In 2024, the average consumption of data has reached a magnitude of 748 exabytes per month. The reason behind this is the rise in the availability of internet, devices with better storage, cloud storage options, online streaming, and social media. With the rise in data consumption, malicious activities are also rising.
Data is considered as a new fuel of this generation and is quite valuable. Due to this, many hackers are becoming active. They steal your precious customer information and sell this data to third parties, startups or malicious marketing firms entering the similar industry.
With this changing environment and the rise in malicious activities over the internet, we all need to adapt and take security measures to protect our data. But how can we do this?
This is where data risk management comes into play. With data risk management, you can oversee the flow of your data within your firm or among your customers, and based on that, you can set policies and procedures to prevent data leaks.
With this blog, you’ll get to learn what data risk management is, data theft risk trends in different industries, data governance processes, and data risk mitigation strategies. Let’s dive in …
What is Data Risk Management?
Data risk management is basically a series of processes designed to govern, recognize, and mitigate the risks of data leaks. Without adopting data risk management strategies, a company is constantly at risk of data loss, intellectual property theft, data manipulation, and loss of its reputation among customers and shareholders. All of these factors can have a serious impact on your brand’s competitive standing and security.
A thoroughly designed data risk management plan outlines
- Stats on data breach probability,
- The budget required to implement a data risk management plan,
- Steps for risk assessment process,
- Data theft risk trends in your operating industry,
- Data governance processes, and
- Risk mitigation strategies
The plan also covers the procedures for properly storing, accessing, and changing datasets, methods for identifying and addressing vulnerabilities beforehand, and ways to minimize exposure when data is compromised.
Data risk management also involves comprehensive employee training to ensure that everyone in the organization knows how to prevent a data breach.
Now as you’ve got information about what data risk manage is and how important it is for an organization to implement it, its time to create one for yourself.
To help you with this, we have created a presentation module with customizable slides. All these slides provide you with a step-by-step process to create a data risk management plan. In these slides, we have covered some general information that is suitable for all types of organizations; however, feel free to customize anything that better suits your firm.
PowerPoint Slides for Creating Data Risk Management Plan
