The Internet records almost all of our data, from identification numbers to family moments caught on camera for posterity. Hackers seek it out with great fervor even if the average person can’t access it. In July 2017, Equifax, a credit reporting agency, suffered a massive data breach. The incident exposed the personal details of approximately 147 million American consumers, including sensitive information such as Social Security numbers, birth dates, addresses, and driver's license numbers. The breach was attributed to a vulnerability in Equifax's website software, which went undetected until late July.
This breach has highlighted the critical need for businesses to enhance cybersecurity measures and safeguard sensitive personal information. It also underscores the significant repercussions of data breaches on individuals, businesses, and society. One of the elements that bolster cybersecurity is a robust firewall. Organizations should keep a constant check on it for its ability to hold against an attack.
To conduct this inspection well and share the results with stakeholders, you need SlideTeam’s Firewall Audit Templates.
We understand how critical cybersecurity is, and therefore, SlideTeam brings you content-ready and 100% editable slides to help you communicate the vital information related to your data to your team and stakeholders for its safeguarding. They provide a starting point, a structured framework, and the flexibility to alter the details according to your needs.
Let’s explore these templates now!
Template 1: Firewall Audit
Conduct a firewall audit with this PPT Deck. It includes slides that help you with the tools you need, such as the process for the audit, network security, types of firewalls, comparative assessment table, and more. This set will help you better understand and explain the process and results to stakeholders. Download now!
Template 2: Six-step Process to Conduct Firewall Audit
This slide presents a structured six-step process for conducting a firewall audit within an organization. The focus is on ensuring network security and mitigating cyber threats. The steps highlighted include:
- Collecting essential data such as firewall logs and security policy reports.
- Auditing the firewall change management process to identify and rectify security breaches.
- Reviewing firewall security policies to ensure compliance with regulatory standards and implementation of security patches.
- Optimizing the firewall rule base to improve system performance and adjust inactive rules.
- Conducting a thorough risk assessment to identify issues like data breaches and non-compliance with standards like FISMA and SOX.
- Implementing security recommendations by prioritizing issues based on risk potential and severity and making the necessary network security adjustments.
Download this template to maintain robust firewall security.
Template 3: Firewall Audit for Ensuring Network Infrastructure Security
This PPT Layout slide details the importance and benefits of conducting a firewall audit to ensure network infrastructure security. It breaks down the audit into four critical components:
- Network Security: Identifying vulnerabilities, detecting security gaps, and addressing misconfigurations within the firewall setup to safeguard the network.
- Risk Management: Aim to minimize the risk of data breaches by diligently monitoring firewall configurations and ensuring adherence to established security standards.
- Policy and Rules Optimization: Streamlining firewall rules by removing unused or redundant ones improves network performance and optimizes rule efficiency.
- Access Control Mechanism: Implementing mechanisms to provide network access only to authorized users and prevent unauthorized access attempts.
Download this template to highlight the tangible benefits of such an audit, which contribute to a more robust and efficient network security posture.
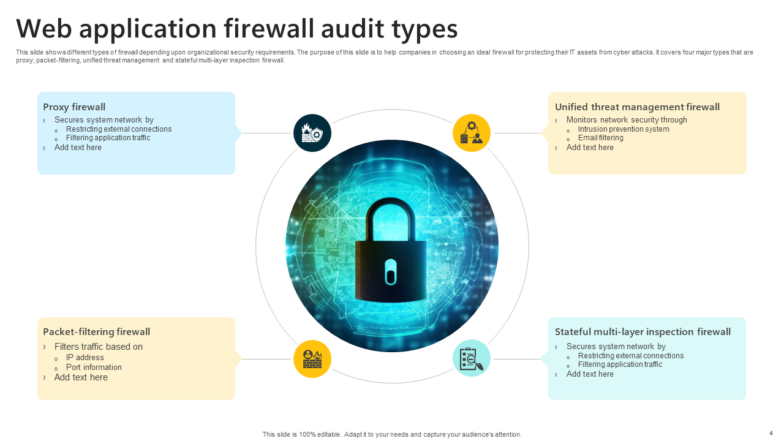
Template 4: Web Application Firewall Audit Types
Get an overview of different types of firewalls used for web application security, guiding organizations in selecting the appropriate firewall for their IT infrastructure with this PPT Preset:
- Proxy Firewall: It secures the network by restricting external connections and filtering application traffic.
- Packet-filtering Firewall: It filters traffic based on IP addresses and port information.
- Unified Threat Management Firewall: It monitors network security by integrating multiple security features.
- Stateful Multi-layer Inspection Firewall: It provides robust security by filtering traffic and keeping track of established connections.
The slide enables you to consider each firewall type's capabilities in relation to the organization's specific security needs. Get it now.
