionals well, providing a guide to understanding, avoiding, and reducing the effect of malware. Organizations may strengthen their defenses and confidently traverse the challenging terrain of the digital frontier by implementing these templates into their cybersecurity operations.
PS: Dealing with security breaches, data theft, and system compromises is a big concern. Check out these Security Incident Response Plans with PPT Templates for a way to handle such situations.





 Customer Reviews
Customer Reviews





![Top 7 Templates on Employee Experience Strategy [Free PPT & PDF]](https://www.slideteam.net/wp/wp-content/uploads/2024/01/Employee-Experience-Strategy-1013x441.jpg)