Let’s discuss a few important slides of the presentation to give you a basic idea of how a data risk management plan can be created in PowerPoint.
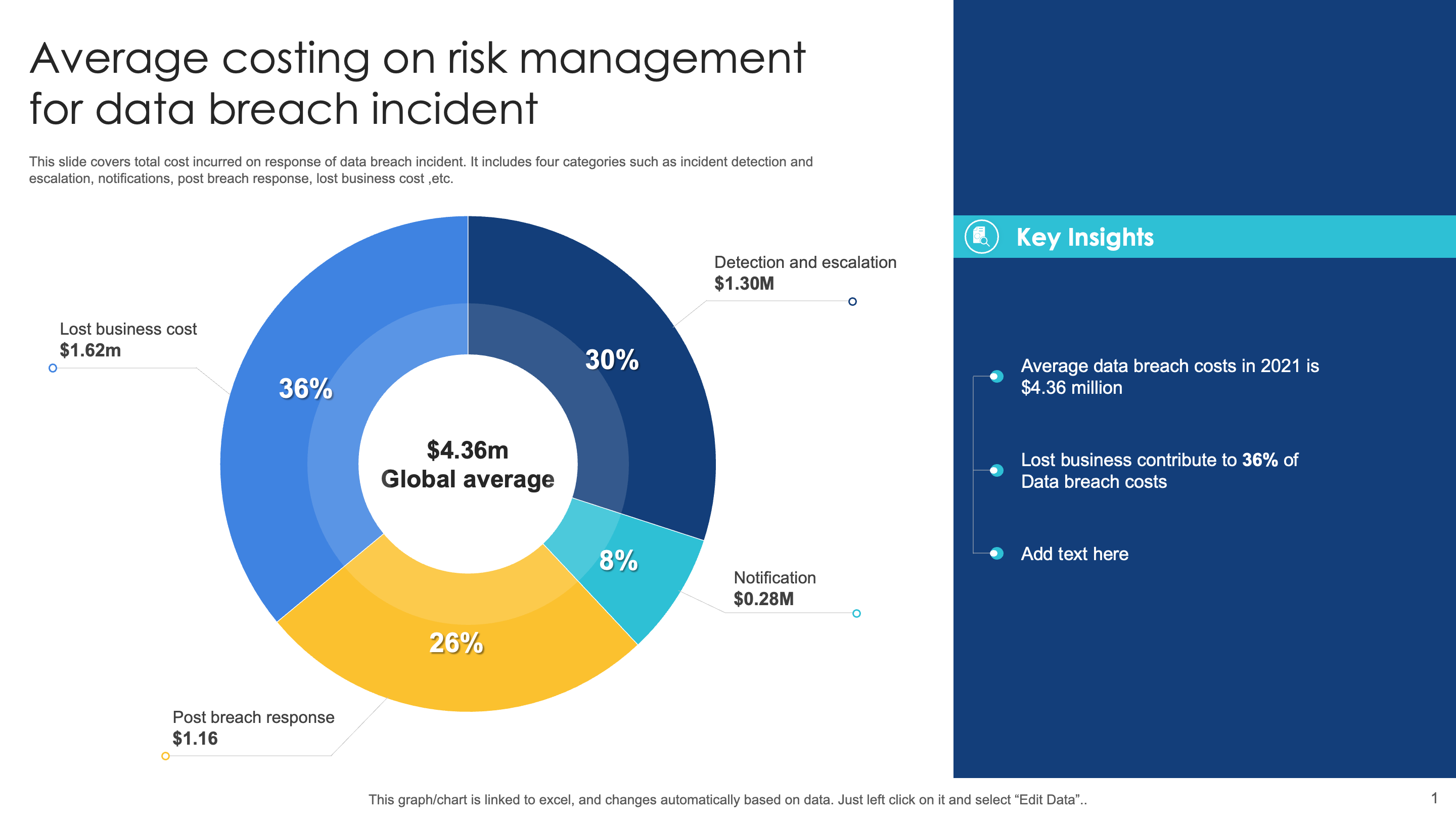
Slide 1: Average Costing on Risk Management for Data Breach Incident
This slide shows a pie chart depicting the average cost of risk management for data breach incidents. The pie chart breaks down the average costs incurred and categorizes them into four main areas:
- Lost business cost
- Detection and escalation
- Post-breach response
- Notification
Feel free to edit the pie chart or add more categories if required. On the right-hand side, we’ve also provided key highlights of the overall cost analytics. Use this section to summarize and provide notes on your statistical analysis.
By preparing a cost structure, you can accurately predict the expenses your company may incur in handling data breaches if an effective data risk management plan is not put in place.
Download this PowerPoint Template Now!
Slide 2: Data Breach Risk Stats on Social Media Platforms and Incident Sources
This slide shows risk stats of data breaches on social media platforms along with sources of such incidents. The data is presented in pie chart form with percentage and actual number of incidents
The first pie chart shows the division of data breach incidents based on the type of attack, including categories such as identity theft, account access, financial access, malicious insider, and unknown sources.
Next, we have another pie chart showing the sources of data breaches. The sources include malicious outsider, accidental loss, hacktivist, nuisance, and existential data.
Overall, with this template, you can highlight how social media platforms are vulnerable to various data breach attacks.
Download this PowerPoint Template Now!
Slide 3: Five Step Financial Data Risk Assessment Process
This slide shows a five-step process essential for financial data risk assessment. Follow these steps for a thorough assessment:
- The first step is to establish a framework for managing data security.
- Once you have a proper framework in place, the next step is to identify the specific data sets that need to be addressed
- Even after properly identifying the data sets that need governance, we must be prepared for the worst-case scenario. Therefore, this third step involves assessing financial liabilities that could arise due to data breaches.
- Next, based on the identification and financial liabilities calculated in the second and third steps, we need to prioritize data sets that require more focus.
- Lastly, the final step is to create a mitigation plan to address the identified risks and prepare a budget required to implement these measures.
Overall, this template gives you a general framework for creating a financial data risk assessment process. Customize the framework’s data as per your own requirements.
Download this PowerPoint Template Now!