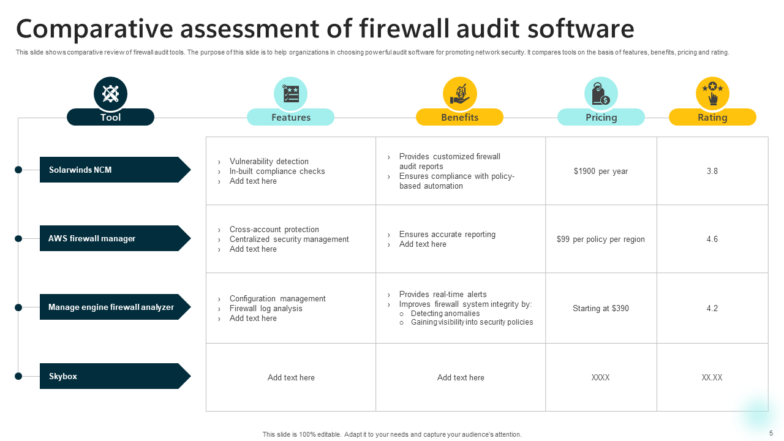
Template 5: Comparative Assessment of Firewall Audit Software
Deliver a comparative analysis of firewall audit software using this PPT Slide based on key attributes such as features, benefits, pricing, and user ratings:
SolarWinds NCM: Noted for its vulnerability detection and in-built compliance checks.
AWS Firewall Manager: Known for cross-account protection and centralized security management, ensuring accurate reporting.
ManageEngine Firewall Analyzer: Focuses on configuration management and firewall log analysis.
Download this template to evaluate which software aligns with their security needs and budget while considering user satisfaction and software effectiveness.
Template 6: Evaluating Security Capabilities for Firewall Auditing
The PPT Set showcases a circular flowchart detailing a systematic approach for evaluating security capabilities during firewall audits. It outlines a six-step cyclical process:
- Define assessment scope: Establish goals and standards to assess security and align with frameworks like COBIT and GDPR.
- Conduct security audit: Test and verify the effectiveness of security systems, controls, policies, and procedures.
- Implement changes: Address identified security gaps to enhance system protection.
- Evaluate risks: Identify and assess potential threats to the information system and determine mitigating actions.
- Analyze results: Compare risk analysis findings with organizational standards to pinpoint security gaps and understand security system integrity.
- Repeat cycle: Regularly reassess security to adjust policies based on environmental shifts or organizational needs.
Download this template to maintain a secure and reliable network infrastructure through continuous improvement and vigilant monitoring.
Template 7: Feature Comparison of Firewall Audit Tools
The slide features a table that includes real-time alerting, customized audit reports, policy compliance, risk assessment, and intrusion prevention capabilities. It also lists audit tools like Tufin, AlgoSec, SolarWinds, AWS Firewall Manager, and Titania Nipper, with checkmarks indicating the presence of a feature and crosses indicating its absence. This visual guide aids organizations in selecting the right tool that meets their specific security audit requirements. Grab it now.
Template 8: Firewall Audit Software Solutions for Security Compliance
This slide provides you with an overview of firewall audit software solutions aimed at enhancing security compliance. It emphasizes ensuring that network security aligns with organizational regulatory standards. The slide breaks down the solutions into three main components: Firewall rule analysis, Firewall configuration management, and Workflow automation. The layout delivers a streamlined, technology-driven approach to maintaining robust network security through meticulous analysis, management, and automation of firewall rules and policies. Download now.
Template 9: Prerequisites for Choosing Firewall Audit Tools
This slide outlines the essential considerations before selecting firewall audit tools for business IT security. It emphasizes four core areas: Security needs, Functionality, Scalability, and Cost structure. The evaluation begins with an understanding of the organization's security requirements. Next, ensure the chosen tool's functionality aligns with organizational security standards. Scalability is another critical factor, where the tool must meet growing network demands without frequent replacements. Lastly, the cost structure of the firewall audit tool is examined, including licensing, upfront costs, and ongoing maintenance expenses. Download the slide to prompt your business to weigh practical needs against financial implications to ensure a secure and efficient IT infrastructure.
Template 10: Firewall Audit Icon for Network Security
The slide presents an icon representing a firewall audit for network security. It's a visual aid designed to capture the audience's attention and emphasize the importance of cybersecurity audits. The image is accompanied by placeholders for text, suggesting that details or descriptions can be added. The slide underscores the critical role of firewall audits in protecting data and ensuring safe, secure network operations. Download this template now.
Walls that Bolster Cybersecurity
Use our Firewall Audit Templates to perform proper firewall inspections to ensure you don’t leave your customers’ valuable information vulnerable to data breaches.
Access these slides with a single click and streamline your cybersecurity auditing process more. You can choose one of our subscription services: monthly, semi-annual, annual, annual+ with a click here.
PS: The templates in this blog are not ranked in any particular order. Pick the one(s) you like and download it!





 Customer Reviews
Customer Reviews