Slide 4: Overview of Reported Data Theft Risk Trends in Health Care Sector
This slides displays an overview of data theft risk trends in healthcare sector. This is just to present you a structure how trends can be presented for a specific industry. Feel free to customize the template for any industry you are operating in.
This template presents information based on findings from data loss incidents within the healthcare and medical field. It covers top threat patterns such as hacking, human error, or privilege misuse. Additionally, the slide covers actor motives, including incidents where medical records are specifically targeted. Furthermore, there’s a pie chart showing statistics for data compromised. We have covered the loss of personal data and medical records. You can edit this pie chart in Excel to show relevant data. For example, firms operating in the financial industry can show credit card details and accounts compromised.
With this template, you can visually present data patterns, reasons behind data theft, and the percentage of data compromised, making it easier for the audience to grasp.
Download this PowerPoint Template Now!
Slide 5: Adoption of Big Data Analytics to Mitigate Compliance and Operational Risks
This slide shows a graph depicting compliance mitigation and improvements in operational risks with big data analytics. The x-axis presents various areas where big data analytics is used to manage risks, such as:
- Customer experience
- Risk management
- Target market
- Regulatory compliance
- New product development
- Cost reduction
- Process efficiency
- Developing information products
Furthermore, the y-axis represents the use of big data analytics in percentage. Lastly, a section is provided for key highlights to show widely adopted strategies and top areas where businesses leverage big data analytics.
Download this PowerPoint Template Now!
Slide 6: Four Steps of Cyber Security Data Breach Risk Process
This slide presents a four-stage illustration of the cyber security data breach risk process. The stages include:
- Probe: This stage involves identifying software with outdated security systems, password testing, and launch of phishing attacks
- Initial Attack: After identifying vulnerabilities, the attackers try to trick employees via emails or attempt to corrupt application programs.
- Expanded Attack: If the initial attack is successful, attackers will try to gain broader access by moving through connected networks to reach additional systems.
- Data Lift: Lastly, attackers will extract the targeted data from the compromised systems.
By identifying vulnerabilities with these steps, we can take proactive measures to address cybersecurity risks and reduce the chances of data breaches.
Download this PowerPoint Template Now!
Conclusion
Data breaches are a serious threat to any organization therefore Implementing a strong data risk management plan is crucial to protect your valuable information. In this blog, we have covered the importance of data risk management and discussed customizable PowerPoint templates that offer a foundational structure for creating your own plan.
The slides covered were just a few essential slides, however the complete module covers a step-by-step guide to create a data risk management plan and safeguard your data.
Our data risk PowerPoint PPT is exclusively available for our subscribers.
Subscription options:
- Monthly: $49.99 (10 downloads)
- Yearly: $249.99 (unlimited downloads)
Sign up today and gain access to a vast collection of professionally designed and 100% editable PowerPoint slides.



Frequently Asked Questions
Q: Why is it important for organizations to invest in a data risk management plan?
Answer: Data is increasingly valuable in today's digital age, and the consequences of a data breach can be severe, ranging from financial losses to reputational damage. A data risk management plan helps organizations identify and mitigate potential risks, safeguarding sensitive information, and protecting against data breaches. Investing in such a plan demonstrates a commitment to security and helps maintain trust with customers, partners, and stakeholders.
Q: How often should a data risk management plan be reviewed and updated?
Answer: A data risk management plan should be reviewed and updated regularly to adapt to evolving threats, technologies, and regulatory requirements. It's recommended to conduct comprehensive reviews at least annually or whenever significant changes occur within the organization, such as the introduction of new technologies, changes in business operations, or updates to data protection laws. Continuous monitoring and assessment are essential to ensure the effectiveness and relevance of the plan over time.
Q: What role do employees play in implementing a data risk management plan?
Answer: Employees are a critical component of effective data risk management. They are often the first line of defense against data breaches and security incidents. Employee training and awareness programs are essential for ensuring that everyone within the organization understands their role in protecting sensitive information, follows best practices for data security, and knows how to respond in the event of a security incident. By fostering a culture of security awareness and accountability, organizations can strengthen their overall security posture and mitigate the risk of data breaches.





 Customer Reviews
Customer Reviews